The demand for secure and user-friendly authentication methods is growing, with passwordless authentication being a key solution. Key features of well picked passwordless authentication solution include biometric authentication, fingerprint scanning, facial recognition and enhanced security through public key cryptography. These methods protect sensitive information and make access easier for users.
You should consider security enhancements and compliance factors when tackling identity and access management complexities. So stick around as we break down these important features that can elevate your approach to security and usability in the realm of passwordless solutions and stay in for a bonus point!
Interested in Keycloak Managed Service?
Key must-have features of your passwordless solution
In my experience as a marketer at Inteca, where I’ve collaborated with many clients on identity and access management projects, I’ve identified several must-have features that not only support security but also enhance the overall user experience. Here’s a closer look at these essential components:
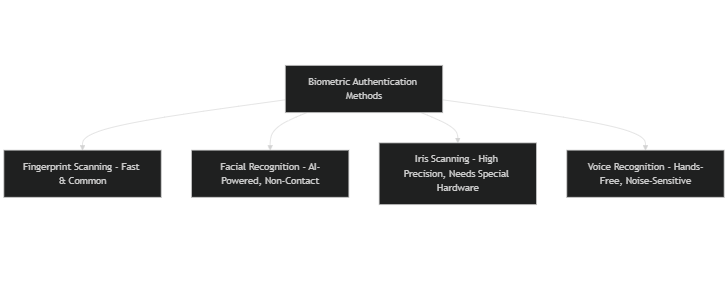
1. Biometric Authentication
Biometric authentication stands at the forefront of passwordless solutions. It utilizes distinctive physical traits for identity verification, ensuring both security and convenience. Your users will thank you for these options:
- Fingerprint scanning is a key component of a passwordless authentication method. – widely used and quick, it’s a staple in smartphones.
- Facial recognition – this non-contact method has significantly evolved with advancements in AI technology.
- Iris scanning – although it offers high precision, it typically requires advanced hardware.
- Voice recognition – a handy option for hands-free access, though it can be susceptible to background noise interference and may benefit from multi-factor authentication.
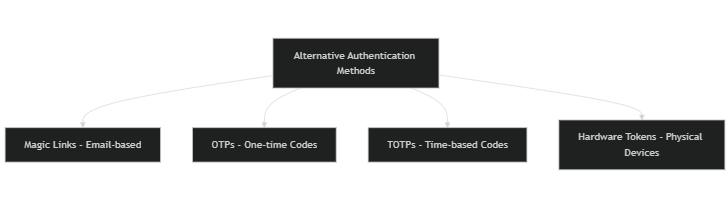
2. Alternative authentication methods
While biometrics are powerful, having alternative methods enriches the authentication landscape. Here are some notable techniques:
- Magic Links – a passwordless authentication method that simplifies user access. They simplify the login experience by sending users a one-time link via email.
- One-Time Passwords (OTPs) – Temporary codes sent directly to users act as a hardware token, adding an extra layer of protection.
- Time-Based One-Time Passwords (TOTPs) – These are generated based on time intervals, enhancing security further and can be used as a temporary credential.
- Hardware Security Tokens – these physical devices create unique codes, strengthening security for critical systems.
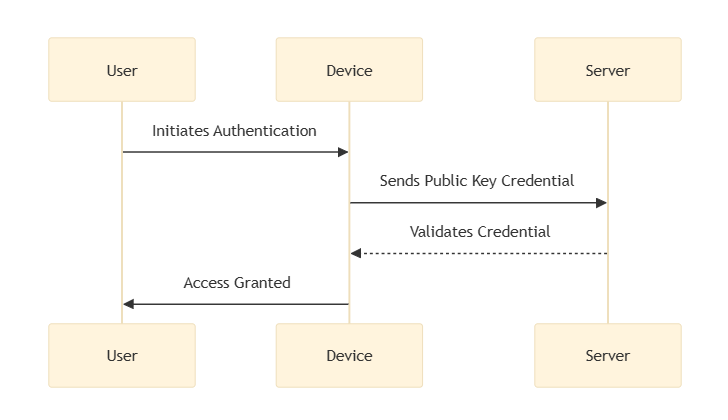
3. FIDO2/WebAuthn support
Integrating FIDO2 and WebAuthn security protocols require standards such as multi-factor authentication and password management. This set of standards enables strong, passwordless authentication. By allowing users to authenticate using devices like smartphones and security keys, it ensures that sensitive information remains locally stored and protected by a private key. Adopting these standards reduces the risks associated with phishing and boosts user confidence in the authentication process.
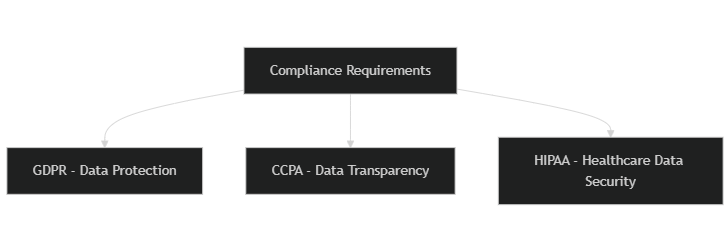
4. Compliance and regulations
Any solution you consider have to be compliant with regulations, so your passwordless solution should:
- Conduct data protection impact assessments to evaluate the effectiveness of multi-factor authentication strategies. These assessments help identify and mitigate potential risks.
- Meet GDPR compliance – This ensures user data is protected in accordance with European regulations and aligns with passwordless authentication methods.
- Adhere to CCPA compliance – essential for maintaining transparency with California residents regarding their data.
- Fulfills HIPAA compliance – particularly crucial for healthcare organizations that manage sensitive patient information.
5. Same-Device vs. Cross-Device Authentication (CDA)
It’s important to understand how authentication varies across devices:
– Same-Device Authentication is a convenient option for hands-free access, though it can be susceptible to background noise interference and may require an additional authentication factor. offers a straightforward experience when users log in on their primary devices.
– Cross-Device Authentication poses challenges like maintaining security across various platforms, but solutions such as session management, device fingerprinting, and multi-factor authentication can effectively address these issues.
6. **Bonus point** Security enhancements
To protect sensitive data, advanced security features are a necessity. Look out for:
- Advanced encryption techniques that safeguard data during both transmission and storage.
- Biometric template protection ensures that any stored biometric information is difficult to compromise and adheres to multi-factor authentication standards.
- Cancelable biometrics provides users the ability to alter their biometric templates if they believe they have been compromised, adding an extra layer of security.
Key Takeaways
When evaluating a passwordless authentication solution, it’s essential to keep these key takeaways in mind:
-
Look for solutions that include effective biometric methods, like fingerprint scanning and facial recognition, which not only elevate security but also enhance user convenience.
-
Consider options such as magic links and one-time passwords (OTPs) that simplify the login experience while maintaining security standards. This variety caters to different user needs and preferences.
-
Prioritize solutions that align with FIDO2 and WebAuthn. These standards ensure that authentication data stays on the user’s device, significantly decreasing the chances of data breaches.
-
Ensure that the solution adheres to necessary compliance requirements like GDPR, CCPA, and HIPAA to protect user data and maintain trust within your organization.
-
Evaluate whether the solution supports both same-device and cross-device authentication, allowing users to access services seamlessly across various platforms with multi-factor authentication.
By focusing on these critical elements, you can select a passwordless authentication solution that strengthens security while also improving user satisfaction and compliance with regulations in your organization.
See why Keycloak may be the best choice for your passwordless login needs!