Enterprise Keycloak Consulting Services: Architecture, Integration & Custom Deployments
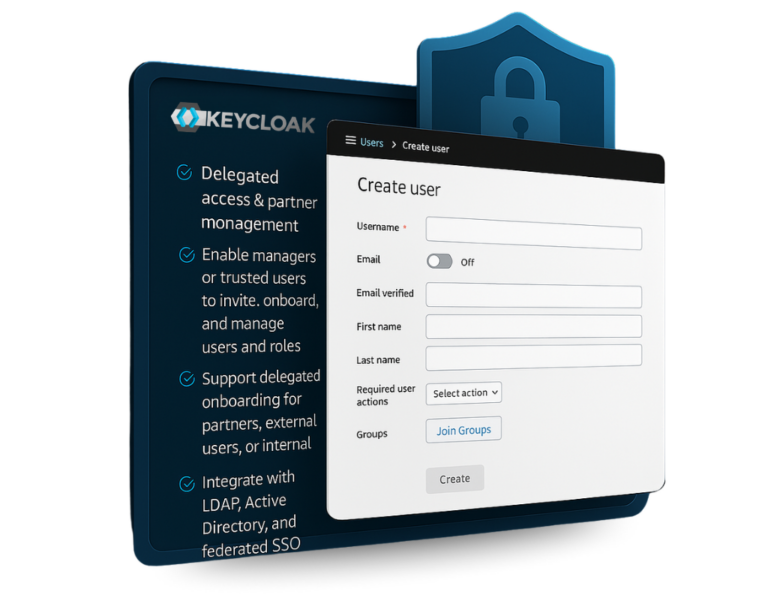
Why enterprises need specialized Keycloak consulting Modern enterprises face a dual challenge: navigating complex IT ecosystems while securing user and service identities. For organizations operating across legacy environments, cloud platforms, and microservices, Identity and Access Management (IAM) becomes a high-stakes endeavor. While Keycloak offers powerful, open-source IAM capabilities, unlocking its full potential requires deep expertise…