How to implement enterprise SSO with Keycloak: end-to-end guide
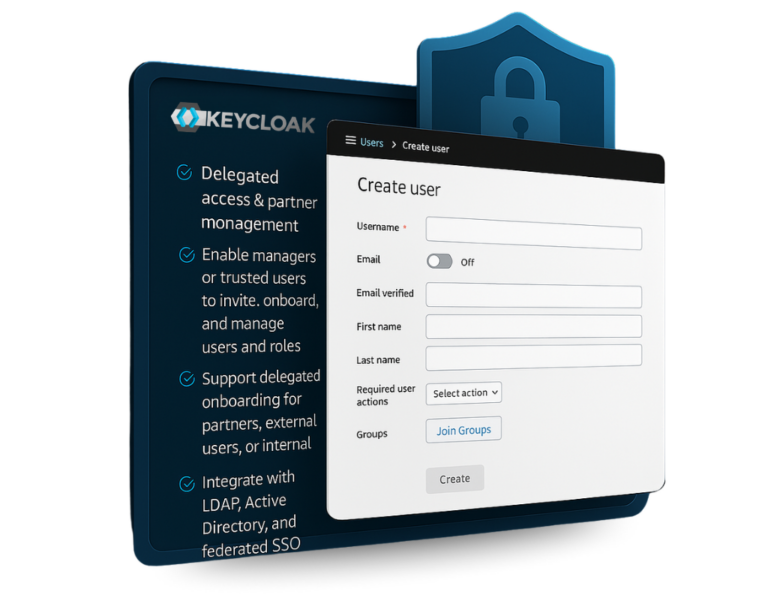
Introduction to enterprise single sign-on (SSO) implementation Enterprise environments demand secure, centralized access control. Implementing single sign-on (SSO) is a best practice for authentication and authorization across enterprise systems. It enables users to access multiple applications using a single set of credentials. Inteca offers end-to-end enterprise SSO solutions built on Keycloak, supporting SAML, OAuth2, and…