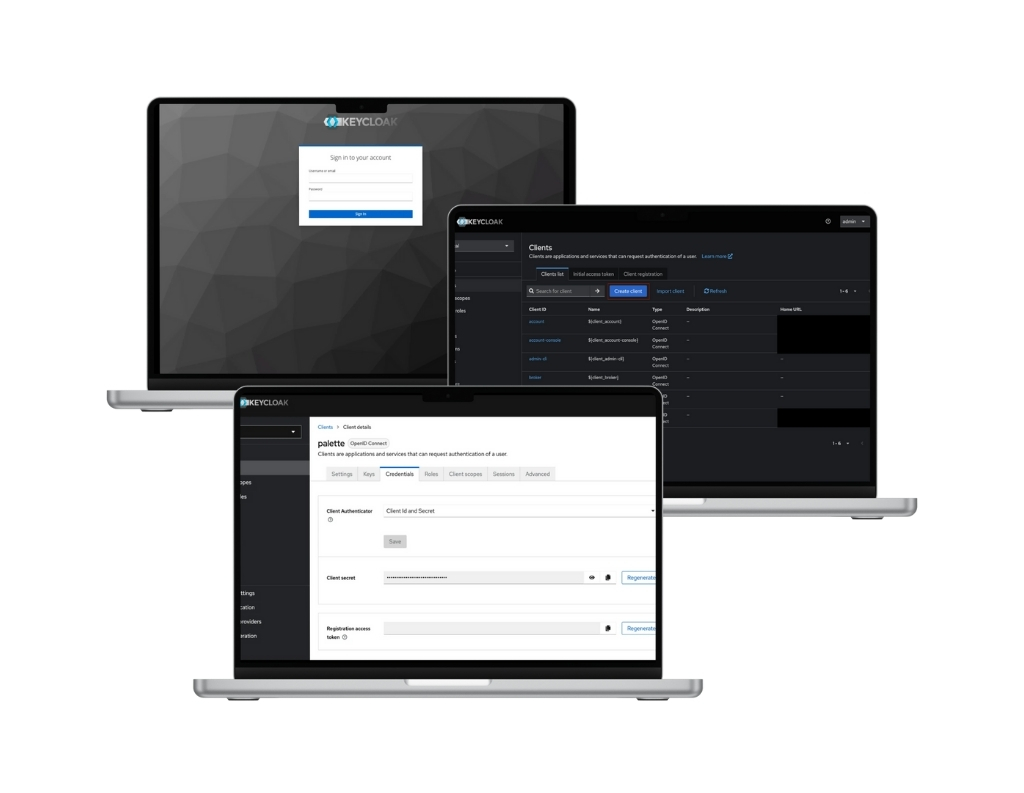
Enterprise SSO provider
Enterprise SSO: Single Sign-On for Secure and Efficient Enterprises
Enterprise SSO is a critical component of Identity and Access Management (IAM) for modern organizations. It allows users to authenticate once and then access multiple applications seamlessly, without re-entering credentials. For enterprises, this means improved security, better control, and greater operational efficiency. Inteca provides tailored, enterprise-grade SSO solutions—based on Keycloak.
Let’s talk about your project
What is Enterprise SSO and why does it matter for your business?
Enterprise SSO simplifies access and enhances security, making it an indispensable tool for modern businesses looking to streamline operations and fortify their digital defenses.
Definition of Enterprise SSO
Enterprise SSO enables users to access multiple applications and services within an organization after a single authentication.
Key Benefits of Implementing Enterprise SSO
Discover the transformative advantages Enterprise SSO brings to your organization:
Simplified Login and Enhanced User Experience
Single login improves speed and convenience.
No need to remember multiple passwords.
Boosted productivity through faster access.
Improved Security
Centralized identity and access management.
Reduced risk of data breaches and phishing.
Enforcement of strong password policies, security protocols, and MFA.
Faster onboarding and offboardi
Greater IT Efficiency and Control
Automated user lifecycle management (onboarding, offboarding).
Centralized access policies and controls.
Reduced IT support burden for password-related issues.
Regulatory Compliance
Helps comply with GDPR, HIPAA, ISO 27001.
Complete auditability and activity tracking.
Lower Operational Costs
Fewer helpdesk tickets for password resets.
Streamlined access management.
Enterprise identity security in numbers
Understanding the critical landscape of identity security challenges:
High-Risk Users
2% of users are high-risk, accounting for 70% of security incidents. (Source: Verizon Data Breach)
Unmonitored Logins
66% of security incidents stem from unmonitored privileged access.(Source: Forrester Research)
Phishing Attacks
50% of phishing attacks aim at stealing credentials. (Source: Gartner)
Weak passwords
54% of data breaches caused by weak, stolen, or reused passwords. (Source: FIDO Alliance)
Reduce your risk today!
Talk to our experts and discover how we handle everything – from seamless SSO deployment to 24/7 identity management support.
How Does Enterprise SSO Work?
Implementing SSO is based on a standardized process of authentication, token verification, and access distribution—providing seamless login for users and full visibility for administrators.
SSO Workflow
From Authentication to Access
Central Authentication
Users log in to a centralized authentication system (IdP) – often a robust platform like Keycloak, or your existing infrastructure such as Active Directory, Azure AD
Token Verification and Issuance
After verifying credentials, the IdP issues a secure token (e.g., SAML Assertion, OIDC Token) that confirms the user’s identity.
Seamless Access to Applications
The token is passed to connected enterprise applications, granting access without requiring re-authentication.
Centralized Access Management
Admins manage access policies, roles, and privileges from a unified console.
Core Enterprise SSO Components we integrate
Inteca ensures complete SSO integration with your existing IT infrastructure, supporting all major protocols and access control mechanisms.
Inteca specializes in integrating your existing identity stores with a Keycloak – centralized SSO platform to manage access to all your applications.
- Active Directory (AD), SAP, and Oracle for enterprise-wide identity management.
- LDAP, Azure Active Directory, Google Workspace
- Industry-Standard Authentication Protocols: SAML 2.0, OAuth 2.0, OpenID Connect – for cloud and SaaS applications.
- Integration with DevOps and Kubernetes – ensuring secure identity management in dynamic cloud infrastructures
Advanced Authentication Methods
Our solutions integrate cutting-edge authentication mechanisms for enhanced security and user convenience
- Access Control Mechanisms: Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), Conditional Access (e.g., based on location, device, or time).
- We support Multi-Factor Authentication (MFA) via mobile apps, SMS, email, and hardware tokens to provide robust security layers.
- Advanced Authentication Methods: Biometrics – Fingerprint, Face ID, and retina scan authentication, Passkeys & Public-Key Cryptography – Stronger, passwordless security for the modern web, Magic Links & OTPs – authentication without traditional credentials, Hardware Tokens & Smart Cards – Providing robust, phishing-resistant security
Why Implement Enterprise SSO with Inteca?
Inteca delivers full lifecycle SSO projects—from assessment and architecture to integration, support, and continuous monitoring. Partner with us for a seamless and secure transformation.

Proven experts
We have proven expertise in implementing SSO, IAM, MFA, and federations in highly regulated financial environments.

Tailored Solutions and Integrations
Designed to fit your unique environment: seamless integration with SAP, cloud systems, legacy applications, and more.
Continuous optimization & 24/7 support
SLA-backed, 24/7 support and proactive monitoring ensure continuous operation and peace of mind.

Scalability without limits
Our solutions are tested with 1M+ user databases, guaranteeing growth as your business expands.
Related Services
Frequently Asked Questions (FAQ) about Enterprise SSO
Ready to Deploy Enterprise SSO with Inteca?
Contact us today to learn how we can simplify access and strengthen data security in your organization with our expert Enterprise SSO solutions.