Enterprise Single Sign-On (SSO) is a transformative solution for organizations aiming to enhance security and streamline user accessThese tools provide insights into user access patterns, identify anomalies, and facilitate the enforcement of access policies, particularly for usernames and passwords. By allowing users to log in once and access multiple applications seamlessly, SSO reduces password fatigue and strengthens security. With businesses increasingly relying on cloud services and mobile technology, managing user identity securely has become a top priority.
This guide explores the importance of SSO, key concepts, implementation strategies, security enhancements, and emerging trends to help IT leaders make informed decisions.
Why do enterprises need SSO?
As more businesses embrace cloud services and mobile technology, the shift towards these innovations introduces significant challenges in user identity management, requiring robust solutions to ensure security. Relying solely on traditional password systems to protect against cyber threats simply doesn’t suffice anymore. Here are several key reasons why SSO has become indispensable in contemporary IT environments:
| What is the primary benefit of SSO? | Description |
|---|---|
| Enhanced security | Minimizes vulnerabilities by reducing password fatigue and the risks associated with weak password practices. |
| Improved user experience | Allows users to log in once and smoothly navigate across all necessary applications without hassle. |
| Operational efficiency | It cuts down on the time spent addressing password resets and login-related support queries. |
| Compliance and audit readiness | Simplifies tracking user access across systems, which is vital for complying with regulations. |
Implementing SSO not only strengthens security but also improves user productivity by streamlining authentication processes. As part of a broader Zero Trust strategy, SSO ensures that access to enterprise assets is continuously verified while enhancing the user experience. Organizations adopting SSO must also invest in user education and awareness programs to maximize security benefits and minimize potential vulnerabilities.
The rapid evolution of business needs and technological advancements continues to shape SSO solutions, driving innovations that focus on enhanced security, improved user satisfaction, and increased operational efficiency.

99% of organizations
rely on identity-related security solutions like SSO to mitigate credential-based attacks
Understanding SSO concepts
Understanding the significance of Single Sign-On (SSO) begins with a deep dive into its foundational concepts. Let’s examine key components such as Identity Providers (IdP), Service Providers (SP), their trust relationship, and the protocols ensuring secure authentication.
What is single sign-on (SSO)?
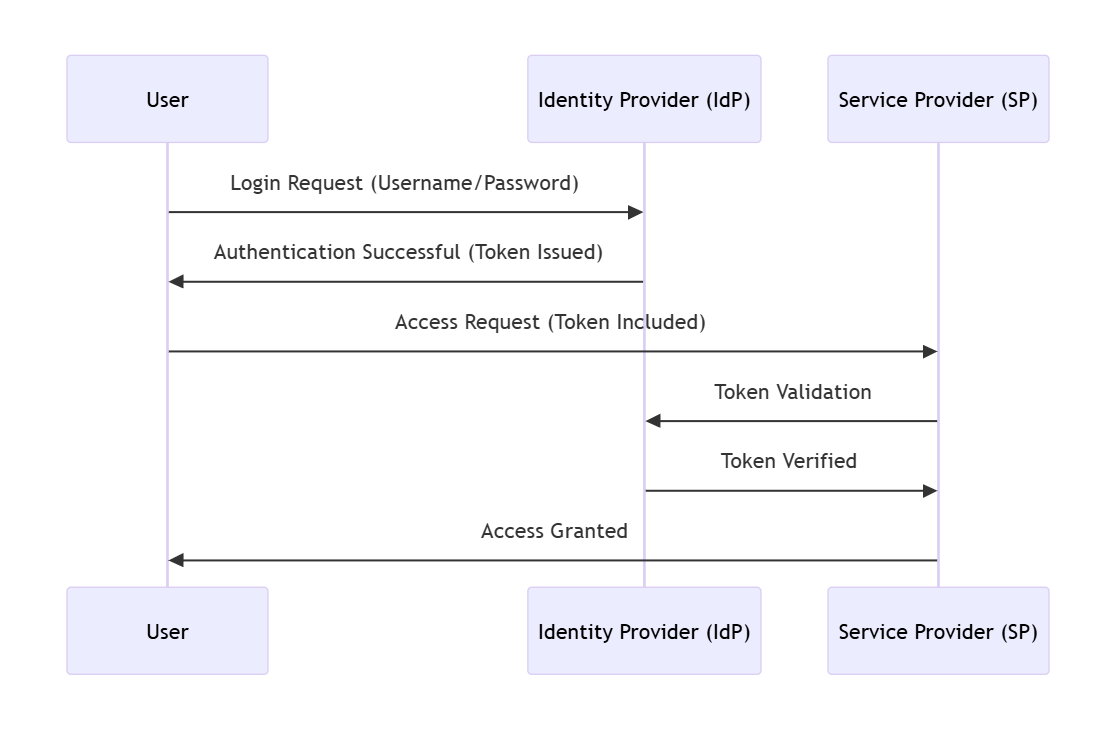
Enterprise SSO enables users to authenticate once per session and gain access to multiple applications without re-entering credentials. This eliminates password sprawl and centralizes authentication, creating a uniform security model across cloud and on-premises environments.
How does single sign-on work?
An effective SSO system relies on a strong identity management framework. Here are the essential components:
– Identity provider (IdP): This entity authenticates users and provides their identity information to service providers.
– Service provider (SP): The application or service that users want to access, which relies on the IdP for user authentication.
– Trust relationship: This involves a mutual agreement between the IdP and SP to securely share identity information.
– Identity federation: This links user identities across different domains, paving the way for seamless resource access.
– Credential management: A systematic approach ensuring user credentials are securely stored and managed.
– Digital gatekeeper: The IdP ensures that users are verified before granting application access, acting as a security checkpoint.
– Cross-domain access: Description of how Microsoft Entra ID can simplify management and enhance compliance.
IdPs serve as the central authority in an SSO environment, issuing authentication tokens that validate user identities across various applications managed by SPs. These interactions are governed by secure authentication protocols, ensuring seamless and safe access to enterprise resources.
Identity federation & trust mechanisms in SSO
A trust relationship is fundamental to the security and functionality of Single Sign-On (SSO). It enables secure authentication between Identity Providers (IdPs) and Service Providers (SPs) by establishing a trusted connection through authentication protocols, cryptographic certificates, and identity federation frameworks.
What is Identity Federation?
Identity Federation allows users to access multiple applications across different organizations, cloud environments, or business entities using a single set of credentials. Instead of maintaining separate accounts for different services, users authenticate once via an IdP, which then verifies their identity across various SPs.
Example: A user logged into their corporate account can seamlessly access third-party business applications (e.g., Microsoft 365, Salesforce) without additional logins.
How trust relationships work in SSO?
Trust relationships between IdPs and SPs ensure mutual recognition and secure authentication. The process involves:
- Identity Validation: The IdP authenticates the user and issues a secure authentication token.
- Token Exchange: The IdP sends a signed security assertion (via SAML, OAuth 2.0, or OpenID Connect) to the SP.
- Authorization Grant: The SP verifies the token, confirms the trust relationship, and grants access.
Key Mechanisms for establishing trust
| Mechanism | Description |
|---|---|
| Cryptographic Certificates | IdPs and SPs exchange digital certificates to encrypt and sign authentication requests. |
| Federated Identity Standards | Standards like SAML, OAuth 2.0, and OpenID Connect govern how authentication data is exchanged. |
| Policy-Based Trust Controls | Organizations define trust policies, such as access conditions, user roles, and risk-based authentication. |
Why strong trust relationships matter?
A well-defined trust relationship ensures that authentication requests are legitimate and prevents security threats such as:
- Man-in-the-middle attacks (intercepted authentication tokens)
- Unauthorized access due to weak validation mechanisms
- Identity spoofing (fake IdPs attempting to issue access tokens)
By implementing strong identity federation mechanisms and trust policies, enterprises can enable seamless cross-platform authentication while maintaining security and compliance.
What authentication protocols are used in SSO?
Using secure authentication protocols is vital for protecting user identities. Here are some of the most widely accepted ones:
| Protocol | Description | Use cases |
|---|---|---|
| SAML (Security Assertion Markup Language) | An XML-based standard that facilitates the secure exchange of authentication and authorization data between Identity Providers (IdPs) and Service Providers (SPs). | Ideal for enterprise applications and federated identity environments. |
| OAuth 2.0 | An authorization framework that allows third-party applications to request limited access to user accounts without handling login credentials. OAuth 2.0 itself does not authenticate users. | Commonly used for API access, mobile applications, and delegated authorization. |
| OpenID Connect | A layer built on top of OAuth 2.0 that adds authentication capabilities by allowing applications | Well-suited for web and mobile applications. |
These protocols enable interoperability across different platforms, securing authentication processes in enterprise environments.
What is SAML and how does It enable SSO?
Security Assertion Markup Language (SAML) is a widely used authentication and authorization standard that allows IdPs to securely transmit user credentials to SPs using XML-based assertions.
Key benefits of SAML in SSO:
- Seamless authentication across multiple enterprise applications.
- Stronger security by eliminating direct credential storage on SPs.
- Widely adopted in enterprise SSO deployments, particularly for legacy applications.
SAML is particularly beneficial in federated identity environments, where users need to authenticate once and gain access to multiple applications across different organizations.
What is OAuth 2.0 and how does it differ from SAML?
OAuth 2.0 is an authorization protocol, not an authentication mechanism. It allows third-party applications to request access to user data without requiring the user’s password. OAuth 2.0 is commonly used for:
- Granting limited access to APIs and cloud services.
- Enabling third-party applications to access user data without storing credentials.
How does OAuth 2.0 works?:
- The user grants permission to a third-party app to access their data.
- The OAuth authorization server issues an access token.
- The third-party app uses this token to retrieve user data without logging in as the user.
Example: When you sign into a third-party app using your Google account, OAuth 2.0 is used to authorize the app to access your Google Calendar without sharing your actual Google credentials.
Limitations of OAuth 2.0:
- It does not authenticate users or verify identities.
- Applications relying only on OAuth cannot confirm who the user is—just that they have access.
What is OpenID connect and how does it work with OAuth 2.0?
OpenID Connect (OIDC) extends OAuth 2.0 by adding identity authentication. While OAuth 2.0 provides authorization, OIDC ensures that an application can verify a user’s identity securely.
How does OpenID Connect work?:
- The user logs into an Identity Provider (IdP) (e.g., Google, Microsoft Azure AD).
- The IdP issues an ID token (alongside an OAuth 2.0 access token).
- The application validates the ID token to confirm the user’s identity.
Benefits of OpenID Connect in SSO:
- Simplifies authentication for web and mobile applications.
- Provides user profile information, unlike OAuth 2.0 alone.
- Works seamlessly with existing OAuth infrastructure.
Example: When a user logs into a web app using Google Login, OpenID Connect verifies the user’s identity before granting access.
What are the risks of single sign-on?
While SSO simplifies authentication, it also introduces certain security risks For example, training users to recognize suspicious login attempts and report them immediately can notably enhance security, especially regarding their usernames., ensuring they are configured for optimal security.
| Security Risk | Description | Mitigation Strategy |
|---|---|---|
| Single Point of Failure (SPoF) | If the SSO system is compromised or experiences downtime, access to all linked applications is lost. | Implement redundant authentication servers, failover mechanisms, and distributed architectures to ensure continuous uptime. |
| Phishing Attacks | Users may be tricked into providing their SSO credentials, giving attackers access to all connected services. | Enforce Multi-Factor Authentication (MFA) and conduct security awareness training to help users identify phishing threats. |
| Session Hijacking | Attackers can steal session tokens and impersonate legitimate users. | Use short session lifetimes, automatic logouts, encrypted session storage, and context-aware authentication. |
| Credential Theft | If an attacker obtains an SSO password, they gain access to all linked applications. | Require strong password policies, adaptive MFA, and risk-based authentication. |
| Unauthorized Access (Privilege Escalation) | Weak access control configurations can allow users to gain unauthorized privileges. | Enforce Role-Based Access Control (RBAC) and regular access reviews. |
| Man-in-the-Middle (MITM) Attacks | Unsecured authentication requests can be intercepted by attackers. | Use TLS encryption, digital signatures, and token validation to secure communication. |
| Compliance & Audit Risks | Without proper logging, organizations may fail regulatory audits. | Enable comprehensive logging, audit trails, and anomaly detection systems. |
According to IBM’s 2024 Cost of a Data Breach Report, the average data breach now costs $4.45 million, with stolen or compromised credentials being the most common cause, accounting for 19% of breaches. This highlights the critical need for organizations to enforce strong authentication mechanisms such as MFA and risk-based authentication to mitigate credential-based attacks.3
$4.45 million
The average total cost of a data breach in 2024
How does SSO improve security?
Enterprise Single Sign-On (SSO) is a powerful tool for securing user identities and streamlining access across multiple applications. However, its effectiveness depends on robust security measures, strategic implementation, and seamless integration with existing systems. This section outlines essential security enhancements, benefits, and implementation strategies to help organizations deploy an effective and secure SSO framework.
Multi-factor authentication (MFA)
Multi-factor authentication (MFA) stands out as a critical security enhancement. By requiring users to present two or more verification methods, MFA significantly mitigates the risk of unauthorized access. The factors typically include:
– Something you know (like a password)
– Something you have (such as a mobile device for a one-time code)
– Something you are (biometric verification)
Integrating MFA is critical for guarding against breaches caused by compromised passwords, making it a key component of a robust SSO setup.
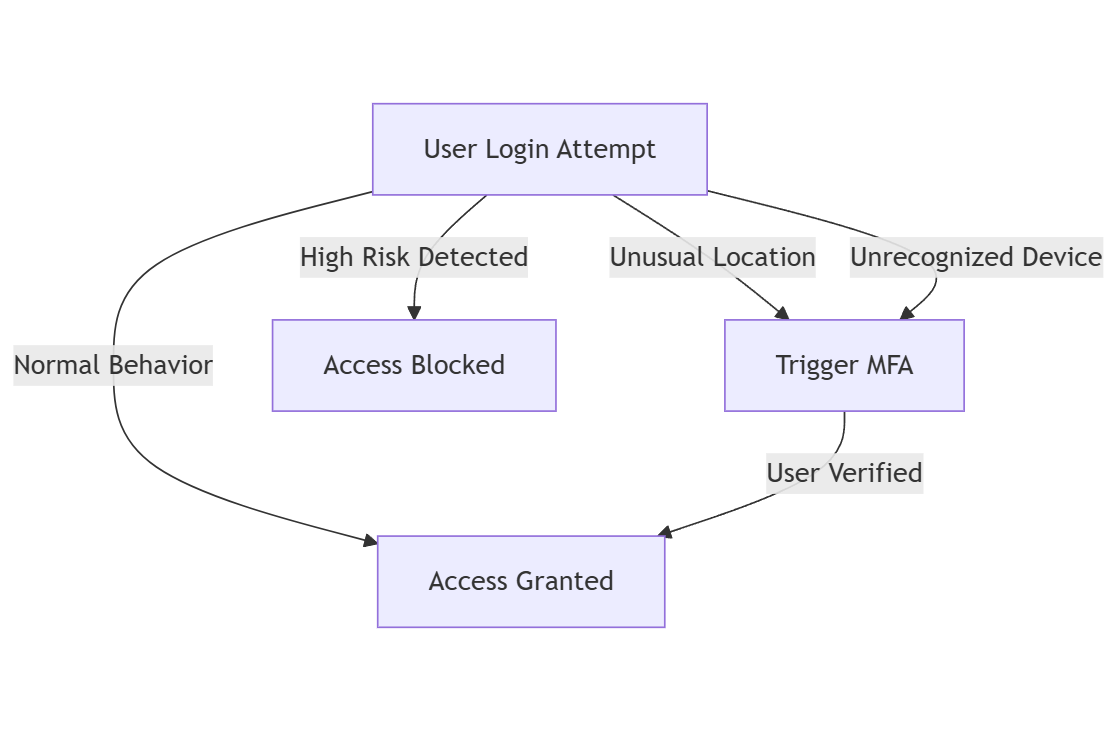
What is Risk-Based Authentication (RBA) and how does it strengthen SSO?
RBA analyzes login behavior and applies additional security measures when anomalies are detected. It assesses:
- Login location – Blocking or requiring extra verification for logins from unfamiliar locations.
- Device health – Denying access from compromised or unpatched devices.
- Login frequency & behavior – Flagging unusual authentication patterns.
Example: If an employee usually logs in from New York at 9 AM, but suddenly logs in from Russia at 3 AM, RBA can prompt additional authentication steps or block access entirely.
Tamper-proof authentication
Tamper-proof authentication mechanisms are vital for preventing unauthorized alterations to authentication data. Techniques such as digital signatures and encryption play an important role in ensuring the integrity of authentication tokens. These measures guarantee that if a token is intercepted, its integrity is preserved, thereby protecting sensitive user information.
What is Contextual Access Control (CAC) and how does it work with SSO?
Contextual access control (CAC) provides an additional security layer by assessing the context of user access requests. Factors evaluated include:
- User location (e.g., logging in from a foreign country triggers additional verification)
- Device security status (e.g., denying access from an unpatched or jailbroken device)
- Time of access (e.g., restricting logins outside of business hours)
By evaluating these factors, organizations can implement flexible access controls that adapt to varying risk levels, ensuring sensitive data is only accessible under secure conditions.
Token-Based Authentication & Secure Session Management
Token-based authentication enhances security by eliminating direct password transmission between clients and servers.
- OAuth 2.0 & OpenID Connect (OIDC) use access tokens for secure authentication.
- Short-lived session tokens reduce the risk of session hijacking.
- Implement automatic logout after periods of inactivity.
Best Practice: Use JWT (JSON Web Tokens) with expiration times and token revocation capabilities to prevent misuse.
How is AI enhancing SSO security?
The role of Artificial Intelligence (AI) in SSO solutions is increasingly important. AI can analyze user behavior patterns and detect anomalies in real-time, helping to flag suspicious activities for further investigation. rely on older applications that may not support modern authentication methods.
The IBM 2024 report found that organizations utilizing AI-driven security and automated threat detection reduced the cost of breaches by an average of $1.76 million. AI-powered authentication solutions, combined with behavioral analytics, can identify suspicious login attempts and proactively block potential threats before they escalate
Business benefits of SSO for enterprises
Enterprise Single Sign-On (SSO) offers numerous advantages that directly enhance security, user experience, productivity, and cost efficiency for organizations. Drawing from extensive experience in identity and access management projects, it’s clear that SSO can significantly transform organizational operations.
Enhanced Security
First, consider the security enhancements that SSO provides:
- Centralized authentication: By consolidating the authentication process, SSO effectively lowers the risk of unauthorized access. By using a single set of credentials, organizations can significantly minimize the risk of breaches.
- Risk-based authentication (RBA): This feature analyzes user behavior and context, enabling organizations to spot unusual activities and respond by requiring additional verification for suspicious logins.
- Compliance support: Many SSO solutions enable organizations to comply with stringent regulations like HIPAA and GDPR, which require strong access controls and comprehensive audit trails.
- Audit requirements: SSO provides a detailed audit trail for user access, making it easier to fulfill compliance and regulatory obligations.
An example is the Pentagon’s Defense Information Systems Agency, developing a unified digital access tool for identity verification across military branches, beginning with the Army. Their goal is to simplify access to unclassified networks, emphasizing the importance of SSO in high-security settings.¹
User experience and productivity
SSO also plays a pivotal role in enhancing user experience and boosting productivity:
- Improved user experience: With SSO, employees enjoy streamlined login processes, allowing them to access various applications with a simple click. This not only enhances user satisfaction but also reduces the frustration associated with managing multiple passwords.
- Increased productivity: By minimizing the time spent on logins and password resets, employees can focus more on their core responsibilities.
Studies indicate that SSO can save organizations approximately 30 minutes per employee each month, resulting in significant productivity gains.
Cost efficiency
From a financial perspective, SSO can result in substantial cost savings for enterprises:
- Minimized IT support costs: With fewer password-related incidents, organizations can ease the burden on IT support teams, enabling them to focus on more critical projects.
- Better control over software licenses: SSO solutions often provide insights into application usage, enabling organizations to optimize their software licensing and cut unnecessary costs.
| Benefit | Description | Impact |
|---|---|---|
| Enhanced security | Centralized authentication reduces unauthorized access risks. | Lower risk of data breaches. |
| User experience | Streamlined logins improve satisfaction and reduce frustration. | Higher employee morale. |
| Increased productivity | Less time on logins translates to more focus on core tasks. | Improved operational efficiency. |
| Cost efficiency | Reduced IT support costs and optimized software licensing. | Greater ROI on IT investments. |
How to implement SSO successfully in your organization?
Implementing Enterprise Single Sign-On (SSO) requires careful planning that combines identity management, user authentication, authorization, access control, and integration with legacy systems. Through my work with clients on identity and access management projects, I have identified effective strategies IT leaders can use to achieve successful SSO implementation while ensuring a smooth user experience.
Identity Management & Governance
Organizations should establish a robust authentication method that must be actively managed: centralized identity management system that ensures:
- Up-to-date user information and access rights.
- Defined roles and permissions to minimize security risks.
- Automated identity lifecycle management, from onboarding to access revocation.
Strong User Authentication
For SSO to be effective, organizations need a strong user authentication mechanism. Here are a couple of strategies I recommend:
– Multi-Factor Authentication (MFA): Integrating MFA into the SSO process significantly enhances security. Users are required to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device. This extra layer is invaluable in keeping unauthorized users at bay.
– Adaptive authentication: This strategy adjusts the authentication process according to the risk level of each login attempt. It evaluates factors like user behavior, location, and device security, applying additional authentication steps when deemed necessary. This approach provides an adaptive security measure that responds to varying levels of risk.
Authorization and access control
Once users are authenticated, the next step is to determine what they can actually do. To streamline access control, I recommend:
– Implementing Role-Based Access Control (RBAC): This method assigns permissions based on user roles, simplifying management and ensuring users access only the applications they need.
– Utilizing Contextual Access Control (CAC): CAC evaluates the context of user access requests, such as time, location, and device security. This evaluation allows for dynamic access controls that adapt to varying risk levels, which is especially useful in today’s ever-changing work environment.
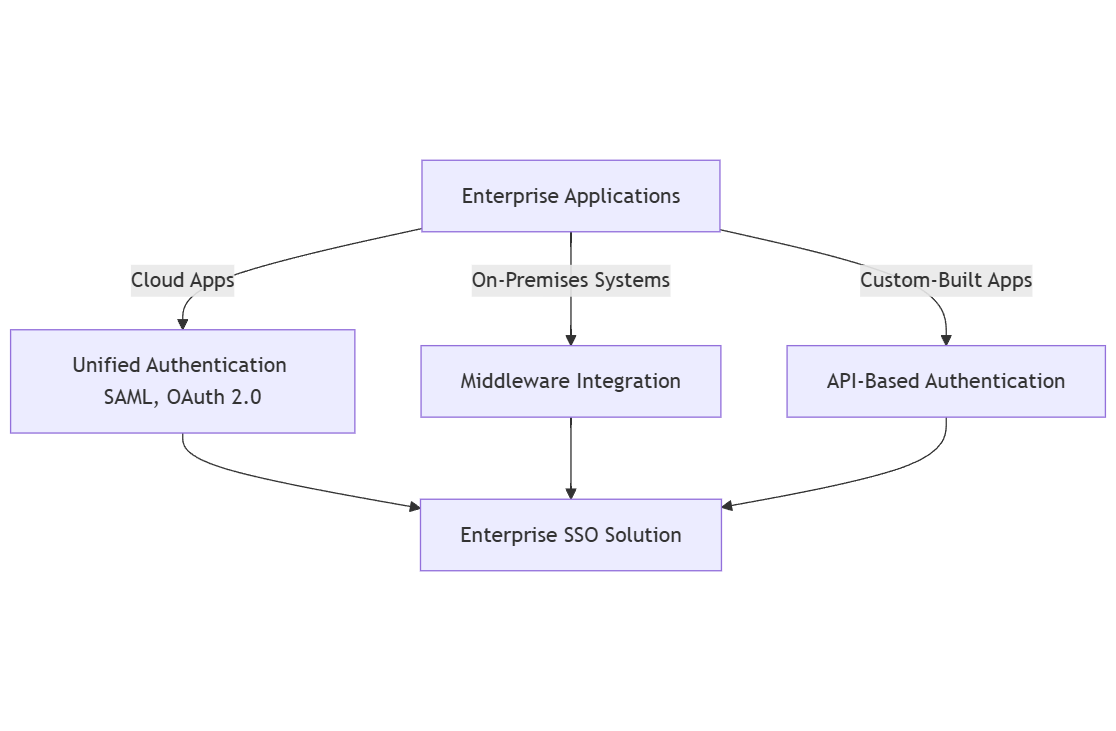
How to integrate SSO with legacy applications?
Integrating legacy systems with modern SSO solutions presents challenges, yet it is essential for comprehensive access management. Here’s how to navigate this:
– Use of middleware: Middleware solutions can serve as a bridge between legacy applications and modern identity management systems. This allows for seamless integration without the need to overhaul existing systems.
– API-based integration: For those legacy systems that support it, leveraging APIs can facilitate direct integration with SSO solutions, enabling efficient data exchange and user authentication.
User experience and convenience
Ultimately, the aim of implementing SSO is to enhance user experience. Here are a few strategies I’ve found effective:
– Streamlined user interfaces: A user-friendly and consistent SSO login interface across all applications reduces confusion and enhances satisfaction. It’s all about making it easy for users to log in and get to work.
– User education: Offering training and resources to educate users about the SSO system is key. This includes emphasizing the importance of security measures like MFA and how to spot phishing attempts.
| Implementation strategy | Benefits | Challenges |
|---|---|---|
| Identity management | Centralizes user data and simplifies access control | Requires initial setup and ongoing maintenance |
| User authentication (MFA) | Enhances security and reduces the risk of unauthorized access | May introduce friction if not implemented thoughtfully |
| RBAC & CAC | Simplifies management and ensures the principle of least privilege | Complexity in defining roles and permissions |
| Legacy system integration | Ensures comprehensive access management across all systems | Technical challenges and potential compatibility issues |
| User experience enhancements | Increases user satisfaction and improves productivity | Requires ongoing education and support |
By embracing these implementation strategies, organizations can forge a secure, efficient, and user-friendly SSO environment. This not only fortifies security but also streamlines user access, aligning seamlessly with the overarching goals of a Zero Trust strategy.
What are the challenges of implementing SSO?
Deploying Single Sign-On (SSO) in an enterprise presents significant
that require thorough planning, technical expertise, and proactive security measures. While SSO enhances security and user experience, integrating it with existing systems, ensuring compliance, and managing costs can be complex. This section explores the most common challenges enterprises encounter when implementing SSO and offers strategies to overcome them.
67.5% of corporate logins –
Are still done using passwords instead of SSO-backed authentication
Integration issues
Integration complexity
One of the most significant obstacles to SSO deployment is integrating diverse enterprise applications into a single authentication system. Many organizations operate a hybrid environment consisting of:
- Cloud applications
- On-premises legacy systems
- Custom-built enterprise applications
Each system may require different authentication mechanisms, making seamless integration difficult. Organizations need a well-defined integration strategy that accounts for:
- Unified authentication protocols (SAML, OAuth 2.0, OpenID Connect).
- API-based integrations to bridge compatibility gaps.
- Middleware solutions to connect legacy systems with modern identity providers (IdPs).
The FS-ISAC report highlights that financial institutions face increased complexity when integrating modern identity management solutions due to legacy infrastructure and regulatory compliance needs. This aligns with the challenges enterprises face when implementing SSO, particularly when dealing with hybrid environments combining on-premises and cloud applications. 4
Legacy system integration
Many organizations still rely on older applications that were not built to support modern authentication standards. These systems may:
- Lack support for SSO protocols like SAML or OAuth 2.0.
- Require manual authentication workarounds, reducing SSO effectiveness.
- Introduce security vulnerabilities if not properly integrated.
Solution:
- Implement custom connectors or middleware solutions that allow legacy applications to interact with modern identity platforms.
- Gradually modernize authentication frameworks by replacing outdated authentication mechanisms with federated identity solutions.
Single Point of Failure (SPoF)
A well-known risk of SSO is that it centralizes authentication. If the SSO system fails, users could lose access to all connected applications, disrupting business operations.
Mitigation Strategies:
- Deploy redundant authentication servers to maintain uptime.
- Implement failover mechanisms to ensure backup authentication pathways.
- Ensure SSO services are distributed across multiple data centers.
SSO Compromise Risks
While SSO eliminates the need for multiple passwords, if a user’s SSO credentials are compromised, an attacker could potentially gain access to all connected applications.
Mitigation Strategies:
- Enforce Multi-Factor Authentication (MFA) to add a second layer of protection.
- Implement risk-based authentication (RBA) that evaluates login behaviors and triggers additional verification for high-risk activities.
- Monitor user activity logs to ensure proper sign-in processes. for unusual access patterns.
Customization requirements
Every organization has its unique workflows and security needs, often necessitating some degree of customization of the SSO solutions. Pricing for Microsoft Learn resources related to security and authentication methods: It’s crucial to ensure that modifications do not weaken the SSO’s security. A careless tweak could expose the organization to potential threats, which is a risk no enterprise can afford to take.
A striking report notes that 80% of enterprise SaaS logins are not visible to IT and security teams because users often rely on personal credentials or non-SSO corporate accounts. This visibility gap contributes to significant security risks, highlighting the importance of comprehensive monitoring during SSO implementations
Compliance and governance
Compliance and governance play a crucial role in effectively implementing Enterprise Single Sign-On (SSO). From my experience with various clients in identity and access management, it is essential to navigate regulatory requirements and internal policies to secure sensitive information and protect user privacy. We will explore the key elements of compliance audit requirements and access governance and their importance in the SSO framework.
Compliance audit requirements
Compliance audits are crucial for meeting regulatory standards and following internal policies. Organizations implementing SSO should prioritize these key requirements:
- Regulatory compliance: Organizations must be aware of industry-specific regulations like GDPR, HIPAA, and PCI DSS. These standards impose strict controls over user data access and management, making it essential to maintain comprehensive audit trails to demonstrate compliance.
- Access control policies: Establishing clear access control policies is essential. This involves defining user roles, permissions, and the processes for granting and revoking access. Regular audits ensure consistent enforcement of policies across applications.
- User activity logging: Effective logging mechanisms play a key role in monitoring user activity within the SSO system. Effective logs should capture login attempts, including failed sign-in attempts, access requests, and administrative actions, thereby providing a comprehensive record for compliance audits.
| Audit requirement | Description | Importance |
|---|---|---|
| Regulatory compliance | Adherence to laws governing data access | Avoids legal penalties and reputational damage |
| Access control policies | Defined roles and permissions for user access | Ensures the principle of least privilege is maintained |
| User activity logging | Detailed logs of user actions within the SSO system | Facilitates auditing and incident response |
Security automation plays a crucial role in compliance and governance. IBM’s 2024 report found that organizations leveraging full security automation reduced their breach costs by $1.76 million and shortened their response time by an average of 99 days. This demonstrates the importance of automated governance tools for access management, anomaly detection, and compliance tracking3
The FS-ISAC report emphasizes that strong authentication frameworks (like SSO combined with MFA) are essential for regulatory compliance in banking and financial services. 4
Access governance
Access governance encompasses the policies and processes that manage user access rights, ensuring compliance with organizational standards. Effective access governance within SSO implementations includes:
- Role-based access control (RBAC): Implementing RBAC simplifies access management by assigning permissions based on user roles. This approach minimizes the complexity of managing individual user permissions while enhancing compliance with access policies.
- Regular access reviews: Conducting periodic access reviews is essential for maintaining compliance. These reviews help identify and remedy any unauthorized access or outdated permissions, ensuring users retain only the access necessary for their roles.
- Automated governance tools: Utilizing automated tools for access governance can streamline compliance efforts. This feature enables users to access resources across various domains without having to log in again, thanks to federated identity management, which is how SSO works.
| Access governance strategy | Benefits | Challenges |
|---|---|---|
| Role-based access control (RBAC) | Simplifies management and enhances compliance | Requires careful role definition |
| Regular access reviews | Ensures up-to-date access permissions | Time-consuming if done manually |
| Automated governance tools | Streamlines compliance efforts and identifies anomalies | Initial setup and integration complexity |
By prioritizing compliance audits and strong access governance strategies, organizations can enhance security and user experience while aligning with regulatory mandates. Being proactive about compliance and governance is essential for maintaining trust and protecting sensitive data in the current digital environment.
What are the latest trends and innovations in SSO?
Enterprise Single Sign-On (SSO) is changing quickly due to the demand for stronger security and better user experiences. Organizations are implementing new technologies that significantly impact SSO solutions. I want to highlight key advancements – Identity Federation, Digital Gatekeepers, Centralized User Management, and Federated Identity Management (FIM).
Identity federation
Identity Federation empowers organizations to establish trust relationships across diverse domains. This allows users to access resources across various organizations using a single set of credentials. It’s a game-changer for businesses collaborating with partners or navigating multi-cloud environments. By streamlining access management and reducing the complexity of handling multiple identities, Identity Federation significantly enhances security through the centralization of authentication processes.
Digital gatekeeper
The role of a Digital gatekeeper is becoming crucial as organizations focus on implementing strong security measures. This centralized authority manages user access and authentication across various applications and services. By utilizing advanced algorithms and machine learning, these gatekeepers monitor user behavior, identify unusual activities, and enforce security policies immediately. This proactive approach not only fortifies security but also enriches the user experience by minimizing friction during the login process.
Centralized user management
Centralized User Management systems are becoming essential for organizations focused on streamlining identity and access management. These systems gather user data from multiple sources, providing a comprehensive overview of identities across the organization. By integrating with other security solutions, centralized user management ensures consistent enforcement of access rights, thus reducing the risk of unauthorized access. This method simplifies user provisioning and deprovisioning while enhancing compliance with regulatory requirements.
| Technology | Description | Benefits |
|---|---|---|
| Identity Federation | Establishes trust relationships for seamless access across multiple domains. | Reduces credential management complexity and enhances collaboration. |
| Digital Gatekeeper | Central authority managing authentication and access control in real-time. | Detects anomalies and enforces security policies proactively. |
| Centralized User Management | Consolidates user data for a unified view of identities across the enterprise. | Simplifies access management and enhances compliance. |
| Federated Identity Management | Manages identities across different systems while allowing single sign-on capabilities. | Increases user satisfaction and reduces password fatigue. |
Federated identity management (FIM)
Federated Identity Management (FIM) extends the concept of identity federation, allowing organizations to manage identities across independent domains. This technology enables users to authenticate once and gain access to multiple services without repeated logins. FIM greatly enhances user experience and bolsters security by minimizing the number of credentials users need to juggle. As cloud services and third-party applications expand, FIM will be essential for simplifying access while maintaining strong security. This trend is vital for businesses handling sensitive data or operating in regulated sectors.
What should you consider before deploying SSO?
Implementing Enterprise Single Sign-On (SSO) presents unique challenges that organizations must address for secure and efficient authentication. A major concern is the Single Point of Failure (SPoF) that SSO systems may create. If the SSO infrastructure is compromised, access to all connected applications is at risk. Therefore, it is essential to implement strong security measures.
Single point of failure (SPoF)
A Single Point of Failure refers to any system component whose failure disrupts the entire operation. In the case of SSO, if the authentication service goes down or is breached, users might lose access to all connected applications. To reduce this risk, organizations can take the following steps:
– Redundancy: Implementing redundant systems and failover mechanisms ensures the authentication service remains operational even if one component falters.
– Distributed architecture: Adopting a distributed architecture for the SSO solution can help balance loads and lower the risk of a complete system failure.
– Regular backups: Regular backups of authentication databases are essential for quick recovery from potential data loss.
Security measures
To address the vulnerabilities of SSO, organizations should use a multi-layered security approach:
– Multi-Factor Authentication (MFA): Integrating MFA adds an essential layer of security, requiring users to provide two or more verification factors for access. This significantly diminishes the risk of unauthorized access, particularly when user credentials are compromised².
– Encryption: Strong encryption protocols for data transmission and storage are necessary to protect sensitive user information from interception or unauthorized access.
User provisioning and management
Effective user provisioning and management are crucial to give users the right access across different applications. Organizations should consider:
– Automated provisioning: Utilizing automated provisioning tools can streamline the process of granting access and managing user identities across applications.
– Role-Based Access Control (RBAC): Implementing RBAC assigns permissions based on user roles, ensuring users only access the applications essential for their job functions.
Performance and availability
SSO solutions must perform reliably and be scalable to support organizational growth and rising user demand. Key considerations include:
– Load testing: Regular load testing is necessary to ensure the SSO system can handle peak usage periods without performance degradation.
– Scalability: Selecting an SSO solution that can scale easily is crucial for accommodating the growing number of users and applications within the organization.
Compliance with regulatory requirements
Organizations need to make sure their SSO systems meet regulatory standards like GDPR or HIPAA. This encompasses:
– Audit trails: Comprehensive audit trails of user access and authentication events are necessary to demonstrate compliance during audits.
– Data privacy: Policies and procedures must be in place to protect user data and ensure adherence to data privacy regulations.
User education
Educating users is essential for employees to use SSO systems effectively and securely. Organizations should:
– Training programs: Develop training initiatives to educate users about the importance of security measures, such as recognizing phishing attempts and understanding the benefits of MFA.
– Ongoing support: Providing continuous support and resources can help users adjust to the SSO system and address any concerns.
How to choose the best SSO provider for your business?
Selecting the right Single Sign-On (SSO) provider is a critical decision for organizations seeking to enhance security, improve user experience, and ensure seamless integration across their IT infrastructure. The right provider should align with an organization’s security needs, scalability requirements, and compliance mandates. This section outlines the key selection criteria, top SSO providers, and real-world case studies demonstrating successful SSO implementations.
Top SSO Providers and their offerings
| Provider | Key Features | Pricing | Integration Complexity |
|---|---|---|---|
| Inteca | Personalization and enterprise-grade scalability | Architecture based | Low |
| Okta | Cloud-based IAM | Subscription | Medium |
| Auth0 | Developer-friendly | Subscription | Medium |
| OneLogin | Unified cloud directory | Subscription | High |
| JumpCloud | Cloud Directory | Subscription | High |
| Microsoft Azure AD | Enterprise-grade IAM | Subscription | Medium |
| IBM Security Verify | AI-powered IAM | Subscription | High |
| Oracle Identity Cloud Service | Hybrid IAM | Subscription | High |
| Amazon Cognito | Scalable authentication | Pay-as-you-go | Medium |
| Infisign UniFed SSO | Enterprise SSO | Subscription | Medium |
Choosing the right provider depends on an organization’s specific needs, such as cloud compatibility, regulatory compliance, or API-based integration requirements.
Factors to consider when selecting an SSO provider
When assessing potential SSO providers, IT leaders should consider the following factors:
– Security protocols: It is essential to verify that the provider adheres to established security protocols, including SAML, OAuth 2.0, and OpenID Connect, to protect user data.
– Integration capabilities: Evaluating the ease of integration of the SSO solution with existing applications and systems will streamline implementation and optimize resource usage.
– Customization options: Customizable solutions allow providers to tailor their offerings to meet specific organizational workflows, thereby improving user experience.
– Scalability: Select a solution capable of scaling effectively to accommodate the growing number of users and applications.
– Pricing: Finally, assessing the pricing model against your budget and anticipated usage is vital for making a cost-effective choice.
Strategic implementation
- Choose the right identity provider (IdP): Choosing a trustworthy identity provider (IdP) with proven security features is vital. Look for providers that offer robust security features, seamless integration capabilities, and strong support for various authentication protocols like SAML and OAuth 2.0.
- Plan for legacy integration: Confirm that your SSO solution can work seamlessly with your current infrastructure. Middleware and API-based solutions can bridge the gap between legacy systems and modern applications, ensuring a smooth transition.
What are the hidden costs of SSO implementation?
While SSO reduces IT costs in the long run, hidden expenses can arise during and after implementation.
| Hidden Cost | Description | Mitigation Strategy |
|---|---|---|
| Initial Setup Costs | Requires significant investment in software, integration, and deployment. | Choose scalable solutions to avoid excessive customization. |
| Ongoing Maintenance | Regular updates, patches, and security upgrades increase costs. | Budget for long-term maintenance in IT planning. |
| Vendor Lock-in | Proprietary SSO solutions may lead to dependency on a single provider. | Opt for open standards-based solutions to ensure flexibility. |
For organizations in critical infrastructure sectors (e.g., finance, healthcare, government), the cost of a data breach is significantly higher—$5.04 million on average, according to IBM’s 2024 report. This underscores the need for robust SSO security measures, as compromised credentials can lead to far-reaching financial and operational consequences.3
How do companies use single sign-on?
Throughout my work on identity and access management projects, I have encountered several case studies demonstrating how Single Sign-On (SSO) enhances security and simplifies user access across various sectors.
To illustrate the benefits of SSO adoption, the following case studies highlight real-world examples of successful implementations.
| Case Study | Key Outcomes | Benefits |
|---|---|---|
| Norton LifeLock | Streamlined secure access for employees and customers | Reduced password fatigue, enhanced security |
| LastPass | Improved authentication management for customers | Strengthened password security, improved user experience |
| Academic Institution | Centralized authentication for students and faculty | Reduced helpdesk calls, consistent security policies |
| Inteca (European Economic Bureau) | Federated authentication across multiple banks | 99.9% uptime, increased security |
Norton LifeLock
For example, Norton LifeLock illustrates this point well. As a leader in cybersecurity, they implemented SSO to streamline access to various security tools for employees and customers. This move not only reduced password fatigue but also allowed users to access multiple services with just one set of credentials. This led to a secure and efficient user experience, further solidifying Norton LifeLock’s reputation as a trusted security provider.
LastPass
LastPass, known for its password management solutions, also serves as a relevant example. By integrating SSO, they provided seamless access to multiple applications and addressed the prevalent problem of password reuse. This shift prompted users to adopt stronger, unique passwords, improving user experience and reinforcing LastPass’s commitment to security.
Academic institution
A prominent academic institution struggled with disjointed access for students and faculty. The implementation of an SSO solution centralized their authentication processes, allowing users to access various educational resources with a single login. This change enhanced user experience and significantly lowered helpdesk calls for password resets while ensuring consistent password policies.
Inteca case study
Another compelling case involves Inteca. A leading European Economic Information Bureau implemented a tailored cybersecurity solution that federated user authentication with multiple European banks. This initiative achieved a 99.9% uptime for authentication services, significantly enhancing user experience. By integrating SSO, we streamlined the authentication process and fortified security measures, allowing the bureau to operate efficiently while safeguarding sensitive information.
These case studies reinforce the value of SSO, demonstrating its ability to improve security, enhance user satisfaction, and streamline access management.
The role of user education in SSO success
User education and awareness are essential for maximizing the effectiveness of Single Sign-On (SSO) systems. Through my experience with clients in identity and access management, I’ve found that SSO provides robust security and streamlined access, but its success largely depends on users’ understanding and engagement. Here are the key reasons why improving users’ understanding is vital:
Understanding the system
For SSO to be effective, users must understand its functionalities. This includes understanding the significance of a single set of credentials, recognizing security implications, and acknowledging the daily advantages of SSO. Conducting effective training sessions can clarify how the technology works, helping users feel more comfortable and confident in using it.
Reducing security risks
Educated users are less likely to fall victim to security threats. By educating team members about phishing attacks and the importance of safeguarding their credentials, organizations can reduce the risk of unauthorized access. For example, training users to recognize suspicious login attempts and report them immediately can notably enhance security.
Best practices for users
Training should also include key practices for ensuring security when using SSO:
– Creating strong passwords: Advise users to create strong passwords and update them regularly.
– Utilizing MFA: Emphasize the value of Multi-Factor Authentication (MFA) to enhance security.
– Regularly reviewing access rights: Inform users about the importance of regularly reviewing their access rights to maintain access to only necessary resources.
Continuous learning
Education must not be viewed as a one-time effort. Fostering a culture of continuous learning about SSO and security is crucial for organizations to effectively combat emerging threats. Regular refresher courses, updates on best practices, and discussions about new challenges help maintain a focus on security for all team members.
Future of SSO and emerging trends
As we look to the future, Single Sign-On (SSO) is evolving rapidly, influenced by new technologies and a stronger emphasis on security. Here are some key emerging trends that will shape the future of SSO.
Passwordless authentication
Organizations are increasingly adopting passwordless authentication to bolster security and enhance user experience. Technologies like biometrics, FIDO2, and magic links are at the forefront of this movement.
| Technology | Description | Benefits | Challenges |
|---|---|---|---|
| Biometrics | Utilizes unique physical traits (e.g., fingerprints, facial recognition) for authentication. | Strong security, user convenience | Privacy concerns, hardware costs |
| FIDO2 | A passwordless authentication standard that employs public key cryptography. | Robust security, resistance to phishing | Implementation complexity |
| Magic links | Sends a time-sensitive link to the user’s email for authentication. | Simple user experience | Email security issues |
Despite the advantages of passwordless options, organizations face hurdles such as complex integration and the need to encourage user acceptance. Transitioning away from traditional passwords necessitates ensuring these new methods are both user-friendly and secure.
References:
-
Defense One. Pentagon Plans Unified Digital Access Tools Across Military. Retrieved from: https://www.defenseone.com/defense-systems/2025/02/pentagon-plans-unified-digital-access-tools-across-military-year/403245/?oref=d1-featured-river-secondary
-
CSO Online. CISOs Should Address Identity Management ‘As Fast As They Can’ Says CrowdStrike Exec. Retrieved from: https://www.csoonline.com/article/3836917/cisos-should-address-identity-management-as-fast-as-they-can-says-crowdstrike-exec.html
-
IBM Security. Cost of a Data Breach Report 2024. Retrieved from: https://www.ibm.com/reports/data-breach
-
Deloitte. Cybersecurity Report: Threat Intelligence Trends in Financial Services (2020). Retrieved from: https://www2.deloitte.com/us/en/insights/industry/financial-services/cybersecurity-maturity-financial-institutions-cyber-risk.html
See why Keycloak may be the best choice for your enterprise SSO!