This article provides practical advice for Project Managers and IT Leaders on common mistakes when implementing passwordless authentication. I will provide strategies to avoid common traps, such as poor planning, lack of user training, and compatibility issues with existing systems. By recognizing these challenges, you can make the transition smoother and improve security and user experience.
How to avoid common pitfalls in passwordless authentication implementation
Passwordless authentication can significantly improve security and user experience, yet it has several challenges. While working with Inteca’s clients I spotted several routine mistakes.
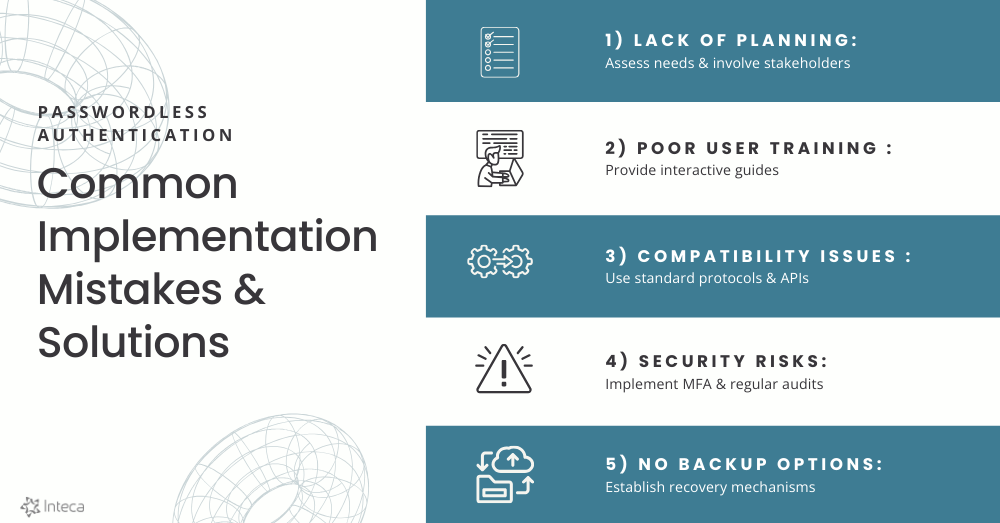
1. Lack of planning and assessment
A critical error many organizations make is rashly adopting passwordless solutions without a clear strategy. This rushed approach can result in a disconnect between the solutions implemented and the actual needs of the business and its users.
Actionable solution for this mistake – Before starting the implementation, assess your existing systems and understand user needs. Engage key stakeholders early in the process to ensure that the passwordless solution aligns with both organizational goals and user requirements. This step lays the groundwork for a smooth implementation.
2. Insufficient education and training
User education is essential. If end-users lack a clear understanding of passwordless methods, they might resist the changes due to confusion.
Actionable solution for this mistake – Provide comprehensive training sessions and develop easy-to-understand guides and resources. Interactive sessions combined with clear materials enhance learning outcomes. Utilizing video tutorials and interactive guides can make learning engaging and effective. It’s important for users to understand the advantages of the new authentication methods, which will help them adapt and use the system comfortably.
3. Ignoring compatibility issues
A frequent mistake is not assessing how passwordless solutions integrate with current systems and applications. Such incompatibility can lead to significant operational challenges.
Actionable solution for this mistake – Prioritize compatibility assessments to ensure seamless integration with current IT infrastructure. Using standard protocols and APIs will simplify integration and minimize disruptions. This proactive step can prevent potential headaches down the line.
4. Overlooking security risks
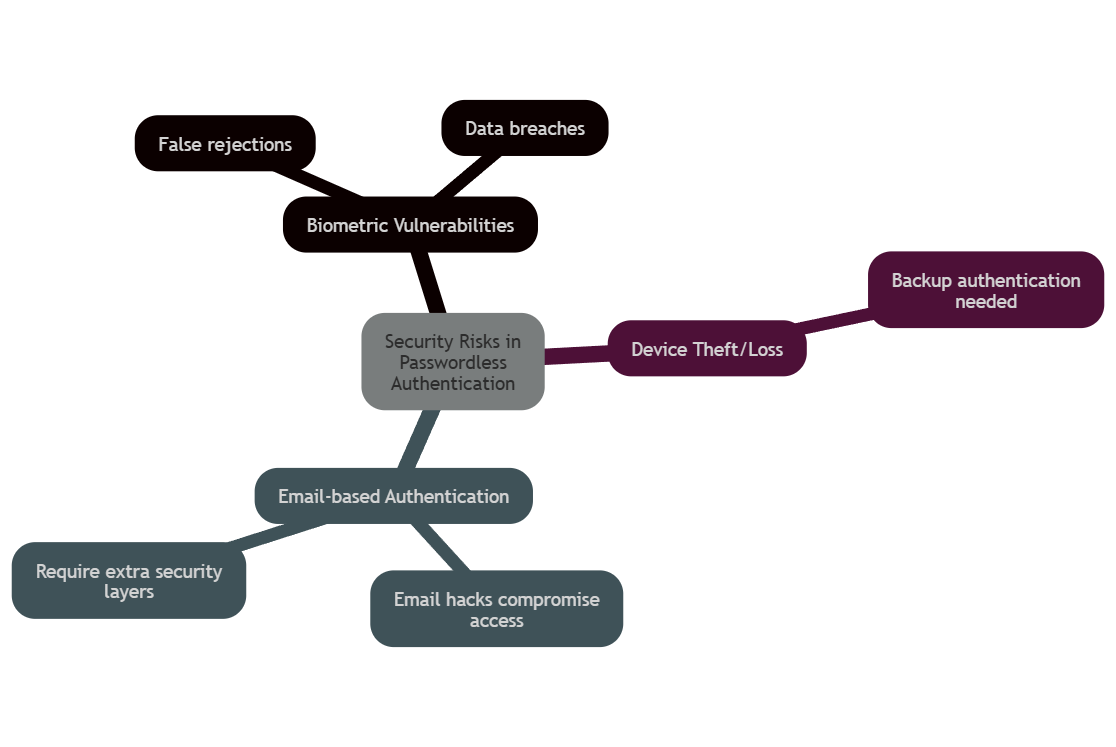
Although passwordless authentication improves security, it does introduce certain vulnerabilities like biometric vulnerabilities, device theft or loss considerations, or low user trust in logging without a password . Organizations mustn’t overlook potential risks.
Actionable solution for this mistake – Identify these risks early on and implement robust security measures. Use strong encryption methods and perform regular security audits. Using multi-factor authentication (MFA) strengthens security and helps protect your organization from vulnerabilities.
5. Neglecting backup and recovery options
In my work, I’ve seen the chaos that ensues when a system fails or a user gets locked out without a backup method in place.
Actionable solution for this mistake – Establish clear recovery processes to help users regain access without compromising security. It’s also wise to test these processes regularly to ensure they work effectively when needed.
6. Insufficient communication and change management
Poor communication about the transition to passwordless authentication can lead to confusion among users.
Actionable solution for this mistake – Implement a comprehensive change management strategy that involves all stakeholders. Regular updates and feedback sessions can ease the transition and promote acceptance among users.
7. Challenges in user adoption
Users often hesitate to adopt new technologies due to fear of change. Especially when it comes to cybersecurity. No-password authentication may seem weak, and potentially harmful for some of users.
Actionable solution for this mistake – Engage users early in the process. Address their concerns openly and highlight the benefits of passwordless solutions to foster a positive attitude towards the new system.
8. Over-reliance on Technology
There’s a misconception that simply implementing passwordless authentication will solve all security issues. Cybersecurity is a complex term, hence one solution will not solve all of the potential vulnerabilities.
Actionable solution for this mistake – Maintain a holistic approach to security that includes policies, procedures, and ongoing user education. Regularly reviewing security practices will keep organizations prepared for evolving threats.
9. Inadequate testing and evaluation
Finally, organizations sometimes skip thorough testing, leading to significant problems post-deployment.
Actionable solution for this mistake – Conduct extensive testing before full deployment and schedule regular evaluations to refine the approach and address any emerging challenges.
**Bonus** challenges with some passwordless authentication methods
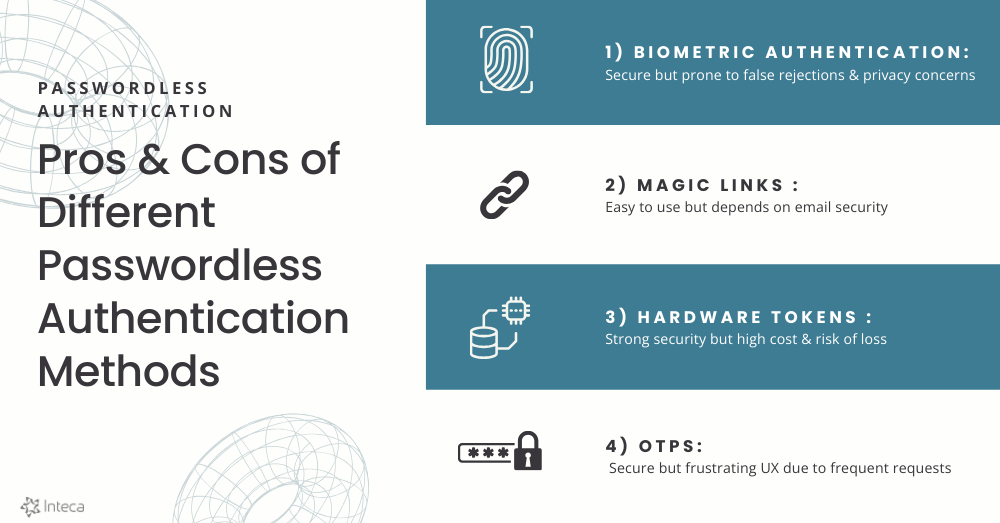
1. Biometric authentication
Biometric authentication, such as using fingerprints or facial recognition, enhances security but also raises significant privacy concerns.
Here are a couple of challenges:
- False Rejection Rates (FRR) – variations in biometric readings can lead to users being denied access due to environmental factors or even changes in their appearance.
- Data security – protecting biometric data is essential because a breach can lead to identity theft, which is difficult to rectify.
2. Hardware security tokens
Although hardware tokens like YubiKeys provide strong security, they come with their own challenges:
- Physical dependency – users need to carry their tokens, and misplacing one can prevent access to important systems.
- Cost and management – the initial investment and the ongoing management of these tokens can be quite resource-intensive for organizations.
3. Magic Links
Magic links simplify the login process, but they do have some drawbacks:
- Email security – if someone compromises an email account, hackers can access the system without a password.
- User reliance on email access – users need reliable access to their email accounts, which can be an issue if they forget their credentials or lose access.
4. One-Time Passwords (OTPs)
While OTPs enhance security, they also present some challenges:
- Delivery Issues – users might not receive OTPs because of network issues or incorrect phone numbers.
- User experience – frequent OTP requests can annoy users and make them hesitant to use this method.
5. Passkeys
Passkeys represent a new approach to passwordless authentication, but they also come with challenges:
- Device compatibility – not all devices support passkeys, making account access difficult for users on different platforms.
- User education – users may need some training to effectively create and manage their passkeys.
Remember about user experience and accessibility
User experience (UX) plays a crucial role in effectively implementing passwordless authentication systems. An easy-to-use UX enhances user satisfaction and encourages more people to adopt the technology. In passwordless systems, we aim to streamline the authentication process while maintaining security. Let’s explore some important aspects to consider:
User experience in passwordless systems
- Simplicity is key – methods like biometric authentication or magic links should be user-friendly. If the process is too complex, users may be reluctant to embrace these new technologies.
- Feedback mechanisms – immediate feedback during authentication helps users feel in control, informing them of their success or any issues.
Accessibility in authentication
- Inclusive design – it’s essential to design passwordless systems that accommodate all users, particularly those with disabilities. This could involve incorporating voice recognition or other methods for individuals with physical limitations.
- Clear instructions – Simple, straightforward instructions greatly enhance accessibility. For instance, users with cognitive disabilities gain from clear language and visual aids that help them navigate the process.
Cost and scalability considerations
Implementing passwordless authentication requires careful consideration of the cost implications that come along with it. The initial expenses can be significant, particularly due to hardware, software, and user education costs. Here are some important aspects to keep in mind:
1. Cost of implementation
- Hardware and software – depending on which passwordless method you choose, you might need to invest in biometric scanners, security tokens, or specific authentication platforms. Costs can vary greatly depending on the scale of your deployment and the chosen technologies.
- Training and support – educating staff and users about the new system is vital for successful implementation. Make sure to set aside part of your budget for training sessions and ongoing support, as this will facilitate smoother adoption and help alleviate any resistance.
2. Scalability of passwordless solutions
As organizations grow, ensuring scalability becomes a priority. Passwordless solutions need to be adaptable enough to manage a growing number of users and changing security demands. Here are some points to consider:
- Integration with existing systems – it’s essential that your passwordless solution integrates smoothly with your existing IT infrastructure. This minimizes the risk of costly overhauls down the line.
- Future-proofing – look for solutions that can evolve with emerging technology without requiring hefty additional investments.
Key takeaways
Transitioning to passwordless authentication offers organizations significant benefits, but avoiding common pitfalls is essential for success. Here are the key takeaways from my experience:
- A strong strategy includes assessing current systems and understanding user needs, which helps align authentication solutions with business objectives.
- Investing in effective training and clear communication will help users adapt to new technologies and reduce resistance.
- Implementing robust security measures and ensuring compatibility with current infrastructure can prevent future operational challenges.
- Conducting regular testing, creating backup options, and focusing on inclusivity can greatly improve security and the overall user experience.
Following these insights will help you enhance the deployment of passwordless authentication, resulting in a secure and user-friendly environment.
Learn how eliminating passwords can improve security and cut costs!