I. Introduction to centralized identity management (IAM)
What is centralized access management?
Centralized Identity and Access Management (IAM) simplifies the management of user identities and their access permissions by consolidating these functions into one system. This model allows organizations to improve their operational workflows and strengthen security, as it centralizes identity-related tasks like authentication and authorization. In contrast, decentralized methods distribute identity management across multiple systems and applications, which can create security vulnerabilities and complicate operations. Centralized IAM helps businesses establish a clear framework that simplifies processes and enhances their overall security.
Why centralized IAM is important?
As organizations adapt to technological changes, they increasingly depend on data and technology to support their operations. This reliance highlights the importance of implementing effective and secure access management. Centralized IAM proves essential as it enables organizations to enforce consistent security policies, reduce vulnerabilities, and comply with regulations. For instance, the Pentagon’s IT agency is developing a comprehensive identity solution aimed at improving identity verification across military branches. This initiative illustrates that centralized IAM can enhance security and make access management easier across different sectors, ultimately protecting sensitive information.¹
Core concepts in centralized identity management
To grasp the fundamentals of IAM, it is essential to understand key concepts and terminology commonly used in the field. Here’s a quick rundown:
| Term | Definition |
|---|---|
| Identity | The unique representation of a user within a digital ecosystem. |
| Authentication | The process of confirming a user’s identity, usually involving passwords or biometrics. |
| Authorization | This determines what an authenticated user can do, governed by specific access control policies. |
| Access control | Mechanisms aimed at restricting access to resources, ensuring that only authorized individuals can access sensitive data or applications. |
| Policies | Rules outlining how access is granted or denied based on user roles and attributes. |
| Permissions | Specific rights assigned to users that dictate their actions within a system. |
| Users, roles, groups | Users are individuals; roles are sets of permissions; groups are collections of users sharing similar access needs. |
What is the difference between centralized and decentralized IAM?
In the past, identity management was often fragmented, with separate systems managing user identities in isolation. This piecemeal approach led to inefficiencies and heightened security risks in a decentralized access control environment. The transition toward centralization has been driven by the need for improved control, visibility, and compliance in managing user identities. As organizations contend with evolving threats and regulatory demands, adopting a centralized IAM framework has become not just advantageous but essential for their operational integrity.
| Factor | Centralized IAM | Decentralized IAM |
|---|---|---|
| Management | Centralized in a single system | Distributed across multiple systems |
| Security | Stronger control, uniform policies | Higher risk due to fragmented controls |
| User Experience | Simplified with SSO & unified access | Complex with multiple logins |
| Compliance | Easier to enforce policies & audits | Harder to monitor compliance |
| Scalability | Easily scalable with automation | Can become complex at scale |

Is your access management secure?
II. What are benefits of centralized access management approach?
Centralized Access Management significantly improves security and operational efficiency while providing a better user experience. Numerous organizations have reported transformative benefits after adopting a centralized IAM system. This section will outline the key advantages of centralized IAM, backed by relevant examples and data.
Enhanced security due to central system
A key advantage of Centralized Access Management is its capacity to fortify an organization’s security through a unified access control system. By consolidating access controls, organizations can uniformly enforce security policies across their systems. This uniformity drastically reduces the risk of human error and misconfiguration, which often plague decentralized systems. Centralized platforms facilitate the integration of advanced security measures such as Multi-Factor Authentication (MFA), restricting access to sensitive information to authorized users only. Centralized systems simplify auditing and monitoring, making it easier to detect suspicious behavior.
Insight: Recently, Cisco raised alarms about critical vulnerabilities in its Identity Services Engine (ISE), which could enable unauthorized access and command execution. This underscores the necessity of a centralized framework to effectively mitigate such risks.²
Reduced password-related vulnerabilities
Centralized IAM systems greatly simplify the management of strong password policies by integrating external resources for password validation and enabling Multi-Factor Authentication (MFA). This integrated approach greatly reduces the risk of password-related security breaches.
Regular audits identify dormant accounts, allowing organizations to deactivate them and minimize potential attack surfaces. Additionally, the process of granting and revoking access becomes more efficient, ensuring that former employees or contractors no longer have access to critical systems, thus safeguarding against insider threats.
Insight: The emergence of phishing kits like Astaroth, capable of bypassing MFA by intercepting login credentials in real-time, highlights the need for robust centralized IAM solutions that can implement advanced MFA strategies.³
Improved control and visibility over access
Enhanced control and visibility over user access is another critical advantage. Centralized IAM empowers organizations to better manage and monitor user access rights through:
– Account management: Regular inventory checks and disabling dormant accounts to thwart unauthorized access.
– Access control management: Streamlined processes for granting and revoking access, paired with enforced MFA requirements, ensuring only authorized users access sensitive resources.
Improved operational efficiency
Centralized IAM systems make user provisioning and deprovisioning seamless, significantly speeding up the onboarding and offboarding processes. This includes:
– Simplified login procedures: With Single Sign-On (SSO) capabilities, users can reduce the number of credentials they need to remember, enhancing user satisfaction.
– Automation of access management tasks: This reduces IT overhead and support costs, allowing IT teams to focus on more strategic initiatives.
Enhanced user experience with advanced features
Centralized IAM enhances user experience by allowing seamless access to multiple applications via Single Sign-On (SSO). This alleviates password fatigue and enhances overall productivity.
Insight: The LayerX report emphasizes the importance for organizations to ensure the legitimacy of identities accessing enterprise applications, particularly within SSO contexts.⁴
Compliance and governance in centralized access control
- Unified Access Policies – Enforces security policies consistently across all systems.
- Automated Audits & Reporting – Provides detailed logs for compliance checks.
- Role-Based & Attribute-Based Access Controls (RBAC/ABAC) – Ensures users only access the data they are authorized to see.
- Quick Adaptation to Regulatory Changes – IAM makes it easier to update security protocols when regulations evolve.
Key Takeaway: Organizations leveraging IAM for compliance not only avoid legal penalties but also strengthen their overall security posture, improving trust with customers and stakeholders.

How much time can you save by implementing centralized access management?
III. What are the key components of centralized access management?
What is identity privider (IDPs)?
Identity Providers (IDPs) are key components of centralized access management, enabling effective user identity management. They authenticate users and provide identity information to different applications, making it easier to access various services. IDPs improve user experience by enabling a single login for multiple applications, reducing the hassle of remembering numerous passwords and enhancing security. Well-known IDPs like Okta, Azure Active Directory, and Google Identity exemplify how organizations can retain control over user identities while adhering to necessary security protocols and regulations.
What is single sign-on (SSO)?
Single Sign-On (SSO) is a key functionality of centralized IAM systems, allowing users to log in once to access multiple applications seamlessly. This significantly improves user convenience and reduces the hassle of managing multiple passwords.
How SSO works?
SSO establishes a trusted relationship between users and the applications they access. When a user logs in through the IDP, an authentication token is generated and shared with the desired applications, allowing access without further credential prompts.
Benefits of SSO for enterprises
- Enhanced user experience: A seamless experience for users with fewer prompts to log in.
- Reduced IT support costs: Fewer issues related to forgotten passwords, which in turn lowers operational expenses.
- Increased security: SSO can incorporate Multi-Factor Authentication (MFA) for an additional security layer in a centralized management environment.
What is MFA?
Multi-Factor Authentication (MFA) is a critical security measure requiring users to provide multiple verification forms before accessing applications. This is particularly vital for:
– Externally-exposed applications: MFA greatly lowers the chances of unauthorized access for internet-facing applications.
– Remote network access: MFA ensures that only authenticated users can access sensitive resources from remote locations.
Insight: A recent sophisticated phishing attack targeting organizations using Microsoft Active Directory Federation Services (ADFS) highlighted vulnerabilities, allowing attackers to bypass multi-factor authentication.⁵ This highlights the need for strong MFA strategies to defend against emerging threats.
Authorization services role
Authorization Services are essential in centralized access management, defining who can access specific resources. Key components include:
– Resource server: The server that hosts protected resources.
– Resource: The specific service or data being accessed.
– Scope: This indicates the extent of access granted to a user.
– Permission: Specifies the actions a user can perform on a resource.
– Policy: The overarching rules that govern access permissions in centralized vs decentralized access frameworks.
Centralized resource, permission, and policy management
Effectively managing resources, permissions, and policies is crucial for uniform access control across the organization. It includes:
– Policy types: Organizations can utilize various policies like User-based, Role-based (RBAC), JavaScript-based, and more, tailoring them to their needs.
– Permissions: These can be categorized as Resource-based and Scope-based, allowing for detailed access rights management.
– Policy decision strategies: Different strategies can be employed for access decision-making, ensuring flexibility and security.
Insight: With the rise of AI-driven governance frameworks, organizations are finding new ways to streamline compliance and risk management processes, enhancing their ability to handle access efficiently.⁶
User and account lifecycle management
Managing the user and account lifecycle is paramount for maintaining both security and compliance. This involves automating user provisioning, updates, and deprovisioning processes, ensuring that individuals have appropriate access rights during their tenure. Properly managing user lifecycles helps organizations reduce the risk of unauthorized access and meet regulatory requirements.
Is your IAM strategy strong enough?
Centralized policy enforcement
Centralized policy enforcement helps ensure that access policies are consistently applied across all systems and applications. This consistency not only enhances security but also simplifies compliance efforts. By centralizing policy management, organizations can swiftly adjust to regulatory changes and effectively implement security measures, resulting in a secure and compliant environment.
IV. How to implement centralized IAM solution?
Before initiating the implementation of a Centralized Access Management system, it is essential to define your organization’s specific requirements and objectives. This begins with a thorough evaluation of existing identity management practices, identifying specific challenges, and articulating the desired outcomes of a centralized solution. Typical goals for implementing a centralized solution involve strengthening security, streamlining user access, ensuring compliance, and reducing operational costs. Involving stakeholders from different departments during this phase promotes collaboration and ensures the system aligns with both IT and business requirements, covering all aspects of identity and access management.
Selecting the right software
Selecting the appropriate IAM solution is essential for the effective implementation of centralized access management. Consider the following critical factors:
| Criteria | Description |
|---|---|
| Vendors comparison | Assess various IAM vendors, such as Keycloak¹, Okta, and Microsoft Azure AD, focusing on their features and pricing. |
| Scalability | Ensure that the solution is scalable, capable of accommodating growth in users and applications. |
| Integration | Ensure the solution integrates seamlessly with your existing systems and applications to minimize disruption. |
| Authentication support | Look for solutions that provide diverse authentication methods, including Single Sign-On (SSO) and Multi-Factor Authentication (MFA). |
| Multi-tenancy | If your organization consists of multiple divisions or subsidiaries, consider solutions that offer multi-tenancy capabilities to manage identities across different environments. |
Centralized IAM vendors comparison
Evaluate vendors by comparing their offerings with your specific requirements. Below is a comparison of key features among popular IAM solutions, including Keycloak:
| Feature | Keycloak Managed Service – Inteca | Okta | Azure AD | Auth0 |
|---|---|---|---|---|
| Vendor-lock | No, we rely on open-source Keycloak from Red Hat | Yes | Yes | Yes |
| MFA Support | Yes | Yes | Yes | Yes |
| SSO capabilities | Yes | Yes | Yes | Yes |
| Integration options | Extensive | Extensive | Microsoft Ecosystem supports | Extensive |
| Scalability | High | High | High | High |
| Pricing | Architecture based | Per user | Per user | Per user |
Pro Tip: If your organization has a complex IT environment with on-premise and cloud apps, solutions like Keycloak or Okta may offer better flexibility.
Phased implementation approach
The implementation of a centralized access management system requires a systematic, phased approach. Start with a pilot program in a controlled environment, permitting modifications informed by user feedback and performance evaluation. Gradually expand the implementation to encompass more users and applications, ensuring that each phase undergoes thorough testing and validation. This strategy mitigates risks and helps manage change effectively, allowing your organization to adapt to new processes without overwhelming users.
How to integrate IAM with existing applications and infrastructure?
A successful integration with existing applications and infrastructure is critical for a smooth transition to a centralized IAM system. This integration could include the following steps:
– Assessing compatibility: Assess the compatibility of the new IAM solution with your existing software and hardware.
– APIs and connectors: Leverage APIs and connectors to link the IAM system with existing applications, ensuring smooth data exchange.
– Testing: Perform thorough testing to uncover any integration issues in the access control system prior to full deployment.
How to migrate data and users to IAM platform?
Data migration is a critical phase in the implementation of a centralized IAM system. This involves transferring existing user identity data into the new system while maintaining data integrity and security. Key steps include:
– Data cleanup: Remove duplicate or outdated user accounts before migration.
– Mapping data fields: Ensure that all user attributes are correctly aligned with the new IAM system.
– User onboarding: Create a user onboarding process that educates users about the new system, highlighting its benefits and guiding them on how to navigate it effectively.
Establishing governance and policy frameworks
Establishing governance and policy frameworks is essential for effectively managing access rights and meeting regulatory requirements. This includes:
– Access policies: Clearly define who has access to which resources based on user roles and responsibilities.
– Audit trails: Implement mechanisms to track user access and changes to permissions, promoting accountability and compliance.
– Regular reviews: Schedule periodic reviews of access rights to ensure they remain appropriate as roles and responsibilities evolve.
User training and change management
User training and robust change management are vital for the successful adoption of the new centralized IAM system. Organize comprehensive training sessions that cover:
– System navigation: Help users learn how to navigate the new IAM system efficiently.
– Security best practices: Educate users on security best practices, including recognizing phishing threats and using strong passwords.
– Feedback mechanisms: Set up channels for users to provide feedback and report issues, cultivating a culture of continuous improvement.
By prioritizing user training and change management, organizations can improve user engagement and facilitate the effective adoption of their centralized access management system.
V. Security in centralized access management
Security models like Zero Trust and Identity-First Security are transforming how organizations protect access to systems and data. Centralized Identity and Access Management (IAM) plays a critical role in enabling these paradigms by enforcing consistent identity verification, access control, and real-time monitoring.
What is Zero trust security model?
The Zero Trust Security Model assumes that no user, device, or network is inherently trusted—verification is required every time access is requested. Instead of relying on perimeter-based security, Zero Trust continuously evaluates user identities, device health, and contextual risk before granting access.
“Never trust, always verify.”
How Centralized IAM Implements Zero Trust?
Identity Verification at Every Access Point
- IAM ensures users authenticate every time they request access using Multi-Factor Authentication (MFA), not just at login.
Least Privilege Enforcement
- IAM applies Role-Based (RBAC) and Attribute-Based (ABAC) Access Controls to limit users to only what they need.
Continuous Monitoring & Risk-Based Access
- IAM tools detect anomalies (e.g., logins from unknown locations, high-risk devices) and trigger additional authentication or block access.
Single Sign-On (SSO) with Adaptive Security enhances centralized access control measures.
- While SSO improves user convenience, IAM systems enforce adaptive access rules based on device, location, and user behavior.
What is Identity-first security?
Identity-First Security shifts security focus from networks to users. Instead of protecting an organization’s perimeter (firewalls, VPNs), it secures access at the identity level—validating WHO is requesting access and enforcing strict security policies before granting entry.
“Users, not networks, are the new security perimeter.”
The six A’s of identity-first security
Centralized IAM encompasses the Six A’s of Identity-First Security:
| Security Principle | How Centralized IAM Supports It |
|---|---|
| ️Authentication | Enforces Multi-Factor Authentication (MFA) & passwordless authentication |
| Access Control | Implements RBAC & ABAC to ensure users only access what they need |
| Authorization | Uses policy-based permissions to control data access |
| Attributes | Uses user roles, location, device risk level to refine access |
| Administration | Automates user provisioning & deprovisioning for security compliance with centralized access control policies. |
| Audit & Reporting | Provides real-time access monitoring & audit logs to detect threats |
Adopting centralized access management that combines Zero Trust principles with Identity-First Security enhances security and improves IT efficiency. By prioritizing user identities and maintaining continuous verification of access, organizations can effectively protect their most critical resources against evolving threats.
Unused accounts are a hacker’s dream
VI. What are the challenged of centralized access management?
The risk of a single point of failure
A significant concern organizations face with Centralized Access Management is the risk of a single point of failure. If the centralized system goes down or gets compromised, a failure or compromise of the centralized system can result in access disruptions and expose sensitive data to breaches. To mitigate this risk, organizations should implement redundancy and disaster recovery plans. Having redundant systems in multiple locations helps ensure systems remain available. A strong disaster recovery strategy should include regular backups and efficient failover mechanisms. This approach allows organizations to recover quickly from incidents while minimizing downtime and maintaining security.
Scalability challenges
As organizations grow, they encounter challenges in scaling their user bases, devices, and applications. This growth can overwhelm centralized IAM systems, complicating the management of numerous identities and access requests. As identity management systems grow more complex, organizations need AI-driven solutions to manage resources and identities more effectively. By weaving AI technologies into their IAM strategies, businesses can enhance their systems to handle growth smoothly without compromising on performance or security.2
Complexity of integration
Integrating a centralized IAM solution with legacy systems and diverse technologies presents significant challenges. Many organizations still depend on older systems that may not integrate with modern IAM solutions, leading to potential security vulnerabilities and operational issues. To address these challenges, organizations should assess their current infrastructure and develop a clear integration strategy. Using APIs and connectors can help bridge the gap between legacy systems and modern IAM solutions, facilitating a smoother transition and enhancing security.
Ongoing maintenance and updates
To keep a centralized IAM system secure and functioning optimally, regular maintenance is essential. Regular updates and patches are crucial to fend off emerging threats and vulnerabilities. Organizations need to establish a proactive maintenance schedule that includes routine security assessments and updates. This diligence protects sensitive data and ensures compliance with changing regulations. By making maintenance a priority, organizations lay the groundwork for a secure environment for managing user identities and access.
Organizational change management
Effectively managing the human side of change is crucial for successfully adopting a centralized IAM system. Resistance to change can limit user acceptance and hinder the effective implementation of the system. To combat this, organizations should invest in detailed training programs that inform users about the benefits and functions of the new system. Furthermore, involving key stakeholders in decision-making helps create buy-in and encourages a smoother transition. Promoting a culture that embraces change allows organizations to fully realize the benefits of their centralized IAM initiatives.
VII. What are the access control models in IAM?
Effective access control models ensure users can only access resources necessary for their job functions. Centralized Access Management relies on structured access models to define user permissions systematically. The two primary models are Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC), each with its advantages and challenges.
This section breaks down RBAC vs. ABAC, provides real-world examples, and helps organizations determine which model (or combination) best fits their needs.
Role-based access control (RBAC)
What is RBAC?
RBAC assigns permissions based on predefined roles within an organization. Users are granted access according to their role rather than on an individual basis.
How it Works:
- Users are grouped into roles (e.g., “HR Manager,” “Finance Analyst”).
- Each role has a predefined set of permissions (e.g., HR Managers can view employee records, but Finance Analysts cannot).
- Access rights remain static unless roles change.
Example: A Hospital’s RBAC System
- Doctor: Can access patient records, prescribe medications, but cannot modify billing details.
- Nurse: Can access medical history but cannot prescribe.
- Billing Department: Can access payment information but not patient medical records.
When to Use RBAC
- Organizations with stable, well-defined roles (e.g., government agencies, enterprises with clear job functions).
- Where compliance & auditing are critical (e.g., financial services, healthcare).
- For managing large teams efficiently (RBAC simplifies provisioning & deprovisioning).
Limitations of RBAC
Lacks flexibility – Cannot adapt to dynamic access needs (e.g., temporary projects, contract workers).
Rigid structure – Requires manual updates when roles evolve.
Attribute-based access control (ABAC)
What is ABAC?
ABAC provides access control based on user attributes, resource attributes, and environmental factors (e.g., time, location, device).
How it Works:
- Instead of assigning static roles, access is determined dynamically using rules and policies.
- Attributes can include:
- User attributes (e.g., job title, security clearance).
- Resource attributes (e.g., document classification level).
- Environmental attributes (e.g., location, device type, time of access).
Example: A Global Financial Firm Using ABAC
- A trader in New York can access stock trading platforms through a centralized access management system. during business hours but is restricted from remote access on personal devices.
- The same trader, when traveling, is prompted for additional authentication (MFA) before accessing sensitive data.
When to Use ABAC
- For organizations with dynamic access needs (e.g., multinational corporations, cloud-based companies).
- Where context-aware security is required (e.g., location, device, and real-time behavior).
- For fine-grained control over access permissions (more flexibility than RBAC).
Limitations of ABAC
More complex implementation – Requires defining attribute-based rules and maintaining policy engines.
Increased computational overhead – Real-time policy evaluation can slow down access decisions.
RBAC vs. ABAC
| Factor | RBAC | ABAC |
|---|---|---|
| Best for… | Organizations with well-defined roles benefit from a decentralized access control system. | Organizations with dynamic access needs |
| Flexibility | Low – Static roles & permissions | High – Context-aware, real-time policies |
| Security Model | Least Privilege (fixed role-based) | Zero Trust (adaptive, rule-based) |
| Compliance | Good for regulatory compliance (e.g., HIPAA, SOX) | Better for granular security policies |
| Ease of Implementation | Simple (predefined roles & permissions) | Complex (requires attribute management) |
Hybrid approach – combining RBAC & ABAC
Many organizations use both models together to balance security and usability in a centralized vs decentralized access framework. This hybrid model allows RBAC for basic role assignments while ABAC adds dynamic, contextual controls within a centralized access control system..
Example: A Corporate IT System with Hybrid RBAC + ABAC
- RBAC assigns a base level of access (e.g., an “IT Support Engineer” role).
- ABAC refines access based on additional attributes (e.g., restricting system modifications to engineers working in a secure network environment).
Benefits of the Hybrid Model:
- Balances ease of management (RBAC) with dynamic security (ABAC).
- Ensures compliance while maintaining adaptive access controls.

Zero Trust IAM users see 70% fewer unauthorized access attempts
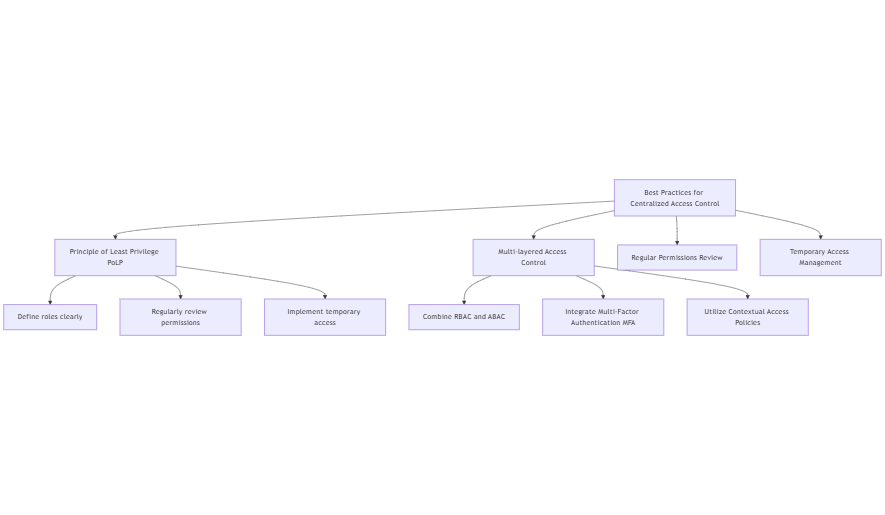
VIII. Best practices for centralized access control
Effective access control is crucial for organizations that want to boost security and simplify their operations. Based on my work with clients on identity and access management, here are some best practices to help IT leaders build strong access control strategies.
Principle of least privilege
The Principle of Least Privilege (PoLP) serves as a foundational guideline in access control. This principle means users should have just enough access to do their jobs. Following PoLP helps organizations lower the chances of unauthorized access and data breaches. Here are some key steps to implement PoLP:
- Define roles clearly: It’s crucial to establish distinct job roles within the organization and map out the necessary access permissions for each role.
- Regularly review permissions: Regularly checking user permissions keeps them in line with current job roles. Removing access for users who have changed roles or left the organization should be a priority.
- Implement temporary access: For special projects or temporary needs, providing time-limited access to sensitive resources guarantees that access is revoked once the need has passed.
Multi-layered access control
Multi-layered access control enhances security by integrating various access control methods to create a resilient framework. This approach enables organizations to add layers of security, making it harder for unauthorized users to get in. Here are some effective strategies:
- Combine RBAC and ABAC: Utilize Role-Based Access Control (RBAC) for baseline access permissions while incorporating Attribute-Based Access Control (ABAC) for more granular, context-aware access decisions. This hybrid model enables organizations to tailor access based on user attributes, roles, and environmental factors.
- Integrate multi-factor authentication (MFA): Implementing MFA strengthens security further. By requiring users to furnish multiple forms of verification, organizations can better shield against unauthorized access, even if credentials are compromised.
- Utilize contextual access policies: Craft policies that consider contextual factors such as user location, device health, and time of access. For example, if a user tries to access sensitive data from an unrecognized device or location, additional verification steps can be triggered.
Summary table of best practices
| Best practice | Description |
|---|---|
| Principle of least privilege | Grant users the minimum access necessary to perform their job functions. |
| Role definition | Clearly define roles and associated permissions for effective access management. |
| Regular permissions review | Periodically audit user access to ensure it matches current roles and responsibilities. |
| Temporary access | Provide time-limited access for special projects, ensuring access is revoked afterward. |
| Multi-layered access control | Combine multiple access control methods to enhance security. |
| RBAC and ABAC integration | Use RBAC for baseline permissions and ABAC for granular access decisions based on user attributes. |
| Multi-factor authentication | Implement MFA to require multiple forms of verification for accessing sensitive resources. |
| Contextual access policies | Establish policies that consider contextual factors for access decisions, enhancing security flexibility. |
Adopting these best practices helps organizations improve security and make user access management easier. As IT leaders evaluate their access control strategies, these guidelines serve as a solid foundation for building a resilient and efficient access management framework.
IX. The move towards passwordless authentication in centralized IAM
The limitations and risks of traditional passwords
Traditional passwords often hinder security efforts, as evidenced by numerous cases in identity and access management. Password-related data breaches pose significant risks, with many organizations facing incidents due to weak passwords and users reusing passwords across multiple accounts. Phishing attacks targeting organizations using Microsoft Active Directory Federation Services (ADFS) illustrate the vulnerabilities in conventional password systems, allowing cybercriminals to bypass even multi-factor authentication. ⁵
Common issues with traditional passwords:
| Issue | Description |
|---|---|
| Weak passwords | Many users opt for simple passwords that can be easily guessed or cracked. |
| Password reuse | Users often recycle passwords across multiple accounts, increasing vulnerability. |
| Phishing attacks | Attackers use deceptive methods to obtain user credentials, undermining security. |
| Data breaches | Organizations face significant risks from breaches due to compromised passwords. |
Benefits of passwordless authentication
Transitioning to passwordless authentication presents numerous advantages that not only enhance security but also improve the overall user experience. Eliminating passwords can reduce the risks linked to password management and streamline the user authentication process.
Key advantages of passwordless authentication:
- Enhanced security: Passwordless methods dramatically lower the risk of unauthorized access, as they remove the vulnerabilities linked to both password theft and phishing attacks.
- Improved user experience through a centralized management approach.: Users can enjoy a hassle-free login experience without the burden of remembering and managing passwords. This convenience often translates to higher satisfaction and productivity levels.
Passwordless authentication methods in centralized IAM
Organizations can choose from various effective methods for integrating passwordless authentication into their centralized IAM systems. Here are a few approaches:
- WebAuthn/passkeys: This method links user identity to a secure device for authentication, eliminating the need for passwords through public key cryptography.
- One-time passwords (OTP): Temporarily generated codes sent via SMS or email ensure that only the intended user can access their account during the login process.
- Magic links: Users can bypass passwords entirely by receiving an email with a unique link that grants them access to their accounts.
- Biometrics: Leveraging fingerprint or facial recognition technologies offers a secure and user-friendly approach to authentication, capitalizing on unique biological traits.
Integrating these passwordless authentication methods into centralized IAM solutions like Keycloak can strengthen security. Keycloak supports an array of authentication strategies, making it smoother for organizations to transition to a passwordless setup. By implementing these passwordless solutions, organizations can mitigate the risks associated with traditional passwords and ensure a seamless user experience.
X. Advanced topics and future trends in centralized access management
Identity orchestration
Identity orchestration is crucial for connecting different identity systems within Identity and Access Management (IAM). Integrating various Identity Providers (IDPs) into a unified framework enhances user access across platforms. This orchestration simplifies user experiences and strengthens security through consistent policy enforcement.
| Benefits of identity orchestration | Description |
|---|---|
| Unified user experience | Offers a seamless access experience across different systems and applications. |
| Improved security posture | Guarantees consistent application of security policies across all integrated systems. |
| Efficiency in identity management | Reduces administrative overhead by managing identities from a single interface. |
Federated identity management
Federated identity management (FIM) is essential for organizations seeking secure access across multiple domains. It enables users to authenticate once and access various services without managing multiple credentials. This improves user convenience and bolsters security by reducing the number of credentials to manage.
Inteca case study: The Economic Information Bureau successfully federated authentication with over 20 European banks, achieving an impressive 99.9% uptime for authentication services. This showcases how FIM can drastically improve operational efficiency and foster user trust in the system.
Insight: AI integration into identity management solutions enhances security and streamlines federated identity processes. AI’s capability to analyze user behavior and contextual information will allow for more dynamic and responsive access control measures. ⁶
AI and machine learning in IAM
AI and machine learning are transforming identity and access management in organizations. These technologies automate routine tasks, detect anomalies, and improve real-time decision-making. For example, AI can identify unusual access patterns that might indicate a security threat, facilitating quicker responses to potential breaches.
Key impacts of AI in IAM:
– Automation: Reduces the manual effort involved in identity management, enabling IT teams to concentrate on strategic initiatives.
– Enhanced security: Offers predictive analytics to foresee and mitigate potential security threats.
– Improved user experience: Enables faster access approvals and smoother user interactions with systems.
Continuous authentication and risk-based access
Traditional authentication methods often fail to meet current security challenges. Continuous authentication and risk-based access have become essential in modern security strategies. Continuous authentication involves ongoing verification of a user’s identity throughout their session, rather than just at the point of entry. This allows for monitoring and evaluation of contextual changes, such as location or device.
Importance in modern security strategies:
– Adaptive security measures: Organizations can adjust access levels based on real-time evaluation of user behavior and context.
– Enhanced protection against threats: Continuous monitoring aids in the swift identification and response to potential security breaches.
– User-centric approach: This strategy ensures security needs align with user experience, reducing disruptions while ensuring protection.
Reference List:
-
Defense One. (2025, February). Pentagon plans unified digital access tools across military branches this year. https://www.defenseone.com/defense-systems/2025/02/pentagon-plans-unified-digital-access-tools-across-military-year/403245/
-
Hayashi, K. (2025, March). CISOs should address identity management as fast as they can, says CrowdStrike exec. CSO Online. https://www.csoonline.com/article/3836917/cisos-should-address-identity-management-as-fast-as-they-can-says-crowdstrike-exec.html
-
Infosecurity Magazine. (2025, April). New phishing kit bypasses MFA by intercepting login credentials. https://www.infosecurity-magazine.com/news/new-phishing-kit-bypasses-mfa-2025
-
LayerX Research Team. (2025). The risks of SSO governance: Why identity security matters. LayerX. https://www.layerx.com/report-2025
-
SecurityWeek. (2025, May). AI integration in identity management solutions: Strengthening access control with machine learning. https://www.securityweek.com/ai-integration-identity-management-solutions
-
SecurityWeek. (2025, May). AI-driven governance frameworks: Automating compliance and risk management. https://www.securityweek.com/ai-driven-governance-frameworks
See how Inteca can help you boost cybersecurity