Organizations may find it difficult to manage user identities and access rights. Centralized Identity and Access Management (IAM) systems provide a solution to these challenges. These systems significantly improve security by simplifying the management of user identities and access permissions while ensuring compliance. The below checklist is designed for IT managers, security architects, and procurement teams to help them evaluate and select the right centralized IAM solution.
Centralized access directory
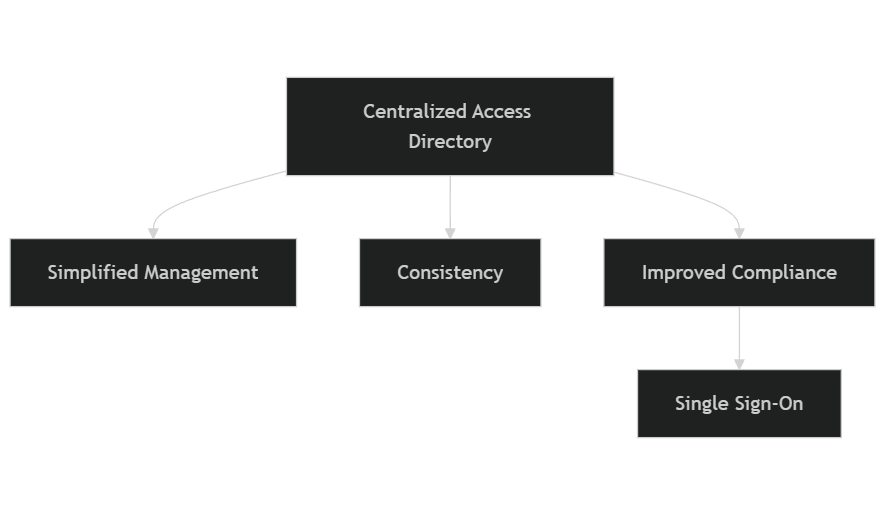
The Centralized Access Directory plays a crucial role in a successful Identity and Access Management (IAM) system. It serves as a single source for user identities, roles, and permissions, simplifying access management and enforcing the principle of least privilege. By consolidating user data, organizations can improve security measures and increase operational efficiency.
A unified repository offers numerous advantages:
– Simplified management: Administrators can oversee user access from one centralized platform, cutting down the complexity associated with juggling multiple directories.
– Consistency: This structure guarantees consistent implementation of security policies throughout the organization, lowering the chances of unauthorized access.
– Improved compliance: It aids in meeting regulatory requirements by offering clear audit trails and strong access controls.
A key benefit of a centralized access directory is Single Sign-On (SSO). With SSO, users can access multiple applications using just one set of credentials, making the login process much smoother and enhancing overall user experience. This simplifies the login process and enhances productivity, as users only need to remember one password.
An interesting example is the initiative being developed by the Pentagon’s IT agency. They are developing a simplified identity solution for various military departments, aiming to enhance digital identity verification on unclassified networks. This initiative underscores the importance of a centralized approach to identity management in large organizations.¹
User provisioning and lifecycle management
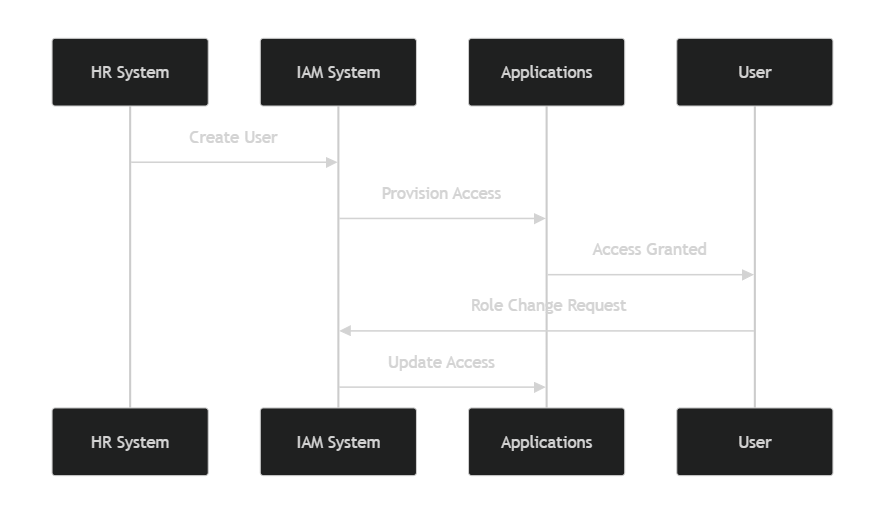
Automated User Provisioning is a highly beneficial feature of centralized IAM systems. It smooths out user account management by automating several processes:
– Onboarding and offboarding: New hires can gain immediate access upon joining, while access is automatically revoked when they leave. This significantly reduces the risk of unauthorized access during onboarding and offboarding.
– User lifecycle management: As roles change, so too do permissions. Automated systems ensure that user access is updated in real-time, maintaining security and compliance throughout an employee’s time with the organization.
– Efficiency boost: With automation handling repetitive tasks, IT teams can redirect their focus toward more strategic initiatives that require their expertise.
User lifecycle management include the oversight of user identities throughout their entire possesion within the organization. This ongoing process affect actively monitoring user activities and recalibrating access rights in response to changes in responsibilities. Proper management of the user lifecycle empowers organizations to:
– Ensure compliance with regulations through the consistent application of effective access controls.
– Enhance security by conducting regular audits and swiftly revoking access rights as soon as they are no longer necessary.
– Improve user satisfaction by guaranteeing quick access to essential resources.
An alarming statistic reveals a significant challenge: 80% of enterprise SaaS logins go unnoticed by IT and security teams, mainly due to personal credentials or accounts without SSO support.² This emphasizes the urgent necessity for strong user provisioning and lifecycle management to ensure transparency and control of user access.
Lower IT costs
Another key aspect of centralized IAM is that it provides self-service features. These allow users to manage routine tasks—like resetting passwords or requesting access—without needing to call on IT support. This increases user satisfaction and reduces helpdesk requests, freeing up IT resources. For instance, companies implementing self-service password management frequently see a 30% decrease in helpdesk calls, allowing IT staff to focus on more strategic initiatives.
Centralized IAM systems offer significant financial advantages. By simplifying identity management and reducing dependency on external vendors, organizations can achieve substantial cost savings. The following comparison highlights the cost differences between traditional and centralized IAM approaches:
| Cost factor | Traditional IAM | Centralized IAM |
|---|---|---|
| Helpdesk support costs | High | Low |
| Outsourcing expenses | Significant | Minimal |
| Administrative overhead | High | Reduced |
| Compliance auditing | Frequent & costly | Streamlined & cost-effective |
Implementing self-service capabilities and reducing operational costs makes centralized IAM a key driver of productivity. This system also offers a solid return on investment, making it a smart choice for organizations looking to optimize IT spending.
Investing in a centralized IAM solution leads to sustained financial benefits. Organizations can expect a positive return on investment as they reduce operational expenses and enhance productivity. By minimizing the time spent on identity management, IT departments can redirect their focus to strategic initiatives, which enhances overall operational efficiency.
Operational efficiency
Centralized IAM systems simplify managing user access across different applications and platforms. By consolidating access management into one interface, IT teams can manage user permissions more effectively and reduce the complexity of overseeing various systems. This method enhances efficiency and decreases the likelihood of errors associated with manual management.
A notable feature of centralized IAM is its capability to monitor user activities in real-time. This capability allows organizations to quickly address security incidents and suspicious activities. With clear visibility into user actions, IT teams can efficiently enforce security policies, which reduces the risk of breaches and strengthens overall security.
Centralized IAM systems simplify user and access management tasks for IT departments. Automated user provisioning and de-provisioning allow IT staff to focus on strategic initiatives instead of routine administrative tasks. This enhances efficiency and enables IT teams to allocate resources towards more impactful projects.
Improved security
Through my work on identity and access management projects, I’ve recognized that enhanced security is vital for organizations using Centralized Identity and Access Management (IAM) systems. These systems protect sensitive information while strengthening the overall security framework. Let’s dive into the key elements that contribute to this enhanced security.
Data encryption is fundamental to any effective IAM system. By ensuring that data is encrypted both in transit and at rest, organizations can safeguard sensitive information against unauthorized access. This layer of protection is crucial for preventing data breaches and ensuring user identity integrity.
IAM systems play a crucial role in combating identity theft. Features like multi-factor authentication (MFA) greatly reduce the risk of unauthorized access. MFA requires users to authenticate through multiple methods, making it much more challenging for attackers to gain access, even if they’ve managed to capture user credentials.
Recently, a sophisticated phishing attack targeting Microsoft Active Directory Federation Services (ADFS) was reported, revealing that attackers could bypass multi-factor authentication. This incident highlights the need for organizations to regularly update security measures and educate users on emerging threats. Keeping a vigilant and proactive stance in security strategies is essential to effectively mitigate such risks3 .
Regulatory compliance
Regulatory Compliance is a fundamental aspect of centralized IAM systems:
– Supports Compliance: These systems help organizations adhere to various regulations by maintaining comprehensive audit trails and access controls. This is crucial for demonstrating compliance during audits.
– Importance of Compliance: In the current regulatory environment, compliance is crucial to avoid penalties and safeguard an organization’s reputation.
Keycloak as centralized IAM
Following table outlines the essential features of Keycloak – centralized IAM system:
| Feature | Description | Benefits |
|---|---|---|
| Centralized access directory | A unified repository for user identities, roles, and permissions. | Simplifies access management and enforces least privilege. |
| Automated user provisioning | Streamlines user account management, automating onboarding and offboarding. | Ensures proper access from day one and revocation upon exit. |
| Efficient administration | Reduces IT workload by simplifying user and access management. | Frees up IT resources for strategic initiatives. |
| Enhanced security | Incorporates multi-factor authentication and consistent policies. | Mitigates security breaches and ensures compliance. |
| Cost savings | Centralized control reduces outsourcing and maintenance costs. | Long-term financial benefits through operational efficiency. |
Using Keycloak as a centralized IAM solution allows organizations to strengthen security and boost operational efficiency, proving invaluable for IT managers, security architects, and procurement teams. Centralized IAM systems play a crucial role in enhancing security and efficiency, effectively managing user identities and access. These systems improve security, simplify user access, and help meet regulatory requirements, which makes them essential for organizations.
While centralized IAM systems offer many benefits, organizations face challenges like user lifecycle management, new application integration, and legacy system compatibility. A key challenge is managing a coherent view of user data, which can become complicated as companies move from on-site to cloud storage. Legacy platforms pose significant hurdles in effectively implementing centralized IAM systems.
A checklist for beneficial centralized IAM solution:
Centralized Access Directory
- Establish a unified repository for user identities, roles, and permissions.
- Implement Single Sign-On (SSO) for seamless access to multiple applications.
User Provisioning and Lifecycle Management
- Automate onboarding and offboarding processes to manage access efficiently.
- Conduct regular audits to monitor and adjust access rights.
Lower IT Costs
- Enable self-service features for password resets and access requests.
- Reduce administrative overhead through automation of routine tasks.
Operational Efficiency
- Consolidate access management into a single interface for IT teams.
- Automate user provisioning and de-provisioning tasks.
Regulatory Compliance
- Maintain comprehensive audit trails for all access activities.
- Implement access controls aligned with regulatory requirements.
Reference List:
- Defense One, https://www.defenseone.com/technology/2025/02/pentagons-it-agency-streamlines-identity-solution/365123/
- CSO Online, https://www.csoonline.com/article/3836917/cisos-should-address-identity-management-as-fast-as-they-can-says-crowdstrike-exec.html
- Infosecurity Magazine, https://www.infosecurity-magazine.com/news/phishing-attack-targets-adfs-users-2025
See why Keycloak may be the best choice for centralized IAM solution