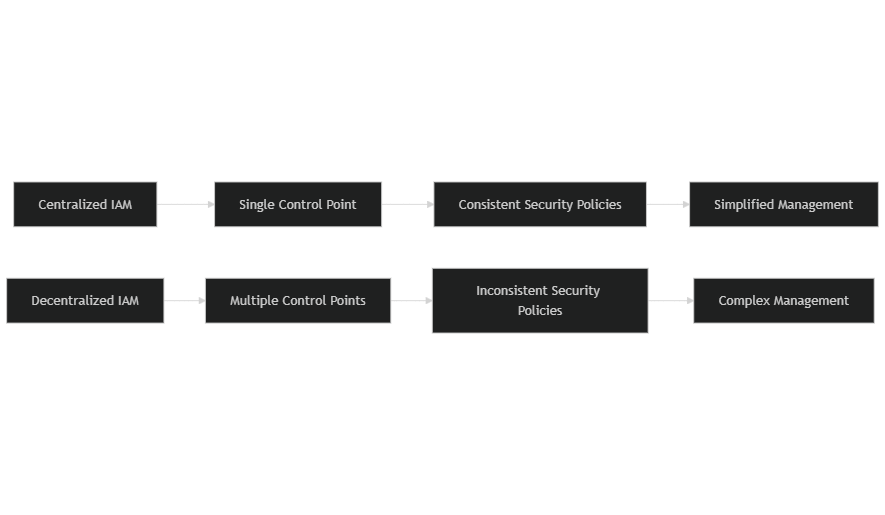
Centralized Identity and Access Management (IAM) is a critical strategy in today’s environment of frequent data breaches and cyber threats, particularly when considering decentralized access control options. A centralized system for managing user identities and permissions allows organizations to apply security policies consistently, enhancing overall security and efficiency.
A centralized access directory enables robust security measures like multi-factor authentication (MFA) and role-based access control (RBAC), simplifying user management and allowing IT teams to focus on strategic tasks. Additionally, automating identity processes and providing real-time access insights help organizations swiftly address risks and meet compliance requirements.
Benefits of centralized IAM approach
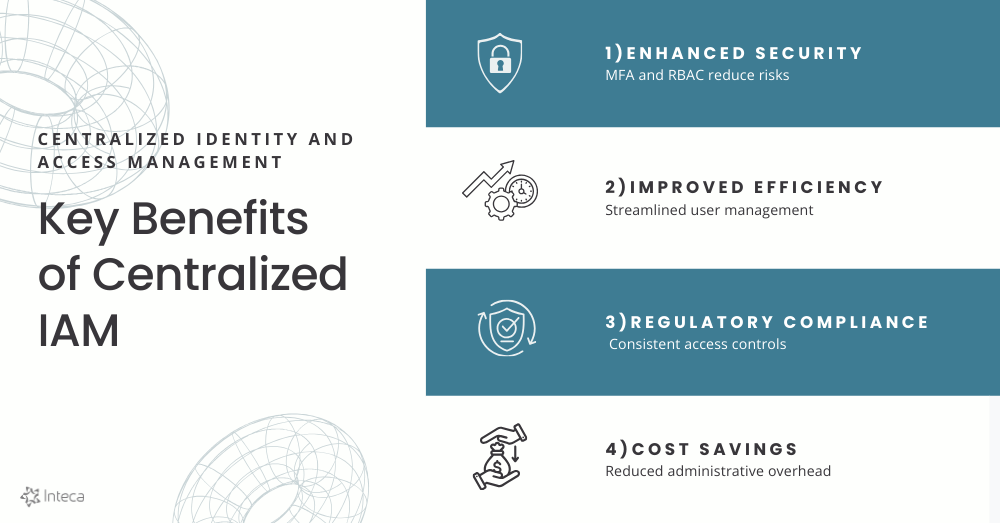
Enhanced security through unified access controls
A major benefit of a centralized IAM system is improved security through unified access controls, which effectively manage access across the organization. Centralized IAM improves security by unifying access controls. It enables organizations to implement MFA and RBAC effectively, minimizing the risk of unauthorized access. For example, an Inteca case study involving a prominent European Economic Information Bureau demonstrated how a tailored cybersecurity solution federated user authentication with multiple European banks, significantly improving authentication service uptime. This underscores the reliability of centralized systems in maintaining security.
Improved efficiency in user management and provisioning
Another significant advantage of centralized IAM is the streamlined user management and provisioning it offers. A recent report highlighted that 80% of enterprise SaaS logins are invisible to IT and security teams due to the use of personal credentials or non-SSO-backed corporate accounts1. A centralized IAM system provides visibility into user access, enabling smoother onboarding processes and reducing IT workload.
Streamlined compliance with regulatory standards
Centralized IAM simplifies compliance management by ensuring consistent application of access controls. AI-driven governance frameworks help organizations manage compliance and risk management processes more effectively. Many organizations report a reduction in compliance-related incidents after adopting centralized IAM, allowing them to focus on core business activities.
Cost savings through reduced administrative overhead
Finally, centralized IAM offers significant financial benefits, especially when compared to decentralized access control systems. By reducing administrative overhead in identity management, organizations can achieve substantial savings. Automating identity processes reduces manual tasks, minimizes errors, and increases productivity. Many organizations that embraced centralized IAM solutions reported lower IT support costs and better resource allocation, ultimately leading to a healthier financial outlook.
Challenges in implementing centralized iam
Implementing a centralized Identity and Access Management (IAM) system can significantly improve both security measures and operational effectiveness. However, my experience with different organizations reveals several challenges that must be addressed. This section will discuss essential challenges such as scalability, integration, and the technical complexities involved in implementation.
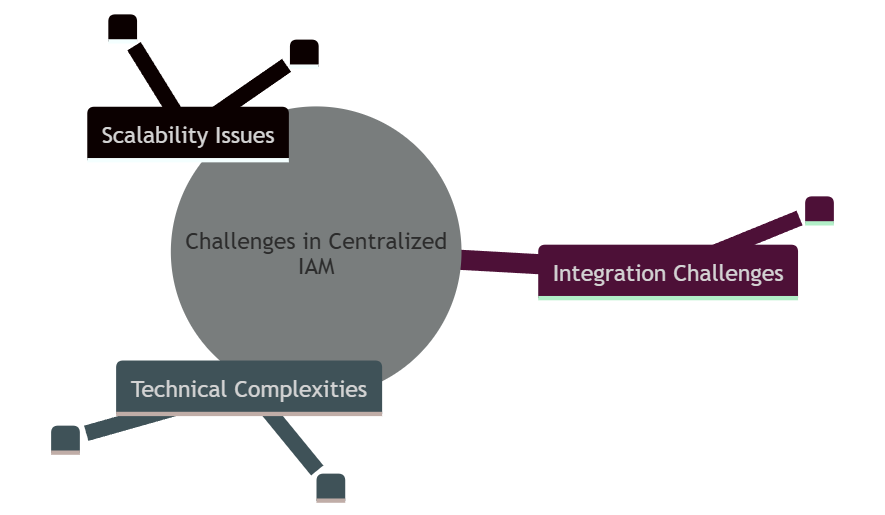
Scalability issues
As organizations develop, their requirements for identity management become increasingly complex. Scalability is a fundamental challenge when adopting centralized IAM solutions. Many organizations struggle with:
- Addressing scalability in growing organizations: Traditional IAM systems often struggle to keep pace as user numbers and applications multiply. This can lead to performance bottlenecks, ultimately frustrating users and IT teams alike.
- Future-proofing iam solutions: Organizations must ensure their IAM systems are adaptable to evolving requirements, including the integration of new technologies and management of a growing number of users. As organizations adopt increasingly complex identity management systems, they encounter scalability challenges that demand AI-driven solutions.
Integration challenges
Integrating centralized IAM with existing systems and applications presents significant challenges. Key integration challenges include:
- Integrating new applications with existing systems: Organizations often struggle to connect new applications to their centralized IAM framework. This can lead to fragmented identity management processes and decreased efficiency, particularly in environments lacking a centralized access point.
- Inteca case study: A progressive European bank demonstrates how tackling these hurdles can yield benefits—by successfully integrating a zero-trust security framework, they significantly improved user authentication during loan selling processes while ensuring secure communication with external payment institutions.
Technical complexities
The technical intricacies involved in IAM integration can pose substantial hurdles:
- Managing the intricacies of IAM integration: Organizations must address numerous technical challenges, including data migration, system compatibility, and user lifecycle management, which can be difficult to manage.
- Insight: Integrating biometric methods with contextual access control is becoming more common, enhancing security through additional verification measures.⁵ Grasping these technical complexities is crucial for successful IAM implementation.
| Challenge | Description | Potential solutions |
|---|---|---|
| Scalability issues | Difficulty in accommodating growth and complexity in user management. | AI-driven solutions and cloud scalability. |
| Integration challenges | Issues with connecting new applications to existing IAM systems. | Comprehensive integration strategies. |
| Technical complexities | Navigating the intricacies of IAM integration and user lifecycle management. | Employing skilled IT teams and consultants. |
Key takeaways
Based on various implementations of centralized Identity and Access Management (IAM), here are several key takeaways that organizations should consider.
Summary of benefits
- Enhanced security: Centralized IAM improves security by unifying access controls, reducing the risk of unauthorized access.
- Improved efficiency: Streamlined user management reduces IT workload and enhances operational efficiency.
- Cost savings: Automation minimizes administrative costs and improves resource allocation.
- Regulatory compliance: Consistently applied access controls simplify compliance and facilitate audits.
Reference List:
- CSO Online, https://www.csoonline.com/article/3836917/cisos-should-address-identity-management-as-fast-as-they-can-says-crowdstrike-exec.html
See why Keycloak may be the best choice for your centralized login needs!