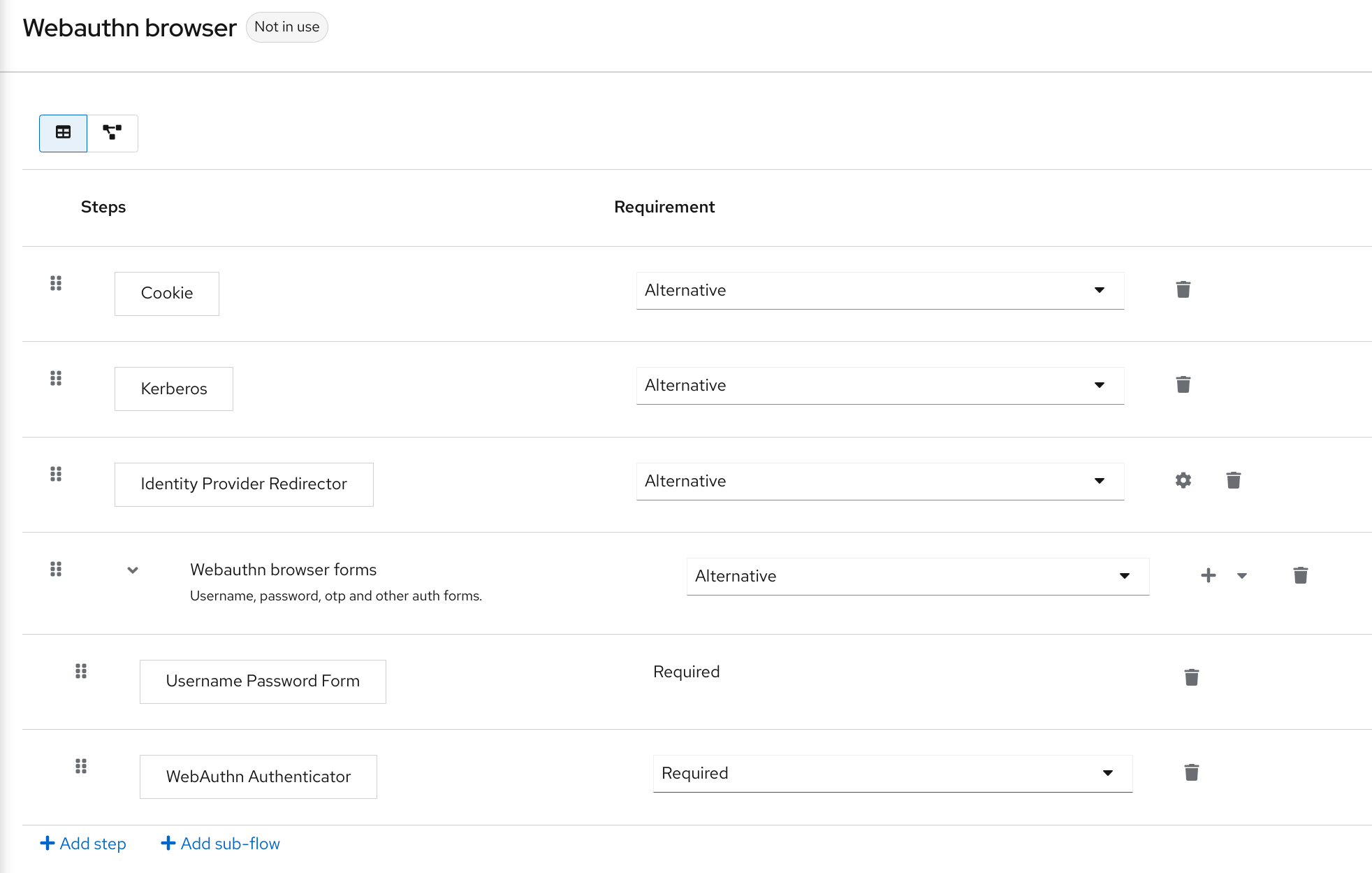
Passwordless authentication is becoming more important for organizations of all sizes, including medium-sized ones. Mainly because of its increased security and improved user experience. While working at Inteca, I’ve seen the growing necessity for stronger authentication methods with constantly new cyber threats. My prediction is that shortly, passwordless authentication will be a must for any organization. We will focus on Passkeys and WebAuthn. Those are relatively recent developments in the field of authentication, designed to improve security and user experience by moving away from traditional passwords and implementing passkey authentication.
Why do “old” methods are no longer enough?
These well-known access control system have served us for years. Still, they come with their own challenges. One of the challenges is user fatigue. I’ve observed how remembering complicated passwords and juggling multiple authentication factors can overwhelm users, often leading them to rely on unsafe password practices. Secondly, vulnerability. It’s clear that traditional methods are just too open to attacks like phishing, credential theft, and breaches, which significantly elevate the risk of unauthorized access to sensitive data.
The call for innovative solutions—like passkeys work by utilizing a public-private key system to enhance security. and WebAuthn—is growing stronger. These cutting-edge methods not only strengthen security but also aim to streamline the user experience, facilitating the way for a much-needed transformation in how we handle authentication.
Image source: keycloak.org
Why do we need stronger authentication methods?
The urgent need for stronger credentialing approach is evident. Cybercriminals are working on more and more sophisticated tactics, traditional methods like passwords and PINs simply aren’t working anymore. Here is why:
More cyber threats
Cyber threats, including credential theft, phishing attacks, and data breaches, are overgrown. It’s concerning how easily a simple username and password can become the weak point in our defenses, exposing sensitive data and putting organizations at risk.
While we may lean on familiar security protocol, they come with significant limitations:
- Credential theft – a major concern that passkeys aim to mitigate through advanced user verification. attackers are always looking for vulnerabilities to steal login details, allowing them to easily access the accounts.
- Phishing attacks – these manipulative tactics fool users into disclosing their personal information, often resulting in serious breaches.
- Data breaches – high-profile data leaks remind us that no organization is safe, leading to the exposure of millions of user credentials.
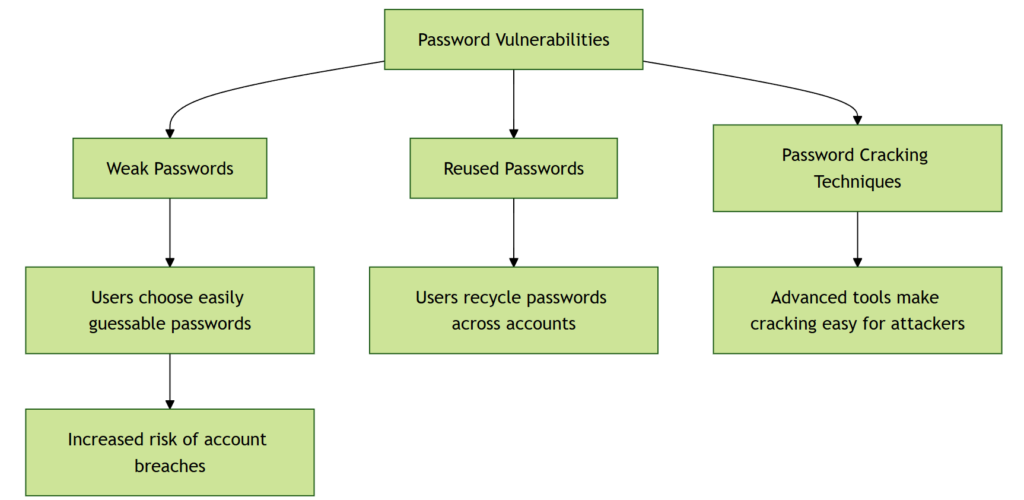
Password vulnerabilities
In truth, passwords aren’t as secure as we once believed:
– Weak passwords – it is not a surprise that most of the users choose basic, easily-guessable passwords that are a recipe for disaster.
– Reused passwords – it’s all too common for users to recycle passwords across different accounts, heightening risk.
– Password cracking techniques – with advanced tools available, cracking passwords has become alarmingly easy for attackers.
End-user experience matters
Let’s not forget that user experience plays a crucial role in authentication. Bulky, complicated processes can lead to frustration, pushing users towards insecure practices. We need solutions that strike a balance between robust security and seamless usability.
The truth is that:
- Users do not need to remember complex passwords
- We need faster and more streamlined login experiences
- Key consideration is to reduced friction in the login process
Regulatory compliance matters
On top of that, regulatory changes are prompting organizations to adopt stronger authorization measures. Compliance requirements are becoming stricter, pushing for enhanced security protocols to safeguard sensitive data and mitigate potential legal repercussions.
The shift towards advanced methods like passkeys and WebAuthn isn’t merely a trend; it’s essential for navigating today’s complex security landscape without using traditional passwords. By tackling these vulnerabilities head-on, we can significantly strengthen our digital defenses.
Image source: keycloak.org
Industry adoption of passwordless authenitcation
If the above examples are not enough to convince you that PA is a must, lets see why others adopt to this technology. A standout moment occurred in 2013 when Google transitioned to a passwordless system for its internal processes. This move showcased that passwordless environments were not just a pipe dream but a practical reality, setting a strong example for other companies.
We see a noticeable trend in the acceptance of passwordless technologies across various sectors. Businesses finally recognizing that the clock has run out on traditional methods.
Why do companies switch to passwordless?
- Growing security concerns – with cyber threats becoming more sophisticated, companies are feeling the pressure to implement stronger authentication measures to protect sensitive information.
- User experience – companies are shifting towards simpler, frictionless identity validation method, which is vital for keeping users engaged and satisfied.
- Regulatory compliance – as regulations tighten, businesses are compelled to adopt advanced authentication solutions to meet heightened security standards.
The login without password market is predicted to skyrocket to $86.35 billion by 2033 1. This forecast signals a robust trend towards widespread adoption, especially among sectors like finance, e-commerce, and technology. These industries facilitating the way, signaling not only a commitment to strengthened security but also a response to evolving user expectations for easy digital experiences.
Interested in Keycloak Managed Service?
In nutshell, the transition towards token-based authentication is an essential evolution in our ongoing battle against cyber threats. As more organizations embrace this innovative approach, the digital security landscape is poised for significant enhancement.
What exactly is FIDO2, WebAuthn and passkeys?
- FIDO2 provides the underlying framework for secure verification without passwords.
- WebAuthn is the browser API that lets websites communicate with FIDO2 authenticators.
- Passkeys are a specific user-friendly implementation of passwordless authentication using WebAuthn and FIDO2.
FIDO2 standard definition
FIDO2 is an identification protocol developed by the Fast Identity Online (FIDO) Alliance. It is a widely available phishing-resistant method. It is an umbrella term that includes the WebAuthn standard and enables no-password authentication using public-key cryptography. This standard plays a key role in encouraging the adoption of passkeys. It ensures that these validation methods are not only secure but also work across various platforms and devices.
This promotes a consistent and reliable customer experience, making it easier for users to embrace this new technology. FIDO2 contains the WebAuthn standard, which is the web API that enables websites to access FIDO2 authenticators
How FIDO2 works:
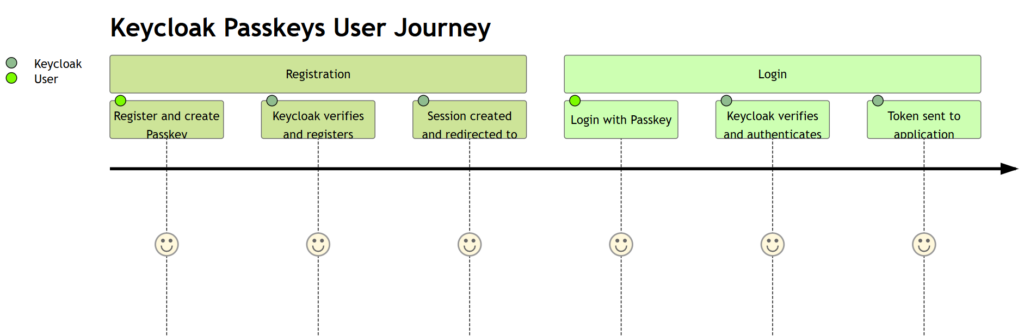
- During registration, the user’s device generates a new key pair, critical for implementing the client to authenticator protocol. The private key is kept on the device, stored securely, while the public key is sent to the service provider (also known as a Relying Party) using the client to authenticator protocol.
- During authentication, the service provider challenges the user’s device, which signs the challenge with the private key. The service provider then verifies the signature using the stored public key
- This process allows for secure verification without the use of passwords or shared secrets
- When a malicious actor tricks a user into logging into a fake website, the FIDO protocol blocks the attempt.
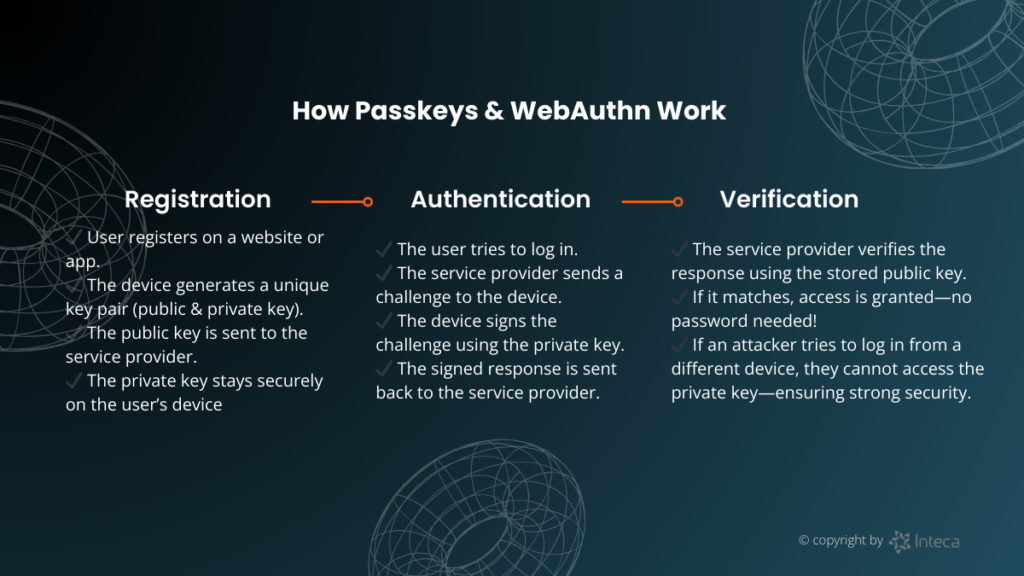
What is WebAuthn technology?
WebAuthn, or Web Authentication API, stands out as a game-changing open standard developed by the World Wide Web Consortium (W3C) in partnership with the FIDO Alliance, alongside renowned tech giants like Google, Microsoft, Apple, and Mozilla. This protocol reshapes user authorization , allowing for passwordless methods that incorporate biometrics or device authenticators, ultimately enhancing both security and the user interface by using passkeys.
WebAuthn in a nutshell:
- Web Authentication (WebAuthn) is a web protocol designed to provide secure authentication across multiple services
- It allows users to authenticate without passwords using various authenticators like fingerprint readers or security keys
- WebAuthn uses public-key cryptography, where a private key is stored securely on the user’s device and a public key is registered with the service provider
- Keycloak supports WebAuthn and can act as a Relying Party (RP), which facilitates passkey registration and validation
- WebAuthn can be used for password-free authentication , allowing users with WebAuthn credentials to authenticate without a password. It can also be used as a second factor in multi-factor authentication
The rise of passkeys
A passkey is basically a cryptographic key that replaces the need for a password in the authentication process. Instead of something a user knows, passkeys rely on something a user possesses, making them significantly less weak to common threats like phishing and credential theft.
Key points about passkey:
- Passkeys are a type of passwordless authentication techniques that use public-key cryptography to verify a user’s identity.
- Passkeys are based on the WebAuthn standard, part of the FIDO2 project, enhances security through user verification.
- They are designed to be highly resistant to phishing and credential-stuffing attacks because they do not involve passwords.
- A private key is stored securely on the user’s device, and a public key is registered with the service provider via the WebAuthn API.
- Passkeys offer cross-platform compatibility, allowing users to create a passkey on one device and use it on others.
- Keycloak provides preview support for passkeys, allowing users to register and authenticate with both synced and device-bound passkeys.
Biometric authentication supports passkeys
What’s even more exciting is the integration of biometric validation technologies—think fingerprints or facial recognition. These methods support the security of passkeys by requiring a biometric check to unlock the private key, ensuring that only the right users can access sensitive information.
Challenges with passkeys
Yet, the journey towards widespread passkey adoption isn’t without its hurdles, particularly in user verification across devices. Challenges like device loss if a user misplaces their device, accessing their accounts can become tricky. Implementing solutions like backup codes or alternative recovery options is crucial to address this risk. User engagement by encouraging users to transition to passkeys requires effort. Organizations should invest in educational campaigns to highlight the advantages of moving away from traditional methods.
Key takeaways
Reflecting on our journey toward stronger verification, the shift to passkeys and WebAuthn emerges as a crucial evolution in enhancing both security and interface experience. Here are the key takeaways:
- Traditional authentication methods like passwords are increasingly falling short due to user fatigue and vulnerabilities—this is where innovative solutions like passkeys come into play.
- With the use of cryptographic keys, passkeys not only mitigate risks from phishing and credential theft but also bolster the protection of sensitive data.
- Passkeys simplify the login process, enabling seamless, one-step verifications that enhance user satisfaction and engagement while keeping security robust, as they are stored on your device.
- Adopting passkeys and WebAuthn can aid organizations in meeting increasingly stringent regulatory standards, contributing to stronger data protection measures.
- The trend towards password-free authentication is gaining momentum, with industry projections suggesting that the market could surge to $86.35 billion by 2033.
By embracing these emerging technologies, we not only strengthen our defenses against evolving cyber threats but also create engaging user experiences vital for success in today’s digital landscape.
Sources:
See why Keycloak may be the best choice for your passwordless login needs!