I’ve noticed that organizations using decentralized IAM systems often struggle with complexity, which is why centralized identity management is a solution for this challenge. Organizations face various challenges, including user provisioning, security gaps, compliance issues, and high management overhead. That’s why centralized identity management is so important, as it ensures that users have appropriate access across all platforms.
Decentralized vs. centralized identity management systems
The table below outlines key features of Decentralized and Centralized IAM systems, highlighting the benefits of a centralized system.
| Feature | Decentralized IAM | Centralized IAM |
|---|---|---|
| User provisioning | Managing users can be intricate and lengthy in decentralized setups | Typically straightforward and efficient with unified processes, centralized access management ensures better security and user provisioning. |
| Security | Inconsistent policies heighten risks, particularly when managing access across different identity providers. | Consistent security measures significantly lower vulnerabilities |
| Compliance | Frequently poses challenges due to data silos | Centralized auditing and reporting streamline compliance efforts |
| Management overhead | Often high because of the number of systems involved | Usually minimized through a single management approach, centralized access management reduces complexity and enhances security. |
The LayerX “2025 Identity Security Report” reveals that 80% of enterprise SaaS logins happen without IT’s awareness, highlighting the need for a centralized strategy to enhance visibility and security1 . Decentralized systems complicate identity governance, which makes it more difficult for IT teams to track and manage access effectively. This comparison reveals a significant trend: many organizations are choosing Centralized IAM solutions to address these issues decisively.
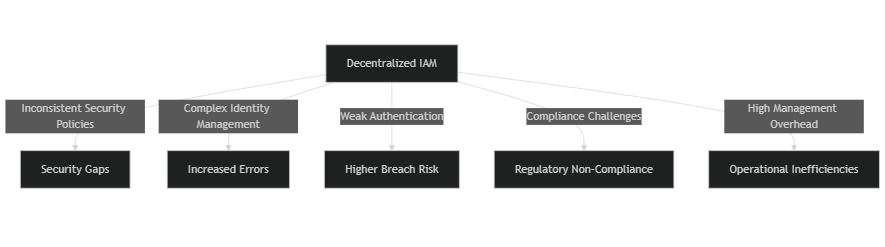
Vulnerabilities of dispersed IAM systems
Having collaborated with various clients on identity and access management (IAM) projects, I’ve noted that decentralized IAM systems pose specific vulnerabilities that significantly affect security and operational efficiency. Here’s a closer look at the key issues:
1. Inconsistent security policies
One major issue with decentralized IAM systems is the lack of a consistent security framework across different platforms, which complicates the management of user access points. Each system often adopts its own security protocols, leading to inconsistent policies. This fragmentation leads to security gaps, making it easier for unauthorized users to exploit weaker measures in some systems, emphasizing the need for fine-grained access controls.
2. Complex user identity management
Managing user identities across several isolated platforms complicates the identity and access management pattern and takes a lot of time. User provisioning is a challenging task, as clients frequently struggle to manage access rights and roles across many systems, particularly when dealing with external identity providers. This complexity can easily result in errors, such as granting excessive permissions or neglecting to revoke access when it’s no longer appropriate, amplifying security risks and complicating the management of user access.
3. Weak authentication mechanisms
Weak authentication mechanisms are frequently found in many decentralized IAM setups. A single vulnerable point can lead to a catastrophic data breach. For instance, if one system employs lax password policies while another mandates multi-factor authentication, the overall security posture is compromised, making it easier for unauthorized users to gain access.
4. Compliance challenges
Ensuring compliance with data privacy regulations is especially challenging in a fragmented IAM environment, particularly when using multiple identity providers. Organizations often struggle to maintain uniform access controls and comprehensive audit trails across disparate systems. The absence of centralized oversight significantly heightens the risk of non-compliance, exposing organizations to legal and financial repercussions.
5. Increased management overhead
The many systems within a decentralized IAM framework result in increased management burdens, complicating the access permissions process. IT teams are often stretched thin, requiring additional resources to monitor, maintain, and secure each individual system, which complicates managing user identities and access. This not only raises operational costs but also takes IT professionals’ attention away from important projects that could benefit the organization, making centralized user management even more critical.
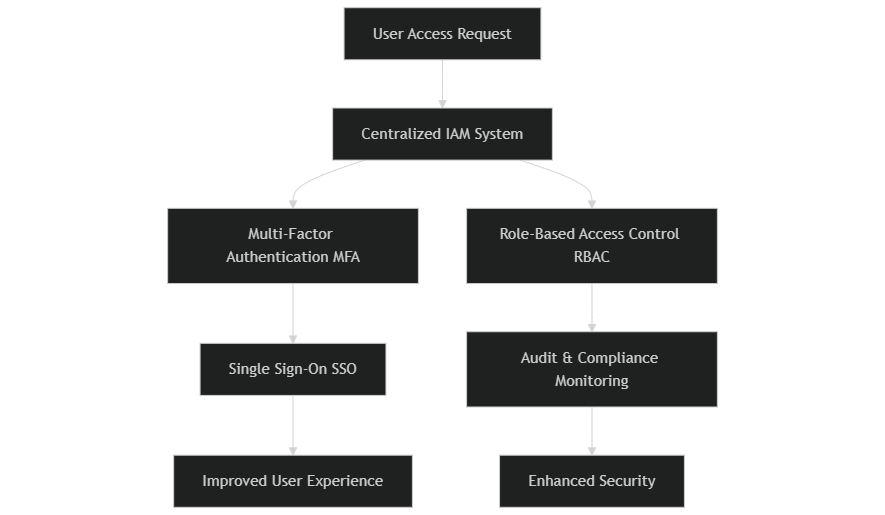
What do you gain from a centralized IAM solution?
It’s become clear that Centralized IAM systems are not just a smart choice; they’re a game-changer. Consolidating identity management into a single framework allows organizations to address the challenges of decentralized systems, leading to improved security and smoother operations.
1. Simplified management
A key advantage of Centralized IAM is how it simplifies user identity management. Centralized IAM allows IT teams to manage user lifecycles effectively, simplifying the processes of provisioning, modifying, and revoking access. This efficient approach decreases the administrative burden of management tasks, enabling IT professionals to concentrate on strategic initiatives instead of repetitive tasks.
2. Enhanced security
Centralized IAM provides a strong security framework that enables organizations to implement uniform security policies. By incorporating stringent authentication methods like Multi-Factor Authentication (MFA) and role-based access control (RBAC), organizations can drastically minimize their attack surface. Additionally, centralized monitoring allows for real-time visibility into access patterns, facilitating faster responses to potential security threats across the centralized system.
3. Improved user experience with single sign-on (SSO)
The incorporation of Single Sign-On (SSO) capabilities within Centralized IAM solutions is another significant benefit. Users can access multiple applications with a single set of credentials. This not only simplifies the user experience by reducing the need to remember multiple passwords, but it also enhances security by minimizing the risk of password-related breaches. Users enjoy a seamless journey with access to multiple platforms without sacrificing safety.
4. Streamlined compliance
Compliance is a significant concern for organizations, and Centralized IAM effectively addresses this issue. It provides essential tools for thorough auditing and reporting, ensuring uniform enforcement of access controls throughout the organization. With a centralized view of user access and activity, demonstrating compliance with regulations becomes far simpler, greatly reducing the risks of penalties and protecting organizational reputation.
By adopting a Centralized IAM solution, organizations can effectively tackle the challenges of decentralized systems and improve their operational efficiency.
Key takeaways
Based on my experience with clients in identity and access management, decentralized IAM environments pose significant challenges for IT teams. Several critical issues arise:
- Managing identities across different platforms can be time-consuming and inefficient, but centralized access management streamlines this process.
- Security gaps are more prevalent in decentralized IAM systems, increasing the need for a centralized identity and access management approach to enforce access effectively. Inconsistent policies introduce vulnerabilities that raise the chances of unauthorized access and data breaches.
- Adhering to data privacy regulations becomes challenging due to fragmented access controls across various systems, underscoring the importance of centralized identity management.
- Administrative demands increase, often necessitating additional resources and specialized expertise.
Moving to a centralized IAM solution can tackle these challenges effectively. It streamlines user management and enhances security with consistent protocols. Furthermore, it improves user experience through Single Sign-On (SSO) and simplifies compliance efforts.
1. The Hidden Dangers Of Shadow Identities And AI-Driven Security Gaps – Forbes – https://www.forbes.com/sites/tonybradley/2025/02/06/the-hidden-dangers-of-shadow-identities-and-ai-driven-security-gaps/
See why Keycloak may be the best choice for your centralized IAM system!