What is FIM and how does it work?
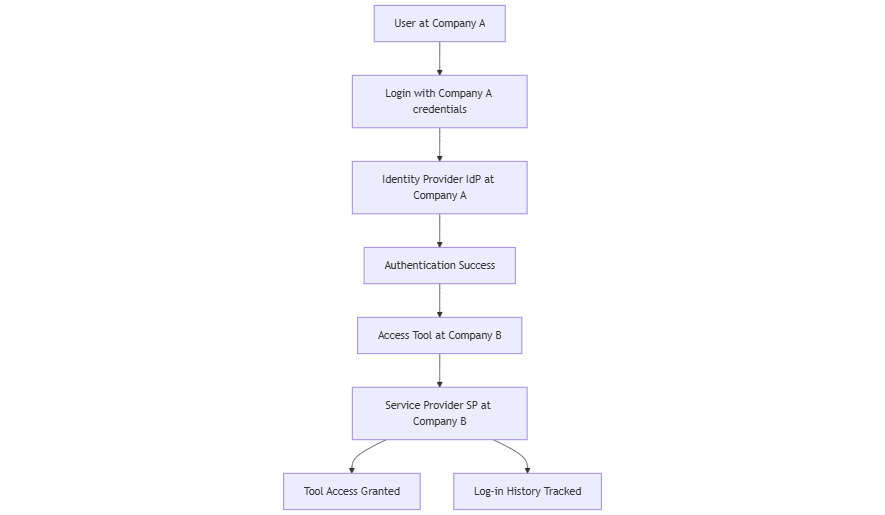
One of federated identity management real life example is when you work at Company A, and you need to use a tool made by Company B — let’s say it’s a cloud-based project management platform. Instead of creating a new username and password just for that tool, you simply log in with your Company A credentials. And you’re in, additionally company B can track you log-in history. Everything according to cybersecurity standards.
You didn’t have to sign up, create another password, or go through a whole registration process.
One login (your company or organization’s identity system) works across different websites, services, or companies — as long as they have a trust agreement. That’s the essence of federations.
This guide presents a comprehensive look at identity management federations, including its benefits, architecture, technologies, applications, and future trends.
What is the difference between SSO and federated identity?
Single sign-on (SSO)
One of the most valuable features of Identity Federation is Single Sign-On (SSO). This feature lets users authenticate once and access multiple applications without having to log in repeatedly. Not only does this simplify the user experience, but it also plays a crucial role in mitigating password fatigue, which can lead to poor security practices.
- Significance of SSO: SSO simplifies navigation for users, making it easier to transition between applications while ensuring a secure environment.
- Security benefits: By reducing the frequency with which users need to enter their credentials, SSO significantly lowers the chances of credential theft.
Federated identity vs. Single sign-on (SSO)
While Single Sign-On (SSO) allows users to authenticate once within a single domain and access multiple applications, Federated Identity Management (FIM) Federated authentication extends this functionality across multiple domains, simplifying user access. This ability allows users to access resources from various organizations without needing to manage multiple credentials.
| Feature | Single Sign-On (SSO) | Federated Identity Management (FIM) |
|---|---|---|
| Domain scope | Single domain | Multiple domains |
| User experience | Simplified access within an organization | Seamless access across organizations |
| Credential management | Centralized within one organization | Distributed across multiple IdPs |
| Trust model | Limited to one organization | Trust established between multiple parties |
Insight: Organizations must verify the legitimacy of identities accessing enterprise applications, particularly in SSO scenarios. That’s why we need safe identity verification processes in both SSO and federated systems to mitigate unauthorized access risks.
Core concepts of federated identity management
What is identity federation?
Identity Federation links a user’s electronic identity among multiple identity management systems, enabling secure access to resources across various domains or organizations. The fundamental principles of identity federation focus on effectively managing a user’s identity across different platforms.
What are the key components of federated identity management?
- Identity Providers (IdPs)These entities are essential for authenticating users and issuing identity assertions, which confirm the user’s identity to other systems, ensuring the integrity of their digital identity. They are responsible for maintaining the integrity of user credentials, ensuring that users are indeed who they claim to be.
- Service Providers (SPs): SPs rely on IdPs for user identity verification and resource access based on received assertions. This relationship is founded on mutual trust for exchanging credentials, allowing organizations to depend on each other’s verification processes. This collaboration enhances user experience while prioritizing security.
Authentication & authorization in federated systems
In federated systems, authentication and authorization are foundational processes. Here, identity providers authenticate users by validating their credentials, while SPs validate the identity assertions provided by the IdPs. This collaboration is crucial for allowing only authorized users to access sensitive resources.
Authentication frameworks not only shield user identities but also support the overall security of the federated system. For example, using multi-factor authentication (MFA) reduces the risk of credential theft by requiring users to provide additional verification.
Insight: A recent sophisticated phishing attack targeting Microsoft Active Directory Federation Services (ADFS) has brought to light vulnerabilities within federated systems, enabling attackers to bypass multi-factor authentication3 This incident highlights the need for organizations to regularly evaluate and strengthen their authentication practices against emerging security threats.
What are the benefits of federated identity management?
Cost savings and scalability
Federated Identity Management (FIM) offers significant cost benefits for organizations looking to simplify how they handle user identities. FIM reduces reliance on multiple authentication systems, leading to notable cost savings. Let’s explore some key financial benefits for organizations adopting FIM:
- Reduced operational costsWith FIM in place, the resources required to manage various identity systems are minimized, allowing for better allocation of identity information. Organizations can allocate their budgets more efficiently by consolidating their identity management infrastructure, which allows them to use their budgets more effectively.
- Lower helpdesk costs: Fewer passwords mean a drop in password-related support tickets. This translates to less time and money spent on helpdesk services, freeing up IT teams to focus on more critical projects.
- Scalable solutions: FIM solutions are built to scale alongside an organization. As businesses expand and evolve, they can seamlessly integrate new applications and services without the need for a complete overhaul of their identity management system. This flexibility helps organizations meet rising user demands while keeping extra costs low.
| Aspect | Traditional identity management | Federated identity management (FIM) |
|---|---|---|
| Initial setup costs | High (multiple systems) | Lower (consolidated approach) |
| Ongoing maintenance costs | High (multiple updates) | Reduced (single system maintenance) |
| Helpdesk support costs | High (password resets) | Lower (fewer credentials) |
| Scalability | Limited (difficult to integrate) | High (easy to add services) |
User convenience
Another key benefit of FIM is its enhancement of the user experience through the use of a trusted identity provider. Here’s how FIM contributes to a more user-friendly environment:
- Seamless access: With Single Sign-On (SSO) capabilities, users can log in once and access various applications seamlessly. This improves user satisfaction and productivity, allowing employees to focus on their work rather than managing multiple logins.
- Reduced IT overhead is one of the advantages of using a trusted identity provider for managing user credentials.: FIM simplifies access management, easing the workload for IT teams. With fewer access-related issues to troubleshoot, IT staff can concentrate on strategic projects rather than getting bogged down with daily credential management. This shift enables organizations to use their IT resources more efficiently.
- Enhanced security: With fewer passwords to remember, users are less likely to engage in insecure practices like password reuse. This overall reduction in password fatigue contributes to an improved security posture within the organization.
| User experience aspect | Traditional identity management | Federated identity management (FIM) |
|---|---|---|
| Login process | Multiple logins | Single sign-on (SSO) |
| User satisfaction | Often low (complexity) | High (simplicity) |
| Security practices | Risky (password reuse) | Improved (fewer passwords) |
| IT resource allocation | High (managing issues) | Optimized (focus on strategy) |
In summary, the benefits of Federated Identity Management include much more than cost savings. FIM not only enhances user convenience but also improves security, allowing organizations to operate more efficiently while ensuring a better overall user experience.
Technologies that make up federations
Federated Identity Management relies on several key technologies and standards to ensure secure and efficient identity verification and access control. Based on my experiences at Inteca, here are some significant protocols and tools central to FIM, along with their functionalities and applications.
Security assertion markup language (SAML) in federated identity
Security Assertion Markup Language (SAML) plays a critical role in the federated authentication process by enabling secure exchanges of identity information. is an XML-based protocol designed specifically for the secure transmission of identity and attribute data between identity providers (IdPs) and service providers (SPs). This protocol supports Single Sign-On (SSO), letting users authenticate once to access multiple applications. SAML is especially useful for enterprises that prioritize the integrity and reliability of identity assertions.
Is OAuth 2.0 a federated identity?
OAuth 2.0 is an authorization framework that allows applications to access user accounts on an HTTP service with limited permissions. It facilitates token-based access, enabling users to grant third-party applications access to their information without sharing their personal credentials. This flexibility makes OAuth 2.0 a preferred option for identity management solutions, particularly for mobile and web applications with diverse security requirements.
OpenID connect (OIDC) role
OpenID Connect (OIDC) builds on the OAuth 2.0 framework by adding an authentication layer. This allows clients to verify a user’s identity and obtain basic profile information. Utilizing JSON Web Tokens (JWTs), OIDC ensures secure and efficient data exchange, making it an excellent fit for federated identity solutions. It’s particularly useful for applications that require both authentication and authorization, creating a streamlined user experience across different platforms.
Shibboleth federated identity
Shibboleth is an open-source federated identity solution widely adopted in academic contexts. Implementing SAML, it provides a comprehensive framework for managing user identities across multiple institutions. Shibboleth enables secure resource sharing while safeguarding user privacy, serving as a valuable tool for educational collaborations and research initiatives.
Digital signatures
Digital Signatures play a vital role in ensuring the integrity and non-repudiation of identity assertions within federated systems. Digital signatures use cryptographic techniques to ensure that the transmitted information is intact and to confirm the sender’s identity⁵. This significant layer of security protects against forgery and unauthorized access, reinforcing the overall robustness of identity assertions.
| Technology/Standard | Description | Use Cases |
|---|---|---|
| SAML | XML-based protocol for secure identity transmission | Enterprise SSO, secure access management |
| OAuth 2.0 | Authorization framework for token-based access | Third-party access, mobile apps |
| OpenID Connect (OIDC) | Authentication layer on top of OAuth 2.0 | User identity verification, web services |
| Shibboleth | Open-source solution for federated identity management | Academic collaborations, resource sharing |
| Digital Signatures | Ensures integrity and authenticity of identity assertions | Secure communications, regulatory compliance |
These technologies and standards are essential for the effective implementation of Federated Identity Management. Using these protocols, organizations can boost security, enhance user experiences, and enable collaboration across various platforms.
What are the implementation models and architecture of federated IAM?
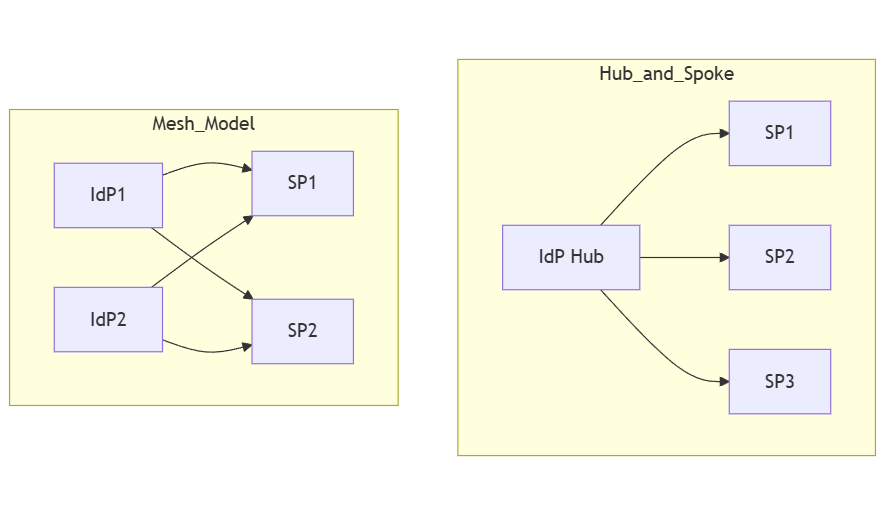
To implement Federated Identity Management (FIM) effectively, organizations should first examine the available architectural models and how these fit their specific requirements. The two predominant models are the hub-and-spoke and mesh architectures, each with their own benefits and challenges that IT decision-makers must weigh carefully.
Hub-and-spoke model
In the hub-and-spoke model, a central hub, usually an Identity Provider (IdP), orchestrates communication among various service providers (SPs). Many organizations prefer this approach for its simpler management stemming from centralization.
Pros:
- Centralized management: With all identity assertions funneled through a single point, it’s easier to implement and maintain.
- Reduced complexity: SPs only need to establish trust with the hub, minimizing the number of connections to manage.
Cons:
- Single point of failure: If the hub experiences downtime, access to all connected SPs could be jeopardized.
- Scalability issues: As the number of SPs grows, the hub can experience performance bottlenecks that directly impact system efficiency.
Mesh model
Alternatively, the mesh model promotes a decentralized network, allowing IdPs and SPs to connect directly and communicate independently.
Pros:
- Increased resilience: No single point of failure means that if one IdP or SP fails, the others remain operational.
- Scalability: This model scales effectively since each new connection adds minimal strain on the existing system.
Cons:
- Complex management: Setting up and maintaining this model can be more intricate, with each SP needing to establish trust with every IdP.
- Higher overhead: The necessity for numerous trust relationships can lead to increased administrative overhead.
| Model | Hub-and-spoke | Mesh |
|---|---|---|
| Management | Centralized, easier to manage | Decentralized, complex management |
| Resilience | Single point of failure | No single point of failure |
| Scalability | Limited scalability | Highly scalable |
| Trust relationships | Fewer relationships to manage | Many relationships to establish |
Trust establishment – metadata exchange
No matter which model is chosen, establishing mutual trust between IdPs and SPs is vital for ensuring secure communication. This process typically requires exchanging metadata that includes key details about endpoints, supported protocols, and the cryptographic certificates for signing assertions.
- Trust establishment: It’s important that IdPs and SPs verify each other’s security policies and compliance with standards, ensuring mutual trust.
- Metadata exchange: Regular updates and exchanges of metadata are necessary to maintain the integrity of the federated system, ensuring all parties are aware of the latest information.

80% of enterprise SaaS logins are invisible to IT and security teams
What are common federated identity management use cases?
Federated identity in education sector
Use case – Cross-institution access
In the education sector, federated identity enables students and faculty to easily access shared resources across different institutions. For instance, universities often collaborate on research projects, requiring shared access to databases and online resources. By implementing FIM, institutions can offer single sign-on (SSO), letting users log in once to access various services and eliminating the need to juggle multiple credentials. This approach improves user satisfaction and lightens the workload for IT departments.
Federated identities in healthcare example
Use case – Shared patient data access
In healthcare, doctors frequently require access to patient records that are shared among various hospitals and clinics. FIM makes it possible for healthcare providers to exchange patient records securely, all while adhering to standards set by regulations like HIPAA. For example, a doctor at one hospital can access a patient’s medical history stored in another facility without needing multiple logins. This interoperability boosts care coordination and patient outcomes by ensuring healthcare professionals can access critical information swiftly.
Example of federated identity in finance
Use case – Secure bank-to-bank access
In the financial sector, federated identity systems play a crucial role in providing secure access between banks. By collaborating on shared services, banks can use FIM to ensure secure user authentication across different institutions. For instance, a customer can access their accounts across different banks using a single identity, simplifying the experience while enhancing security measures through robust authentication protocols. This strategy enhances the customer experience while bolstering the security framework of financial institutions.
FIM in government use case
Use case – Access to government services
In government, citizens can log into multiple services across departments with a single federated identity. For example, a citizen can log in to a government portal to apply for benefits, renew licenses, or pay taxes without needing separate accounts for each service. By using FIM, governments can streamline user access, improve service delivery, and enhance security by ensuring that only authorized individuals can access sensitive information. This builds confidence in government services and streamlines efficiency in public administration, particularly through the use of federated authentication.
| Sector | Use case description | Benefits |
|---|---|---|
| Education | Cross-institution access for students and faculty | Improved user satisfaction, reduced administrative workload |
| Healthcare | Shared patient data access across hospitals | Enhanced care coordination, compliance with regulations |
| Finance | Secure bank-to-bank access for customers | Simplified user experience, strengthened security |
| Government | Access to various services across departments | Streamlined access, improved service delivery |
These real-world use cases demonstrate how federated identity management not only simplifies access but also enhances security and compliance across diverse sectors. As organizations continue to adopt FIM, the potential for improved collaboration and efficiency will only grow.
Is federated identity management secure?
In Federated Identity Management (FIM), ensuring robust security is essential. From my experience at Inteca, organizations depend more on federated systems and must adopt best practices to protect user identities and sensitive data. This section highlights key security considerations that IT leaders and security teams must prioritize.
Multi-factor authentication (MFA)
Multi-factor authentication (MFA) is a critical layer in strengthening federated security. By requiring users to provide multiple forms of verification, MFA significantly reduces the risk of unauthorized access. However, recent developments have changed how security measures are implemented. Recently, a new phishing kit named Astaroth has been identified, capable of bypassing MFA by intercepting login credentials and session cookies in real-time.⁶ This shows how effective MFA can be, while also emphasizing the need for ongoing vigilance and adaptation in security measures.
| Security measure | Description | Importance |
|---|---|---|
| MFA | Requires multiple forms of verification | Reduces risk of unauthorized access |
| Single factor authentication | Traditional username/password | High risk of credential theft |
Access control policies
Establishing access control policies is crucial for managing user access within federated systems. Two common strategies include:
– Role-based access control (RBAC): Access is granted based on the user’s role within the organization. This simplifies management but can result in granting excessive permissions.
– Attribute-based access control (ABAC): Access decisions are based on attributes (e.g., user location, device type). This offers more granular control but can be complex to implement.
Best practice: Regularly review and update access policies to adapt to changing organizational needs and compliance requirements.
Encryption – data protection
Encryption is vital for protecting data both at rest and in transit. Organizations should implement:
– Secure transmission protocols: Such as TLS for data in transit to prevent eavesdropping.
– Data minimization: Collect only the necessary information to reduce exposure.
– Anonymization: Use techniques to obscure user identities in datasets, minimizing risk in case of a breach.
| Data protection strategy | Description | Benefits |
|---|---|---|
| Encryption | Secures data during transmission and storage | Protects sensitive information |
| Data minimization | Limits data collection to essentials | Reduces exposure risk |
| Anonymization | Masks user identities in datasets | Enhances privacy protection |
Insider threats – risk management
Organizations need to stay alert to insider threats. These risks can come from employees or partners who have access. Effective strategies involve:
– Monitoring and alerts: Implement systems to detect unusual access patterns or behaviors.
– Role hygiene: Regularly review user roles and permissions to ensure they align with current responsibilities.
Insight: Establishing a culture of security awareness among employees can significantly mitigate risks associated with insider threats.
Common threats – misconfigurations
Organizations need to recognize common threats and misconfigurations that can undermine federated identity systems:
– Token forgery: Attackers may forge tokens to impersonate legitimate users.
– Rogue identity providers (IdPs): Unauthorized IdPs can trick users into providing credentials.
– Over-permissioned usersUsers with excessive permissions pose a significant risk if their accounts, which contain sensitive identity information, are compromised.
Best practice: Regular security audits and penetration testing are essential to uncover vulnerabilities and misconfigurations in federated systems.
A proactive approach to security in Federated Identity Management is essential to protect the user’s identity across multiple platforms. By implementing these best practices, organizations can significantly enhance their security posture and protect against evolving threats.
What are best practices for implementing FIM
Implementing Federated Identity Management (FIM) allows organizations to streamline user access while maintaining security standards. Based on my work with clients in identity and access management, I present a list of best practices to facilitate effective FIM implementation:
1. Establish clear objectives
Begin by clearly outlining your objectives to set a focused direction for FIM. Consider your goals for FIM – Is it to improve user experience, boost security, or meet compliance requirements? These goals will shape your strategy and decisions moving forward.
2. Choose the right identity providers (IdPs)
Choosing trustworthy IdPs is key to a successful FIM initiative. Ensure that your chosen IdPs comply with industry standards and have strong security measures. Take the time to evaluate potential IdPs thoroughly, focusing on their reputation, reliability, and security protocols.
3. Implement strong security protocols
Using established protocols like SAML, OAuth 2.0, and OpenID Connect ensures secure communication between IdPs and Service Providers (SPs). These protocols protect user identities and sensitive data during transactions. Here’s a quick overview:
| Protocol | Purpose | Key Feature |
|---|---|---|
| SAML | Authentication and authorization | Enables SSO across domains |
| OAuth 2.0 | Authorization framework | Allows limited access to third-party apps |
| OpenID Connect | Authentication layer | Verifies user identity and retrieves profile |
4. Foster user education and awareness
Educating users about FIM is crucial for a smooth transition. Providing training sessions can help users understand the benefits of FIM and how to effectively navigate the new system. This proactive approach will minimize resistance and encourage adherence to security protocols.
5. Monitor and audit regularly
Ongoing monitoring and regular audits are key to maintaining security and compliance. Implement tools that track user activities and flag any suspicious behavior. Regular audits help identify vulnerabilities and keep your FIM implementation compliant with security standards.
6. Ensure compliance with regulations
Keep updated on regulations such as GDPR to ensure your FIM implementation complies. This involves obtaining user consent for data sharing and implementing necessary data protection measures to safeguard user information.
7. Plan for scalability
As organizations grow, their identity management needs will evolve. Choose FIM solutions that can easily scale to accommodate new applications and users. This flexibility saves time and resources, directly supporting the organization’s growth.
AI-driven identity analytics are transforming how we detect threats and grant access
Compliance and regulation of federations
GDPR and privacy regulations
In Federated Identity Management (FIM), following regulations like the General Data Protection Regulation (GDPR) is essential for responsible data handling. Organizations should prioritize consent management and user control to ensure personal data is processed according to established legal standards. This requires obtaining explicit consent from users before processing their data and offering them clear options to manage their privacy settings.
Key considerations for GDPR compliance-
- User consent: It’s crucial that users are fully informed about how their data will be utilized and that their consent is secured before processing occurs.
- Data subject rights: Users need to have the rights to access, correct, and delete their personal data, along with a right to transfer their data where applicable.
- Data minimization: Organizations should only collect and process data that is absolutely necessary, which not only helps in compliance but also minimizes potential risks associated with data breaches.
| Compliance aspect | Description | Importance |
|---|---|---|
| User consent | Obtain explicit consent for data processing | Ensures lawful processing of personal data |
| Data subject rights | Rights to access, rectify, and erase data | Enhances user trust and compliance |
| Data minimization | Limit data collection to what is necessary | Reduces risk of breaches and legal penalties |
Insight: As regulations become stricter, organizations must improve their data governance practices in identity management. Staying proactive in these changes is essential to avoid penalties and to maintain user trust.
Government-wide initiatives un US
Government initiatives play a crucial role in influencing federated identity management. A prime example is the U.S. General Services Administration (GSA) FICAM program, which aims to establish a robust identity management framework across federal agencies. This initiative improves interoperability and secure access to government services, making identity verification efficient and compliant.
Key features of the GSA FICAM program-
- Interoperability standards: It promotes the adoption of standardized protocols to enable seamless identity verification among various agencies.
- Security frameworks: The program sets forth guidelines for secure data exchange and user authentication, significantly fortifying the overall security posture of government services.
Another noteworthy initiative is the eIDAS Regulation (electronic IDentification, Authentication and trust Services), which enables cross-border identity trust within the European Union. This regulation allows citizens and businesses to leverage their national electronic identification for accessing public services across other EU countries, fostering a more cohesive digital single market.
| Initiative | Description | Benefits |
|---|---|---|
| GSA FICAM | Framework for federal identity management | Streamlined access to government services |
| eIDAS Regulation | Cross-border electronic identification | Enhanced trust and interoperability in the EU |
These government initiatives underscore the importance of compliance and regulation in federated identity management. As organizations navigate through these frameworks, maintaining vigilance in aligning with regulatory mandates is essential for offering secure and efficient user access.

FIM scales with your organization — no need to reinvent access as you grow
What are the drawbacks of federated identity management?
As organizations implement Federated Identity Management (FIM), they encounter various challenges that can affect the effectiveness and security of their identity management strategies. IT leaders and security teams must grasp these challenges to effectively implement federated systems.
Privacy concerns
Managing user privacy is paramount in any identity management system, and FIM is no exception. Organizations must prioritize transparency, consent, and responsible data usage to protect user information. The Indian government’s expansion of Aadhaar authentication for businesses has raised significant privacy concerns due to the lack of defined guardrails to prevent misuse of biometric IDs.⁸ Establishing clear protocols and regulations is essential for safeguarding user data and ensuring compliance with privacy laws.
| Privacy Aspect | Considerations | Implications |
|---|---|---|
| Transparency | Clear communication about data usage | Builds trust with users |
| User consent | Obtaining explicit consent for data processing | Legal compliance and ethical responsibility |
| Data minimization | Collecting only necessary data | Reduces risk of breaches |
Interoperability and integration
Integrating different Identity Providers (IdPs) and Service Providers (SPs) across technology stacks can complicate security and compliance efforts. Organizations often struggle with ensuring that various systems can communicate effectively while maintaining security. Failure to manage this complexity may result in higher operational costs and increased security vulnerabilities.
Best practices for integration:
– Standardization: Utilize common protocols such as SAML, OAuth, and OpenID Connect to facilitate smoother integration.
– Regular audits: Conduct periodic assessments of integrated systems to identify and address interoperability issues.
– Training and support: Provide ongoing training for IT staff to ensure they are equipped to handle integration challenges effectively.
Trust exploitation and federation risks
Relying on external partners in a federated identity system creates risks related to trust and security. If a federation partner is compromised, it can jeopardize the security of the entire network. Organizations should actively guard against credential theft and unauthorized access from compromised IdPs or SPs.
Mitigation strategies:
– Robust vetting processes: Establish stringent vetting protocols for potential federation partners to ensure they meet security standards.
– Monitoring and alerts: Implement continuous monitoring systems to detect unusual access patterns or activities that may indicate a breach.
– Incident response plans: Develop comprehensive incident response strategies that outline steps to take in the event of a security breach involving a federation partner.
How we will use federated identity in future?
AI and ML integration
The future of federated identity management (FIM) will be significantly influenced by the integration of Artificial Intelligence (AI) and Machine Learning (ML). These technologies enhance security and streamline processes, making identity management more efficient and adaptable to new cyber threats.
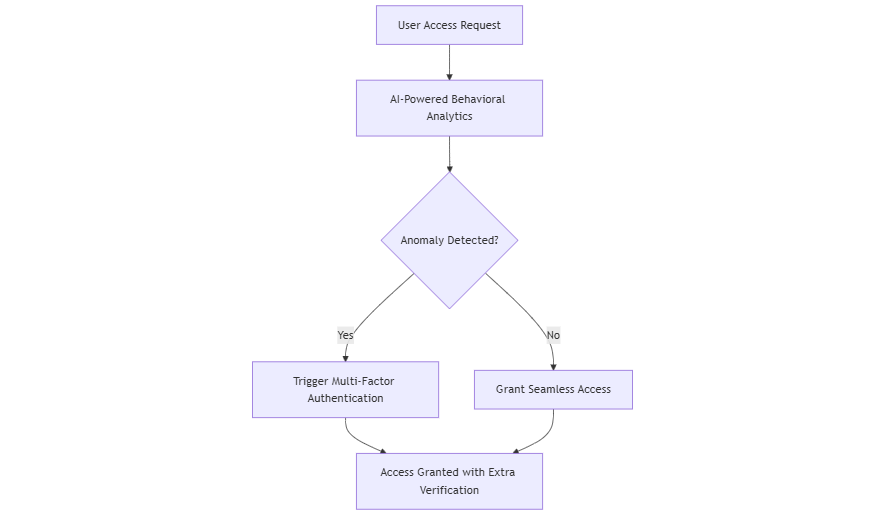
Behavioral analytics for anomaly detection
AI-driven behavioral analytics can significantly improve the identification of anomalies in user behavior. Organizations can analyze user patterns to spot deviations, allowing them to tackle security breaches before they become serious. For instance, if a user typically logs in from a familiar location but attempts to access their account from another country, the system can flag this for further investigation, significantly reducing the risk of unauthorized access.
Dynamic, risk-based authentication
Dynamic, risk-based authentication represents a significant advancement. This method evaluates the context of a user’s access request—considering factors such as location, device, and time—to determine the appropriate level of authentication required. For example, if a user attempts to access sensitive data from an unrecognized device, the system can prompt for additional verification. This method enhances security while simplifying the user experience during valid access attempts.
Summary
Here’s what stands out:
Key benefits of FIM
- Risk reduction – By centralizing authentication and implementing robust protocols, FIM significantly lowers the risks associated with credential theft and unauthorized access. This method guarantees that sensitive data remains secure from the start to the end of its use.
- Enhanced user experience – Users can access multiple platforms with a single login, easing the burden of remembering numerous passwords. This not only improves efficiency but also creates a more enjoyable experience for users.
- Simplified compliance – FIM simplifies auditing and reporting, enabling organizations to meet important regulations like GDPR. This streamlining allows for more efficient compliance management, reducing potential legal headaches.
Critical technologies to leverage
- SAML (Security Assertion Markup Language) – This XML-based protocol is essential for secure identity assertions between Identity Providers (IdPs) and Service Providers (SPs).
- OAuth 2.0 – As an authorization framework, OAuth 2.0 enables third-party applications to securely access user data without compromising credentials.
- OpenID Connect (OIDC) – Acting as an authentication layer atop OAuth 2.0, OIDC enhances security and user verification processes.
- Multi-factor authentication (MFA) – This vital security layer ensures that only authorized users gain access, bolstering protection against unauthorized attempts.
- Digital signatures – These are crucial in confirming the integrity and authenticity of identity assertions within federated systems.
Reference List:
-
The Enterprise Identity Threat Report 2025 – LayerX
https://go.layerxsecurity.com/enterprise-identity-threat-report-2024-unveiling-hidden-threats-to-corporate-identities -
Sophisticated Phishing Attack Targets Microsoft ADFS, Bypasses MFA – Infosecurity Magazine
https://www.infosecurity-magazine.com/news/sophisticated-phishing-attack-targeting -
New Astaroth Phishing Kit Bypasses MFA via Session Hijacking – Infosecurity Magazine
https://www.infosecurity-magazine.com/news/new-phishing-kit-bypasses-mfa-2025 -
India’s Aadhaar Expansion Raises Privacy Concerns Over Biometric Misuse – TechCrunch
https://techcrunch.com/2025/02/indian-aadhaar-authentication-privacy-concerns/
See why Inteca can handle large-scale IAM federations