Adaptive Multi-Factor Authentication (MFA) is a scalable policy that improves organizational security by assessing potential risks during every login transaction and prompting users for additional verification if necessary. This method customizes its requirements based on real-time risk assessments, reducing unauthorized access risks and improving user experience. Adaptive MFA focuses on enhancing security and a better user experience, implementing stricter authorization measures only when necessary, reducing unnecessary hurdles, and encouraging user participation in security practices. It is a pivotal strategy in modern security frameworks.
In this guide we will go through key aspects fo MFA technology.
What is MFA?
Multi-Factor Authentication (MFA) is a security method that requires users to provide two or more types of verification before they can access an account or system using adaptive identification protocols. It moves beyond simple password protection by combining different authentication factors:
-
Something you know – e.g., a password or PIN
-
Something you have – e.g., a phone, smart card, or hardware token
-
Something you are – e.g., biometric data like a fingerprint or facial recognition
This layered approach makes it significantly more difficult for unauthorized users to gain access, even if one factor (like a password) is compromised.
Why MFA matters?
MFA has become a fundamental part of modern cybersecurity strategy. It helps organizations:
-
Improve overall security posture
-
Prevent credential theft and account takeovers
-
Ensure compliance with regulations like GDPR, HIPAA, and PSD2
-
Promote good security habits among users
Single-Factor vs Multi-Factor Authentication
| Single-Factor | Multi-Factor | |
|---|---|---|
| Security Level | Low | High |
| User Convenience | High | Moderate |
| Implementation Cost | Low | Moderate to High |
| Regulatory Compliance | Often not sufficient | Often meets requirements |
| Risk of Credential Theft | High | Low |
Traditional MFA is not enough anymore. Upgrade to Adaptive MFA for smarter, real-time protection that scales with your business.
What is adaptive MFA?
Adaptive Multi-Factor Authentication (A-MFA) is an advanced form of MFA that adjusts validation requirements based on real-time contextual signals. Unlike traditional MFA, which applies the same steps to every user regardless of circumstance, A-MFA dynamically tailors the process depending on factors such as user behavior, device status, location, and time of access. This approach increases security while reducing friction for low-risk, legitimate users.
By evaluating the context of each login attempt, Adaptive MFA ensures that users face additional confirmation steps only when there is a heightened risk, providing a more efficient and secure experience.
Traditional MFA vs Adaptive MFA
| Feature | Traditional MFA | Adaptive MFA |
|---|---|---|
| Authentication Steps | Fixed (e.g., password + SMS) | Dynamic based on assessed risk |
| Risk Assessment | Static or rule-based | Real-time and context-driven |
| User Experience | Often repetitive and rigid | Streamlined and flexible |
| Flexibility | One-size-fits-all | Adjusted to each user or scenario |
| Security Level | Consistent across all attempts | Varies depending on context and behavior |
| Implementation Complexity | Less complex | Requires more planning and contextual integration |
| Cost | Lower initial investment | Higher due to advanced features and tools |
How adaptive MFA works?
Adaptive MFA is built on a series of intelligent components that continuously assess and respond to conditional risk signals. Instead of applying the same verification requirements to every user, A-MFA adapts based on a real-time understanding of user behavior, environment, and device posture. Here’s how it operates:
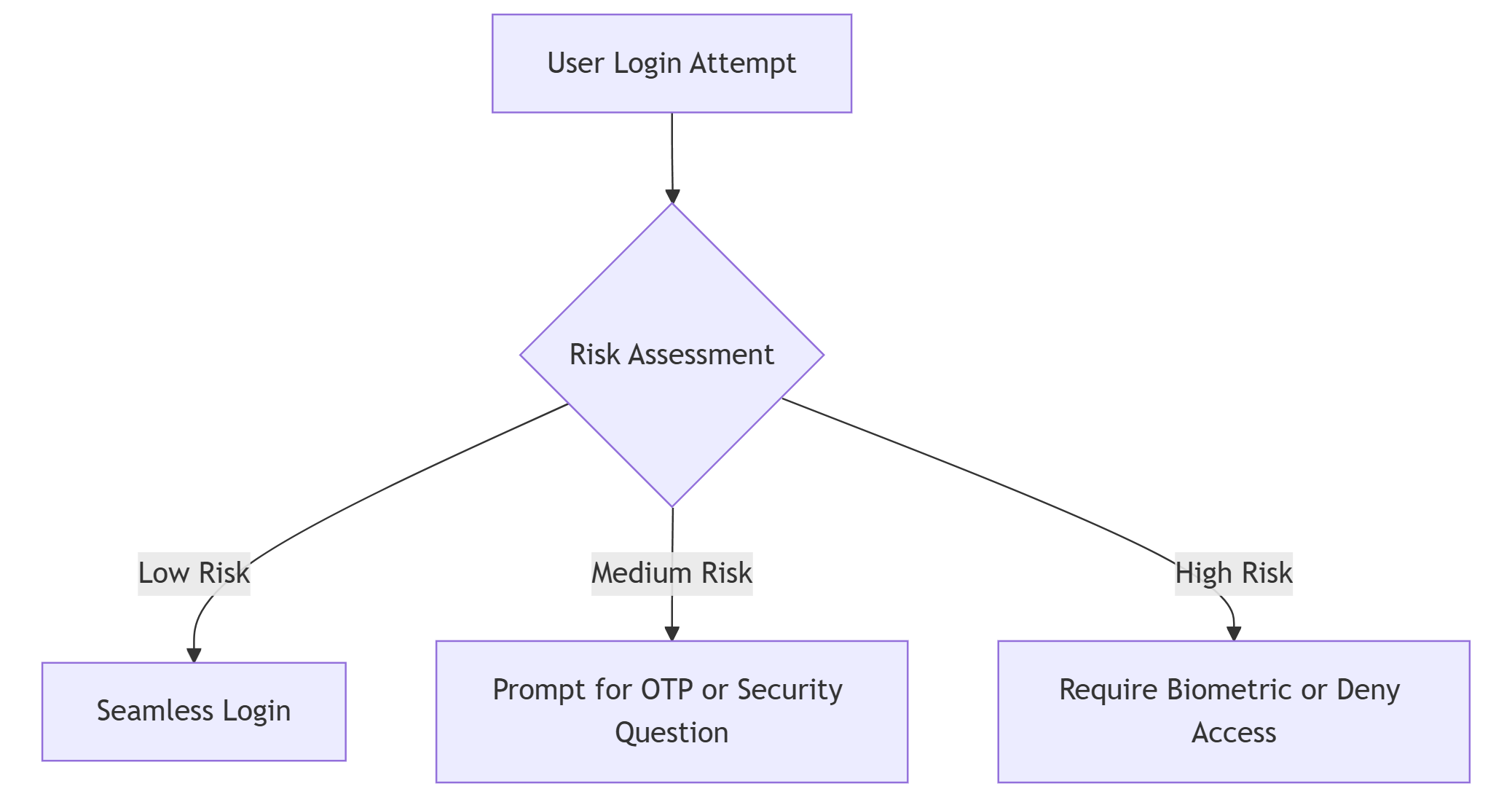
Risk-Based Authentication
Each login attempt is evaluated and assigned a dynamic risk score based on various attributes. Low-risk scenarios may require minimal verification, while high-risk attempts can trigger step-up authentication.
To further strengthen this process, users can be segmented by risk level—allowing more stringent confirmation for high-risk roles or behaviors while maintaining streamlined access for known, low-risk users.
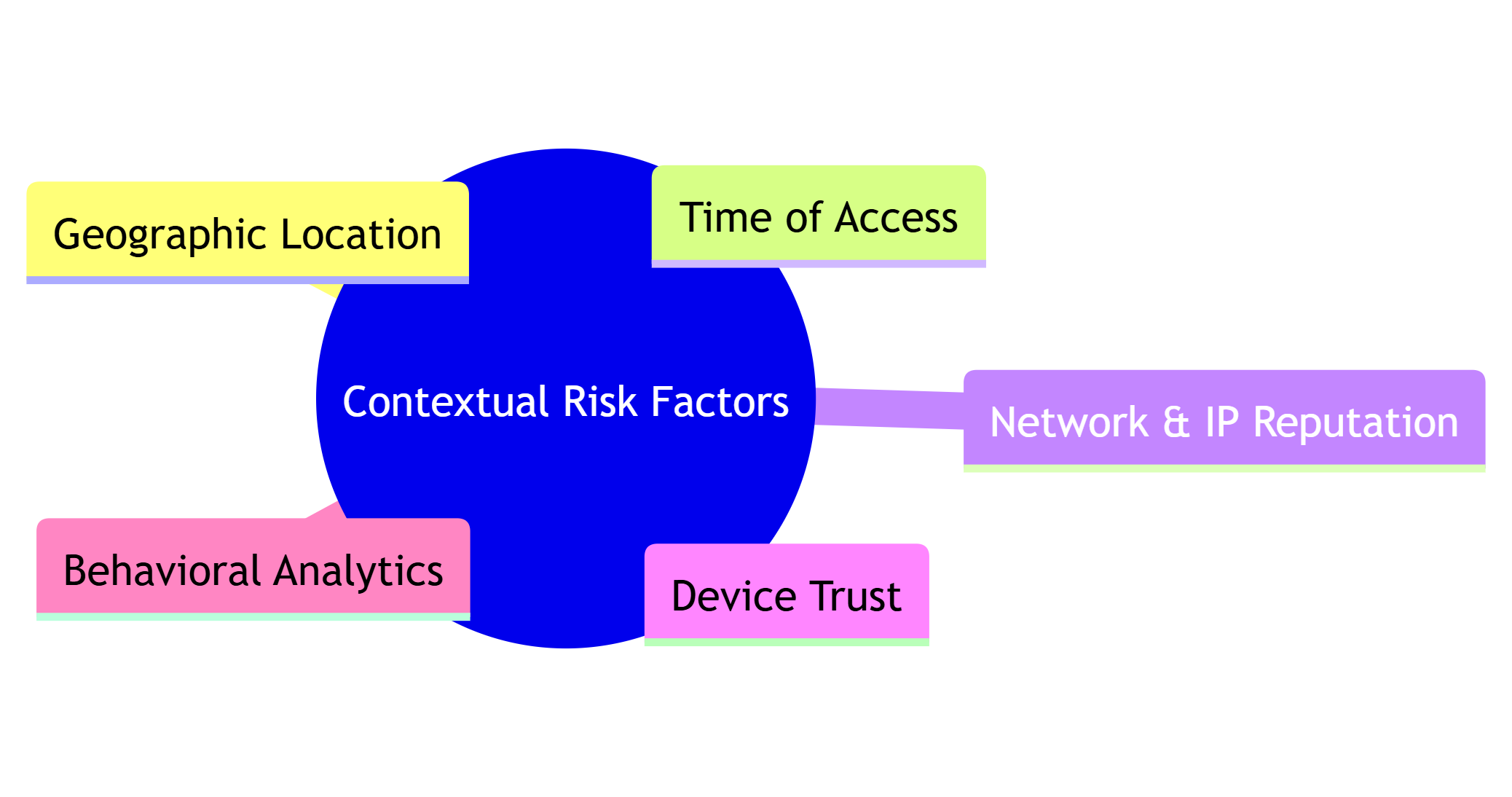
Context analysis
A-MFA considers the context in which access is requested. This includes:
-
Geographic location (e.g., logging in from a new country) is one of the risk factors that adaptive authentication considers.
-
Time of access (e.g., late-night logins outside normal patterns)
-
Network and IP reputation
-
Device fingerprinting and trust
Behavioral analytics
The system continuously observes and learns from a user’s behavior over time, including typing cadence, mouse movements, and login frequency. It builds a behavioral baseline unique to each user, helping detect deviations that may indicate unauthorized access attempts. These user profiles evolve through adaptive learning, enabling faster and more accurate threat detection.

With Adaptive MFA, you get airtight protection—without the friction. Dynamic authentication adapts to risk, not routine.
Device health assessment
A-MFA evaluates the security posture of the device attempting access. If a device lacks encryption, runs outdated software, or lacks endpoint protection, it may be flagged as risky—triggering additional identification steps or denying access altogether.
Location signals
Location data, including IP address, is a core cconditional input for adaptive verification . Unfamiliar or high-risk geographic access points raise suspicion and may initiate additional verification challenges, such as one-time passcodes, security questions, or biometric checks.
Types of Multi-Factor Authentication
Traditional Multi-Factor Authentication (MFA) typically combines two or more static factors to verify a user’s identity. These include:
-
Knowledge factors (e.g., passwords or PINs)
-
Possession factors (e.g., SMS codes, mobile apps, hardware tokens)
-
Inherence factors (e.g., fingerprints or facial recognition)
While effective, these methods are applied uniformly to all users and login attempts, regardless of context. Adaptive MFA builds on these foundational elements by layering in dynamic risk evaluation, allowing the identification process to shift based on behavior, environment, and perceived threat level.
By integrating traditional factors with contextual and behavioral intelligence, Adaptive MFA delivers a more secure and user-friendly approach to identity validation.
| Method | Description | Pros | Cons |
|---|---|---|---|
| SMS-based codes | Users receive a one-time code via SMS. | Easy to implement and user-friendly. | Vulnerable to SIM swapping. |
| Email codes | A verification code sent to the user’s email. | Common and familiar. | Email accounts can be compromised. |
| Hardware tokens | Physical devices generate one-time codes. | High security and offline capabilities. | Costly and may be lost or damaged. |
Benefits of choosing adaptive MFA
- Enhanced Security Posture – Adaptive MFA significantly strengthens an organization’s defense against unauthorized access by responding to threats in real time. Instead of applying static rules, it dynamically adjusts confirmation based on contextual signals like user behavior, location, and device health. This proactive approach makes it harder for attackers to exploit stolen credentials or bypass security protocols.
- Granular policy control – Adaptive MFA allows organizations to implement highly customizable authentication policies. Security requirements can vary based on user roles, departments, access levels, device trust, and real-time risk signals. This granularity helps enforce stricter controls where needed—without overburdening all users with unnecessary steps.
- Scalable and future-proof – Whether supporting dozens or thousands of users, Adaptive MFA scales easily. Cloud-native architectures and machine learning integration enable real-time decision-making at scale, while policy engines allow organizations to evolve security practices without rebuilding the entire authentication framework.
-
Improved user experience – one of the most valuable advantages of Adaptive MFA is its ability to reduce friction for legitimate users. By evaluating risk in real time, the system can streamline access during low-risk scenarios while only prompting for further authentication when truly necessary. This balance between security and usability leads to better user satisfaction and productivity.
Adaptive MFA also supports a user-centric design philosophy. Rather than forcing the same experience on every user, it adapts to the individual’s behavior, preferences, and environment.
Key user-focused capabilities include:
-
Personalized user profiles – Adaptive MFA builds and maintains detailed user profiles based on login frequency, device usage, and location trends. These profiles help the system determine what is “normal” for each user and only intervene when something deviates from the expected pattern.
-
Simplicity and transparency – identification flows are designed to be intuitive and minimally disruptive. Users can be guided through steps with clear messaging and minimal cognitive load.
-
Customization Options: Organizations can allow users to select preferred authentication methods (e.g., biometrics vs. OTP), increasing comfort and engagement without compromising security.
-
Real-Time Feedback: Informing users why an extra step is required (e.g., “Unrecognized device detected”) builds trust and transparency in the authentication process.
-
Advanced techniques in multi-factor authentication
Adaptive MFA relies heavily on advanced techniques that go beyond static credentials and basic verification. By incorporating behavioral intelligence and anomaly detection, modern identification systems can proactively identify threats and respond in real time.
- Behavioral analytics monitors user activity patterns—such as typing speed, navigation habits, and login frequency—to establish a behavioral baseline. If a user’s behavior deviates significantly from their normal profile, the system can flag the session as high-risk and trigger additional verification steps.
- Through continuous machine learning, Adaptive MFA systems learn how each user typically interacts with systems and applications. Over time, they can accurately predict whether a login attempt aligns with historical behavior. This allows the system to distinguish between legitimate users and potential attackers—even when credentials are correct.
-
Anomaly detection engines assess large volumes of confirmation data to identify unusual events, such as:
-
Logins from new geographies
-
Unusual times of access
-
Sudden spikes in access attempts
Rather than waiting for a rule to be triggered, the system reacts dynamically, adjusting identification requirements or denying access outright.
-
-
While traditional biometrics focus on physical traits like fingerprints or facial recognition, behavioral biometrics analyze how users interact with devices to enhance adaptive authentication. These include:
-
Keystroke dynamics
-
Mouse movement patterns
-

Block credential attacks, reduce user friction, and future-proof your access controls with adaptive, context-aware authentication.
Integration and implementation of MFA
Successfully deploying Adaptive MFA requires more than just choosing the right technology. Organizations must account for integration challenges, cost implications, scalability, and user privacy concerns to ensure long-term success.
Integration challenges with existing systems
Many organizations rely on legacy systems that were not designed for modern identity verification and authorization protocols, which can hinder the benefits of adaptive multifactor authorization. Integrating Adaptive MFA into these environments can be complex, especially when compatibility issues arise or when systems lack support for real-time conditional inputs.
To ease implementation:
-
Conduct a system audit to identify integration gaps
-
Use APIs and SDKs to bridge compatibility issues
-
Roll out A-MFA in phases to avoid operational disruption
-
Provide targeted training to reduce user resistance and help teams understand when and why adaptive prompts occur
Cost of implementation
Costs vary depending on organizational size, infrastructure complexity, and chosen solution.
Typical cost categories include:
-
Software licensing
-
Hardware tokens (if applicable)
-
Integration services
-
Ongoing support and training
While the upfront investment can be significant, the long-term cost of inaction—such as data breaches, compliance penalties, and user downtime—is far higher. Organizations should evaluate ROI not just in terms of cost reduction, but also in terms of risk mitigation and the benefits of adaptive authentication.
Scalability of authentication solutions
A-MFA is designed to grow with your organization. It supports:
-
Cloud-based expansion for distributed teams
-
Role-based access policies that adapt as team structures evolve
-
AI-driven automation for onboarding and access provisioning
However, AI introduces new challenges. Poorly tuned machine learning models or insufficient data can result in false positives, causing legitimate users to be flagged as suspicious due to risk factors associated with their IP address. Organizations should plan for ongoing model training, testing, and refinement to minimize disruptions.
Balancing security and user experience
Authorization shouldn’t stop at login. Continuous verification—assessing user activity, device health, and context throughout a session—is becoming a critical part of implementation.
Organizations should incorporate:
-
Session-level monitoring for behavioral anomalies
-
Adaptive responses based on evolving risk conditions
-
Real-time security triggers for access revocation or re-authentication
These adaptive security measures enhance both threat detection and user confidence, enabling a smarter, more resilient access strategy.
User training and adoption
A-MFA introduces a level of complexity that users may not be familiar with—particularly when validation challenges appear to be “invisible” or variable.
To build trust and drive adoption:
-
Offer training that explains how and why A-MFA responds to different scenarios
-
Emphasize the benefit to users: fewer interruptions when behavior is consistent, and added protection when it’s not
-
Address misconceptions about surveillance or overreach by reinforcing transparency and control
Privacy risks and AI limitations
Since Adaptive MFA relies on personal behavioral and situational data, it raises valid privacy concerns. Transparency is critical—users must understand what data is being collected and how it is protected.
Key mitigation strategies include:
-
Data minimization (collect only what’s necessary)
-
Encryption of telemetry and user behavior logs
-
Regular audits to ensure compliance with regulations like GDPR and HIPAA
-
Monitoring for adversarial attacks that attempt to manipulate AI-driven risk scoring
Real-world applications and use cases of adaptive MFA
Adaptive MFA proves its value in real-world scenarios where user behavior, risk, and context vary widely. Below are practical use cases where Adaptive MFA enhances security while maintaining usability across industries and environments.
Adaptive Multi-Factor Authentication for remote workers
Adaptive Multi-Factor Authentication (A-MFA) plays a crucial role in securing remote workforces, as more employees work from locations outside the standard office, providing a seamless confirmation experience. This method adjusts for each login by assessing factors like the user’s location, device condition, and network security.
For example, consider an employee attempting to access sensitive company data from a public Wi-Fi hotspot. In such a scenario, A-MFA prompts the user for extra verification steps, such as a one-time password (OTP) or biometric authentication. Conversely, if that same employee logs in from a secure corporate network using their company-issued device, A-MFA might require just a password. This customized risk assessment aligns security measures with real risks, ensuring effective protection without compromising user ease.
Use case – healthcare sector
Healthcare organizations must protect sensitive patient data and comply with regulations like HIPAA. Adaptive MFA strengthens security by enforcing real-time, context-aware verification when clinicians or patients access systems.
-
Patient portals: Adaptive MFA ensures that only authorized users access electronic health records.
-
Remote access: Doctors logging in from new locations or devices may be prompted for additional authentication through adaptive multifactor authentication.
-
Pharmacy access: Systems handling prescription requests verify user identity through risk-based policies.
Use case – financial institutions
Banks and fintech companies face ongoing threats of credential theft, fraud, and compliance violations. Adaptive MFA plays a crucial role in mitigating these risks.
-
Online and mobile banking: Extra authentication is required when customers perform high-risk actions like password changes or fund transfers.
-
Fraud detection is enhanced through the implementation of adaptive authentication solutions.: Unusual transactions or access attempts from unrecognized locations trigger step-up authentication.
-
Regulatory compliance: A-MFA helps institutions meet strict requirements like those enforced by the FFIEC and PSD2.
Step-Up Authentication Scenarios
Adaptive Multi-Factor Authentication (A-MFA) enhances security and improves user experience, as demonstrated by various clients I’ve worked with on identity and access management projects. Here are some practical examples that illustrate A-MFA in action:
1. Login from new devices
When a user accesses their account from a device not previously associated with them, A-MFA prompts enhanced verification —typically via a one-time passcode or biometric check.
2. Accessing sensitive data
Attempts to access highly sensitive resources such as financial records, personal data, or internal systems often trigger stricter authentication—like requiring a fingerprint scan or hardware token.
3. Unusual geographical locations
Access during nights, weekends, or outside standard business hours can raise risk flags. A-MFA responds with additional confirmation steps depending on the organization’s policies.
4. Non-working hours logins
A spike in failed login attempts may indicate a brute-force attack or credential stuffing. Adaptive MFA responds with temporary account lockouts or multi-factor challenges.
5. Consecutive failed login attempts
When multiple failed login attempts are detected from a single account, A-MFA takes action. It may lock the account temporarily or require stronger authentication for further attempts. This proactive response helps to prevent brute-force attacks, thereby enhancing overall security.
Adaptive MFA in Action – summary
| Scenario | A-MFA Response |
|---|---|
| New device | Prompt for OTP or biometric check |
| Accessing sensitive data | Require strong second factor (e.g., biometric) |
| Unusual geographic location | Push notification, security question, or deny |
| Non-working hours | Step-up authentication triggered |
| Multiple failed login attempts | Temporary lockout or escalate verification steps |
Key Takeaways
-
Adaptive MFA delivers dynamic, risk-based authentication tailored to each access attempt, enhancing both security and usability.
-
Real-time context and behavior analysis allow systems to intelligently assess threats and minimize unnecessaryauthorization friction.
-
Modern use cases across industries—from healthcare to finance—demonstrate the flexibility and necessity of Adaptive MFA.
-
Artificial intelligence (AI), biometrics, and passwordless technologies are rapidly shaping the next generation of authentication.
-
Successful implementation depends on thoughtful integration, user education, and a clear balance between protection and experience.
See why Keycloak may be the best choice for your authorisation needs