Passwordless authentication with WebAuthn and passkeys is transforming how users access their accounts. With this approach, we’re stepping away from the clunky traditional password systems that often complicate user experience and increase security risks. Passwordless methods enhance security by reducing threats associated with password theft and phishing and also enhance the user experience by making logins simpler and faster. Using Keycloak, organizations can tap into various passwordless options, including biometrics and security keys, therefore streamlining access while ensuring they stay compliant with industry regulations.
Why it is even important?
Passwordless authentication benefits are balancing between security and user experience. By removing the need for complex passwords, we can ease the cognitive load on users, leading to quicker logins and greater satisfaction. This is especially important for businesses focused on engaging customers. On the security side, passwordless solutions minimize vulnerabilities linked to passwords and align with compliance mandates like GDPR and PSD2. As we dive deeper into how Keycloak supports these innovative authentication methods, it becomes clear that the future of secure access lies not just in data protection but in creating a smooth user experiences.
What is Keycloak?
It is Red Hat open-source identity and access management (IAM) solution. Keycloak is all about simplifying the authentication process while strengthening security. I’ve seen firsthand how it provides a robust platform for managing user identities. It enables organizations to manage user’s identities and permissions. It acts as a centralized system for user authentication and authorization, allowing businesses to simplify security processes, and integrate company platforms login without compromising on user experiences. By using industry-standard protocols like OpenID Connect, OAuth 2.0, and SAML, Keycloak facilitates secure interactions between users and applications, making it a go-to choice for many companies.
How Keycloak support passwordless authentication?
Keycloak provides a infrastructure that enables organizations to adopt passwordless authentication, incorporating methods like biometrics, authentication key, and one-time codes. Leaning on industry standards such as WebAuthn and FIDO2. These authentication methods are not only secure but also compliant with essential regulations.
WebAuthn & Keycloak
WebAuthn is a web standard designed to facilitate secure passwordless authentication through public key cryptography. Essentially, it allows users to log in using devices like smartphones or credential key without entering a password. This simplifies the user experience and adress the risk of phishing attacks. In Keycloak, implementing WebAuthn is straightforward. Administrators can easily configure this option in the Keycloak admin console, enabling users to register devices for secure authentication using authenticators. It’s a great step toward making user logins both secure and simply to maintain.
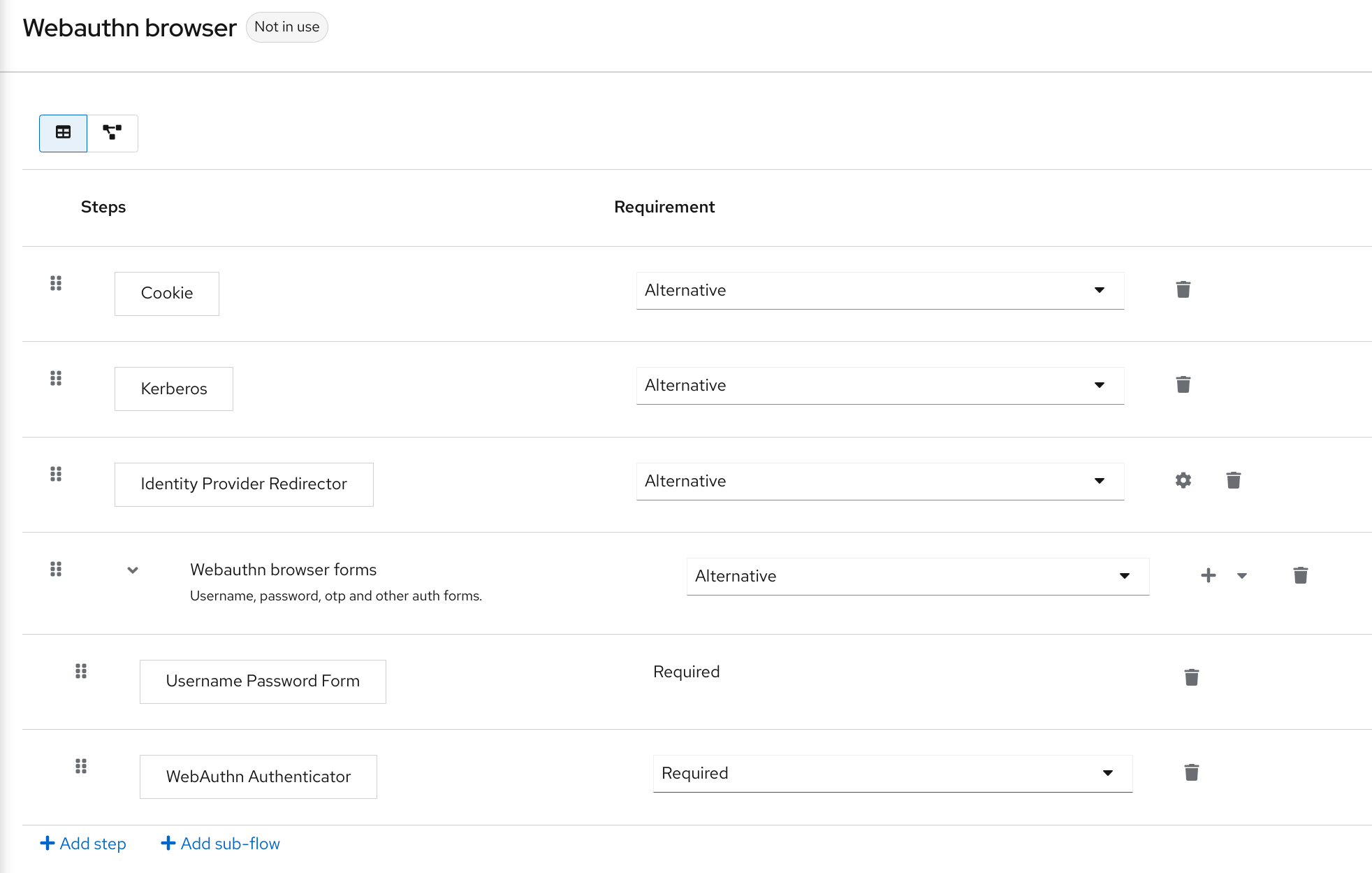
Image source: www.keycloak.org
FIDO2 & Keycloak
FIDO2 standard is a set of specifications that takes passwordless authentication to the next level using hardware security keys or identification data. Building upon the WebAuthn standard, it provides a robust framework for ensuring strong user verification. Keycloak integrates FIDO2 authentication, allowing organizations to leverage this advanced access control mechanism. With FIDO2 security enabled users can authenticate easily using their security token or biometric-based devices, boosting security while simplifying the login process.
No-password verification approach in Keycloak
Organizations can easily choose their authentication flow. Possession-based factors, such as security tokens, play a significant role in modern authentication flows, you can choose options that best suit your users:
- Biometric authentication – this feature allows users to access systems using fingerprint or facial recognition, providing a fast and secure entry point.
- Security keys – with hardware tokens, Keycloak adds an extra layer of protection, ensuring that only authorized users can log in.
- One-time codes (OTP) are a crucial part of many authentication flows. sending temporary codes via SMS or email for verification is another option that enhances security without complicating user access.
- Passkey – a modern approach to password-free access, utilizing cryptographic keys instead of traditional passwords.
- And many more…
Biometric authentication
Biometric methods include fingerprint scanning, facial recognition, and even iris scanning. These approaches utilize unique biological traits for user verification, offering a high level of security. Keycloak can work with various biometric-based authentication solutions, enabling organizations to incorporate these authenticators into their access strategies. Integrating biometrics not only enhances security but also streamlines the overall user experience—a win-win for any organization.
Security keys
Encryption key are physical devices that add an extra layer of protection for user authentication. They can be paired with other methods to securely verify user identities, improving overall security. In Keycloak, users can register their security keys directly in the interface, making it easy to implement two-factor authentication or passwordless logins. This straightforward approach provides both simplicity and security – a perfect combination for user authentication.
Magic link authentication
Magic link authentication works by sending users a one-time link via email for logging in without a password, streamlining the authentication flow. This method is not only convenient but also secure, as it eliminates the need for users to remember passwords. Keycloak supports magic link authentication, allowing organizations to provide a passwordless login experience that’s especially beneficial for applications prioritizing user convenience, such as e-commerce sites or online services.
Interested in Keycloak Managed Service?
Passkey
Passkeys represent a modern approach to credential-free authentication, utilizing cryptographic keys instead of traditional passwords. They significantly simplify the login process while offering enhanced security against phishing and credential theft. Keycloak not only supports passkeys but also encourages organizations to adopt this innovative method. Incorporating passkeys can lead to a more seamless and secure user experience, moving us further away from the burdensome reliance on passwords.
Comparison of passwordless to other authentication methods?
When comparing identity confirmation process, it’s crucial to see how keyless authentication differentiates itself from traditional password-based systems. Here’s a look at the key distinctions in authentication with Keycloak.
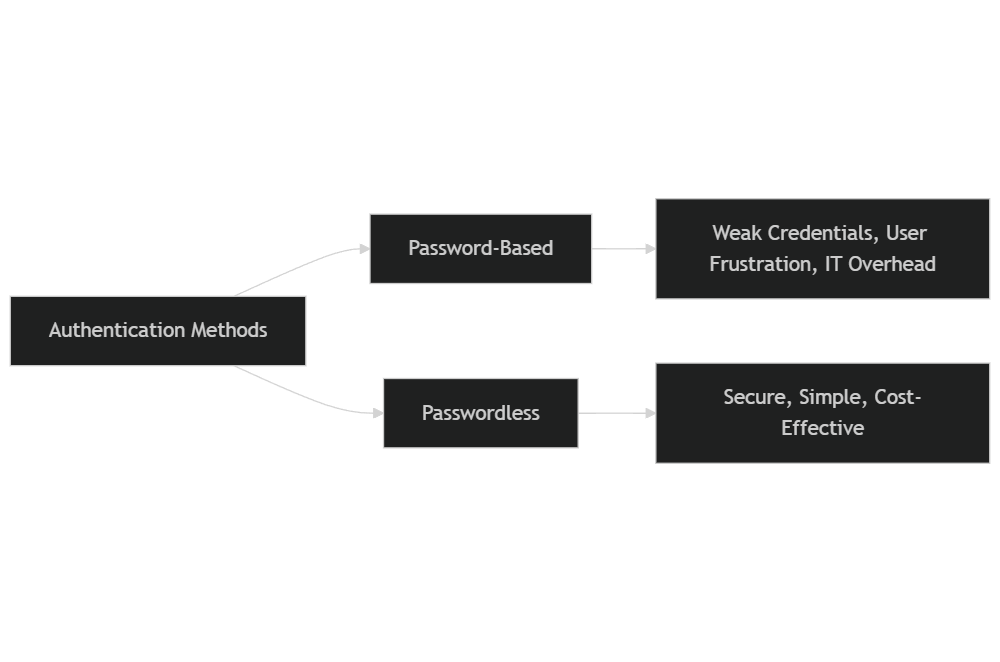
Traditional password-based systems
- Vulnerabilities – many users still rely heavily on passwords, often opting for weak, reused, or easily guessed credentials. This creates major security vulnerabilities that can be exploited by cybercriminals.
- User experience – the inconvinience to remember complex passwords is real. This often leads to frustration and detrimental practices, like writing passwords down or using simple variations that are easy to guess.
- Management overhead – organizations frequently bear the brunt of high IT support costs related to password resets, account lockouts, and recovery processes, which can drain resources from more critical business functions.
What your organisation gain from going passwordless?
- Enhanced security – by eliminating traditional authentication, passwordless methods dramatically reduce the risk of breaches tied to stolen or compromised credentials. Utilizing biometrics or security token offers a significantly more secure authentication process.
- Improved user experience – the login experience becomes much more seamless, as users no longer need to manage or memorize passwords, thanks to the use of authenticators. This reduction in cognitive load leads to greater satisfaction and engagement.
- Cost efficiency – organizations can save substantially on IT support costs associated with password management, freeing up resources for other vital areas of the business.
Inteca case study
In the past we worked with a leading European Information Bureau and together we implemented a password-free access solution using Keycloak that directly addressed the unique challenges faced by the organization.
Challenges faced by our client
Our client was dealing with a multitude of issues, including an overwhelming number of password-related support requests, user dissatisfaction stemming from overly complex access code policies, and the imperative to comply with stringent security regulations like PSD2 and GDPR. These challenges not only hindered user satisfaction but also posed significant risks to data security and overall operational efficiency.
Implementation of Keycloak for seamless login
To overcome these hurdles, we turned to Keycloak for a keyless authentication solution. This approach utilized various credentialing methods, such as biometric verification and security keys, to ensure a seamless and secure login experience for users through authentication with Keycloak. By leveraging Keycloak’s user-friendly interface, we configured the system to simplify the authentication process, allowing users to access their accounts without the hassle of remembering complicated passphrases.
Results achieved
The results were nothing short of impressive. Our customer saw a 70% reduction in password-related support tickets, translating into significant cost savings in IT support. User satisfaction scores zoomed, with feedback indicating that the new verification method greatly enhanced their overall experience. This case study exemplifies how Inteca’s tailored solutions can drive efficiency, security, and user satisfaction in the realm of identity and access management.

Worth to remember
Adopting token-based authentication through Keycloak presents a suite of advantages for organizations looking to bolster security while enhancing user experience through passwordless authentication with WebAuthn. Here are the key takeaways:
- Enhanced security – passwordless solutions drastically reduce risks associated with phishing and passphrase reuse, safeguarding user accounts more effectively.
- Improved user experience – users benefit from a seamless login process, eliminating the need for complex access code management and increasing overall satisfaction and engagement.
- Cost savings – by decreasing password-related support requests, organizations can realize significant savings in IT resources, allowing those resources to be redirected towards more strategic initiatives.
- Compliance ready – keycloak’s passwordless capabilities are aligned with industry standards and regulations, including GDPR and PSD2, aiding organizations in their compliance efforts.
As you assess your organization’s security strategy, I encourage you to explore Keycloak as a robust option for implementing passwordless authentication. Its flexibility and comprehensive features can truly transform your identity and access management approach, making it a valuable investment for the future.
See why Keycloak may be the best choice for your passwordless login needs!