Passwordless Authentication for Enterprises
Faster authentication. No passwords. No phishing risks.
Let’s talk about your project
What is Passwordless Authentication?
Passwordless authentication eliminates passwords entirely, replacing them with biometrics, security keys, or cryptographic tokens. This enhances security, reduces IT costs, and improves compliance.
No need for passwords
Eliminate the need for passwords and reduce attack vectors.
Enhanced user experience
Improve user experience with biometric authentication methods such as passkeys, fingerprint scanning, and facial recognition.
Reduced IT costs
Lower IT costs by eliminating password resets and help desk requests.
Compliance & industry standards
Align with Zero Trust Security, FIDO passkeys, and certificate-based authentication (cert-based authentication) standards.
Reduce your risk today!
Schedule a consultation to implement passwordless solutions in your organization.
How enterprise passwordless authentication works?
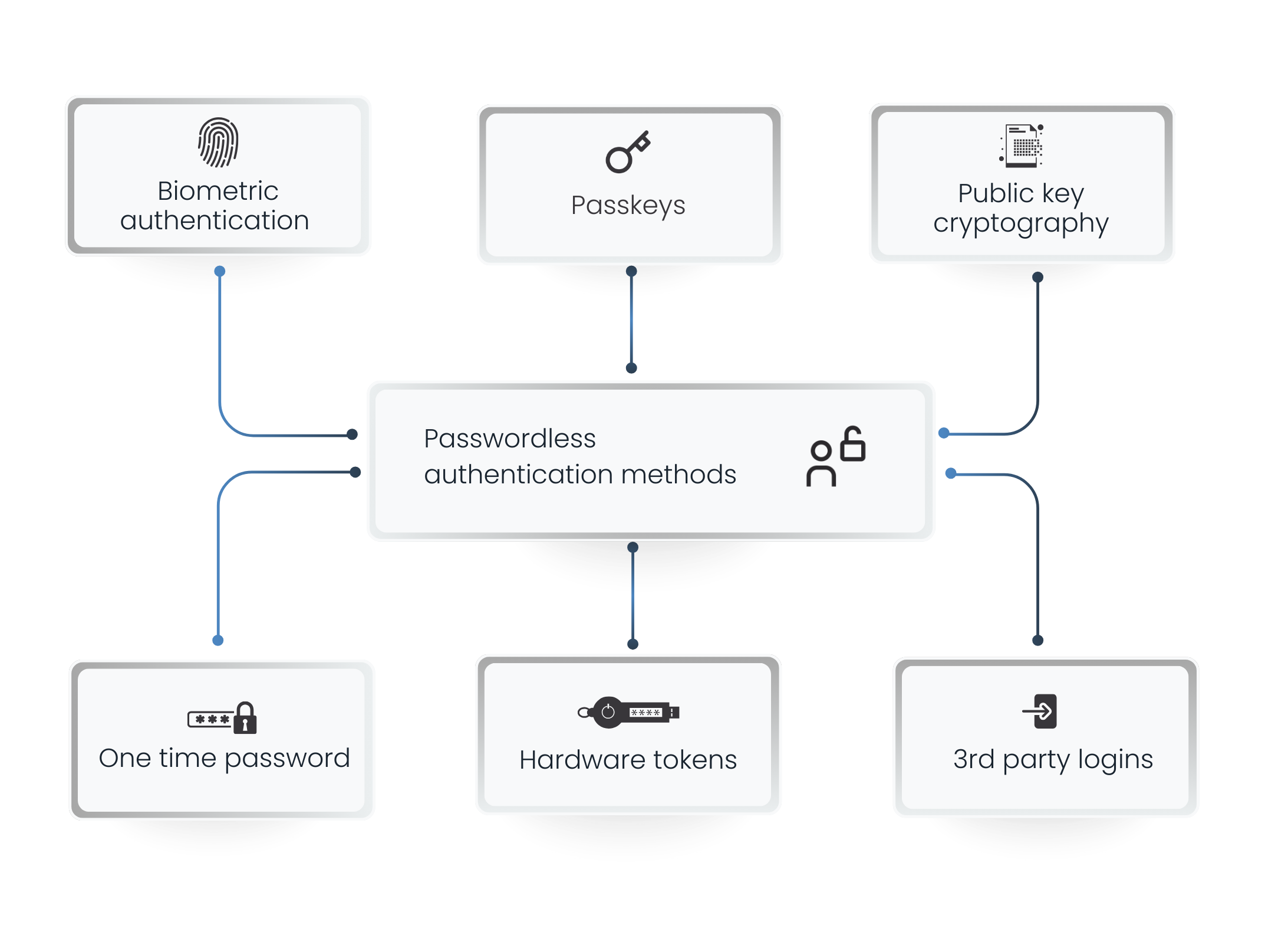
Passwordless authentication methods
- Biometric Authentication Methods – Use fingerprint scanning, facial recognition, or biometric records for seamless login.
- Passkeys & Public-Key Cryptography – Secure authentication using FIDO keys, passkeys vs passwords for security, and WebAuthn.
- Magic Links & OTPs – Authenticate via email, SMS, or Google Magic Link for frictionless access.
- Hardware Tokens & Smart Cards – Cert-based MFA using certificate-based authentication for enterprises.
- Third-Party Logins – Authenticate using Google, Apple, Microsoft for convenience and security.
Scalability & Integration
Passwordless authentication scales across enterprise environments, including payment systems.
- Enterprise-Ready Authentication – Works with IAM & client certificate authentication.
- Multi-Tenant Scalability – Scales authentication for large organizations and passwordless authentication payment solutions.
- Seamless Integration – Works with AWS, Azure, Kubernetes, private clouds.
- Flexible Authentication Flows – Build different passwordless MFA methods per user role.
- Zero Trust Security Model – Authenticate using multi-layer security and certificate authentication.
Advanced security mechanisms
Keycloak passwordless authentication ensures multi-layered security:
- Passwordless MFA – Adds extra security layers with biometrics, OTPs, and passkeys.
- Authorization Methods & RBAC – Certificate authentication methods for structured security policies.
- Risk-Based Authentication – Adjusts security levels based on biometric records and behavioral patterns.
- Adaptive Authentication – Authenticate using client certificate authentication and other MFA methods.
- Zero Trust Security – Every access attempt is verified with no implicit trust.
Keycloak framework
- Single Sign-On (SSO) – Seamless access to multiple applications with one login.
- Keycloak Double Authentication – Supports cert-based authentication and passwordless authentication solutions.
- Google Authenticator Keycloak – Secure authentication using FIDO keys and Google Magic Link.
- Role-Based Access Control (RBAC & ABAC) – Customize passwordless solutions.
- Custom Authentication Flows – Build adaptive authentication options tailored to business needs.
Enterprise identity security in numbers
50%
IT help desk requests
50% of IT help desk requests are related to password resets, increasing operational costs.
Forrester Research
$5.2 MM
per year
$5.2 million per year – The average cost of password resets for a mid-sized company.
30%
reduction in cyberattack risk
30% reduction in cyberattack risk with passwordless authentication compared to traditional MFA.
FIDO Alliance
We are the right partner for SSO & IAM

Enterprise-Grade security & compliance
We specialize in passwordless MFA, certificate authentication, and biometric authentication methods.

Offload the burden of security management
We handle deployment and maintenance, so your IT team can focus on what matters most.
Continuous optimization & 24/7 support
Ongoing performance monitoring and compliance tuning for passwordless authentication solutions.

Scalability without limits
Our passwordless authentication methods scale with your organization’s needs.
Need expert support for customer and workforce identity management?
Contact us today to learn how we cover everything – from architecture design to deployment and 24/7 maintenance







