SkyCloak Alternative for IAM: Keycloak Hosting Compared to Inteca
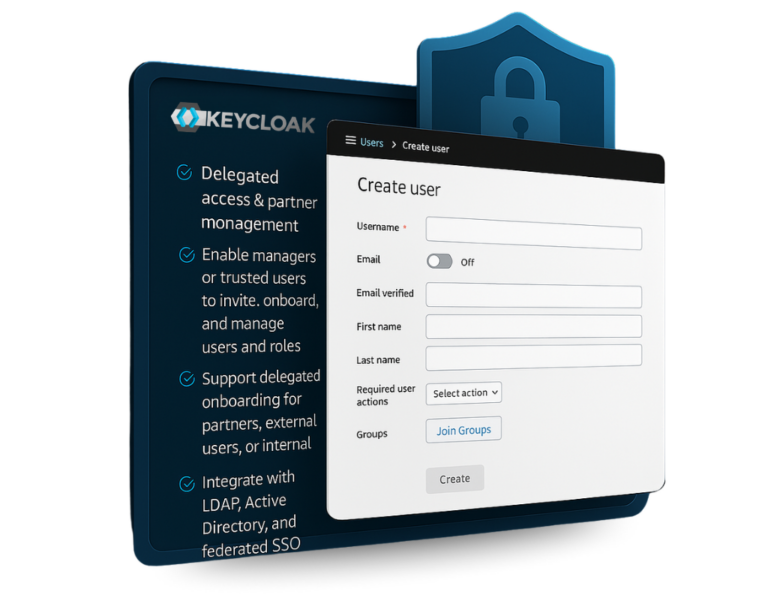
Introduction: Why look beyond SkyCloak for IAM hosting? SkyCloak is one of several managed Keycloak providers offering hosted identity and access management (IAM) solutions with simple MAU-based pricing and support tiers. While it’s a solid option for startups and early-stage projects, scaling enterprises and regulated organizations often require more robust security measures, granular user access…